Exam Details
Exam Code
:ECSAv8Exam Name
:EC-Council Certified Security Analyst (ECSA) v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:200 Q&AsLast Updated
:Apr 09, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAv8 Questions & Answers
-
Question 1:
Which type of security policy applies to the below configuration?
i)Provides maximum security while allowing known, but necessary, dangers
ii)All services are blocked; nothing is allowed iii)Safe and necessary services are enabled individually iv)Non-essential services and procedures that cannot be made safe are NOT allowed v)Everything is logged
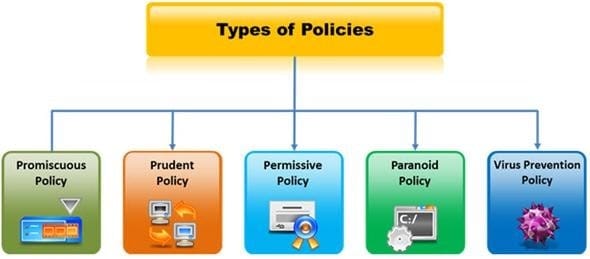
A. Paranoid Policy
B. Prudent Policy
C. Permissive Policy
D. Promiscuous Policy
-
Question 2:
Assessing a network from a hacker's point of view to discover the exploits and vulnerabilities that are accessible to the outside world is which sort of vulnerability assessment?
A. Network Assessments
B. Application Assessments
C. Wireless Network Assessments
D. External Assessment
-
Question 3:
Identify the data security measure which defines a principle or state that ensures that an action or transaction cannot be denied.
A. Availability
B. Integrity
C. Authorization
D. Non-Repudiation
-
Question 4:
One of the steps in information gathering is to run searches on a company using complex keywords in Google.
Which search keywords would you use in the Google search engine to find all the PowerPoint presentations containing information about a target company, ROCHESTON?
A. ROCHESTON fileformat:+ppt
B. ROCHESTON ppt:filestring
C. ROCHESTON filetype:ppt
D. ROCHESTON +ppt:filesearch
-
Question 5:
Which of the following acts related to information security in the US establish that the management of an organization is responsible for establishing and maintaining an adequate internal control structure and procedures for financial reporting?
A. USA Patriot Act 2001
B. Sarbanes-Oxley 2002
C. Gramm-Leach-Bliley Act (GLBA)
D. California SB 1386
-
Question 6:
During external penetration testing, which of the following techniques uses tools like Nmap to predict the sequence numbers generated by the targeted server and use this information to perform session hijacking techniques?
A. TCP Sequence Number Prediction
B. IPID State Number Prediction
C. TCP State Number Prediction
D. IPID Sequence Number Prediction
-
Question 7:
A directory traversal (or path traversal) consists in exploiting insufficient security validation/sanitization of user-supplied input file names, so that characters representing "traverse to parent directory" are passed through to the file APIs.
The goal of this attack is to order an application to access a computer file that is not intended to be accessible. This attack exploits a lack of security (the software is acting exactly as it is supposed to) as opposed to exploiting a bug in the code.
To perform a directory traversal attack, which sequence does a pen tester need to follow to manipulate variables of reference files?
A. dot-dot-slash (../) sequence
B. Denial-of-Service sequence
C. Brute force sequence
D. SQL Injection sequence
-
Question 8:
Which of the following shields Internet users from artificial DNS data, such as a deceptive or mischievous address instead of the genuine address that was requested?
A. DNSSEC
B. Firewall
C. Packet filtering
D. IPSec
-
Question 9:
A firewall protects networked computers from intentional hostile intrusion that could compromise confidentiality or result in data corruption or denial of service. It examines all traffic routed between the two networks to see if it meets certain criteria. If it does, it is routed between the networks, otherwise it is stopped.
Why is an appliance-based firewall is more secure than those implemented on top of the commercial operating system (Software based)?
A. Appliance based firewalls cannot be upgraded
B. Firewalls implemented on a hardware firewall are highly scalable
C. Hardware appliances does not suffer from security vulnerabilities associated with the underlying operating system
D. Operating system firewalls are highly configured
-
Question 10:
A firewall's decision to forward or reject traffic in network filtering is dependent upon which of the following?
A. Destination address
B. Port numbers
C. Source address
D. Protocol used
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAv8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.