Exam Details
Exam Code
:EX407Exam Name
:Red Hat Certified Specialist in Ansible AutomationCertification
:Red Hat CertificationsVendor
:Red HatTotal Questions
:124 Q&AsLast Updated
:Jun 26, 2025
Red Hat Red Hat Certifications EX407 Questions & Answers
-
Question 101:
Observe the details of the following dynamic inventory file. $ ls -l dynamic.py -rw-rw-r--. 1 user user 1928 Mar 30 08:21 dynamic.py Why will this inventory file cause the ansible command to fail?
A. Ansible cannot use python scripts as inventories.
B. The ansible user must own the file.
C. The file is not executable.
D. The ansible command will not fail using the noted file with the given details.
-
Question 102:
-
Question 103:
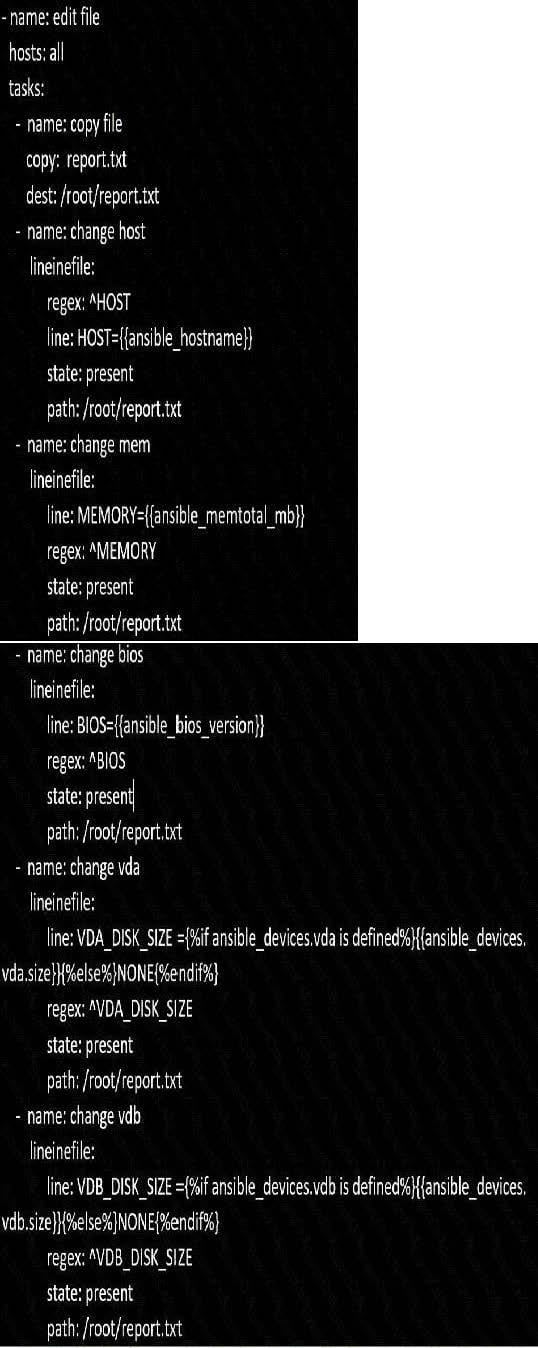
Create a file in /home/sandy/ansible/ called report.yml. Using this playbook, get a filecalled report.txt (make it look exactly as below). Copy this file over to all remote hosts at /root/report.txt. Then edit the lines in the file to provide the real information the of hosts. If a disk does not exist then write NONE.
report.txt
HOST=inventory hostname MEMORY=total memory in mb BIOS=bios version VDA_DISK_SIZE=disk size VDB_DISK_SIZE=disk size
-
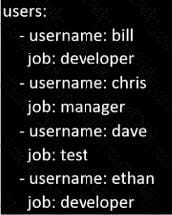
Question 104:
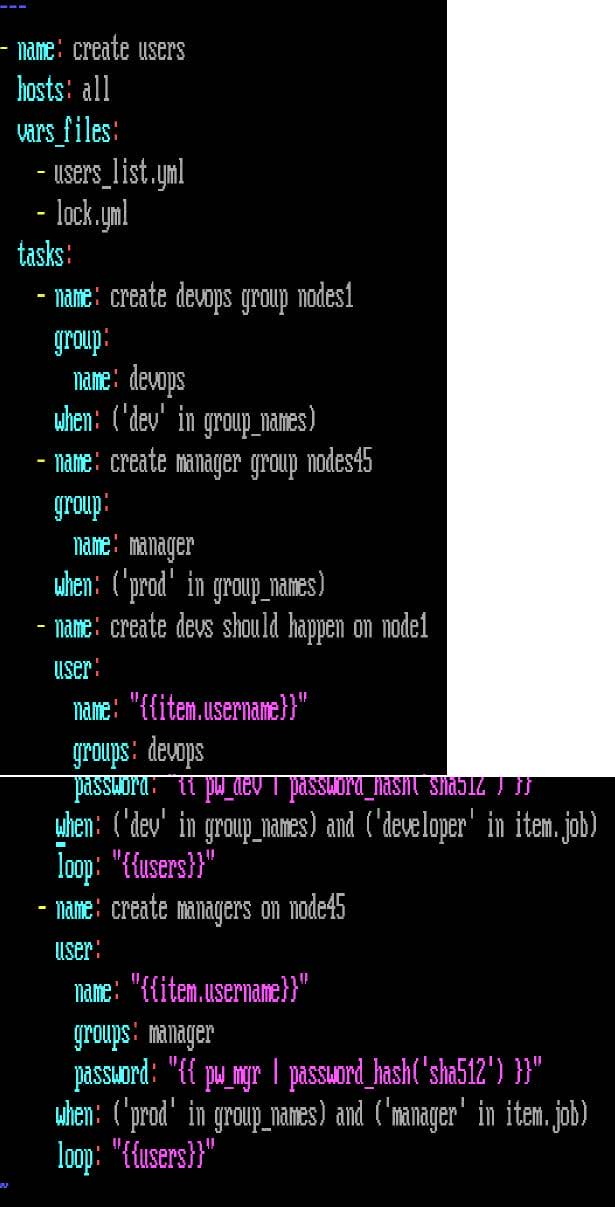
Create the users in the file usersjist.yml file provided. Do this in a playbook called users.yml located at /home/sandy/ansible. The passwords for these users should be set using the lock.yml file from TASK7. When running the playbook, the lock.yml file should be unlocked with secret.txt file from TASK 7.
All users with the job of 'developer' should be created on the dev hosts, add them to the group devops, their password should be set using the pw_dev variable. Likewise create users with the job of 'manager' on the proxy host and add the users to the group 'managers', their password should be set using the pw_mgr variable.
users_list.yml
-
Question 105:
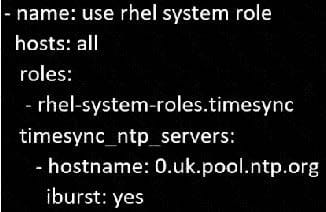
Create a playbook called timesvnc.yml in/home/sandy/ansible using rhel system role timesync. Set the time to use currently configured nip with the server 0.uk.pool.ntp.org. Enable burst. Do this on all hosts.
-
Question 106:
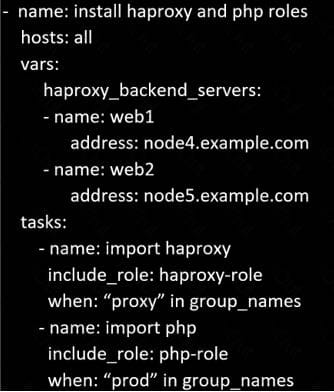
Create a file called requirements.yml /home/sandy/ansible/roles in a file called role.yml in /home/sandy/ansible/. The haproxy-role should be used on the proxy host. And when you curl http://node3.example.com it should display "Welcome tonode4.example.com" and when you curl again "Welcome tonode5.example.com"The php-role should be used on the prod host.
-
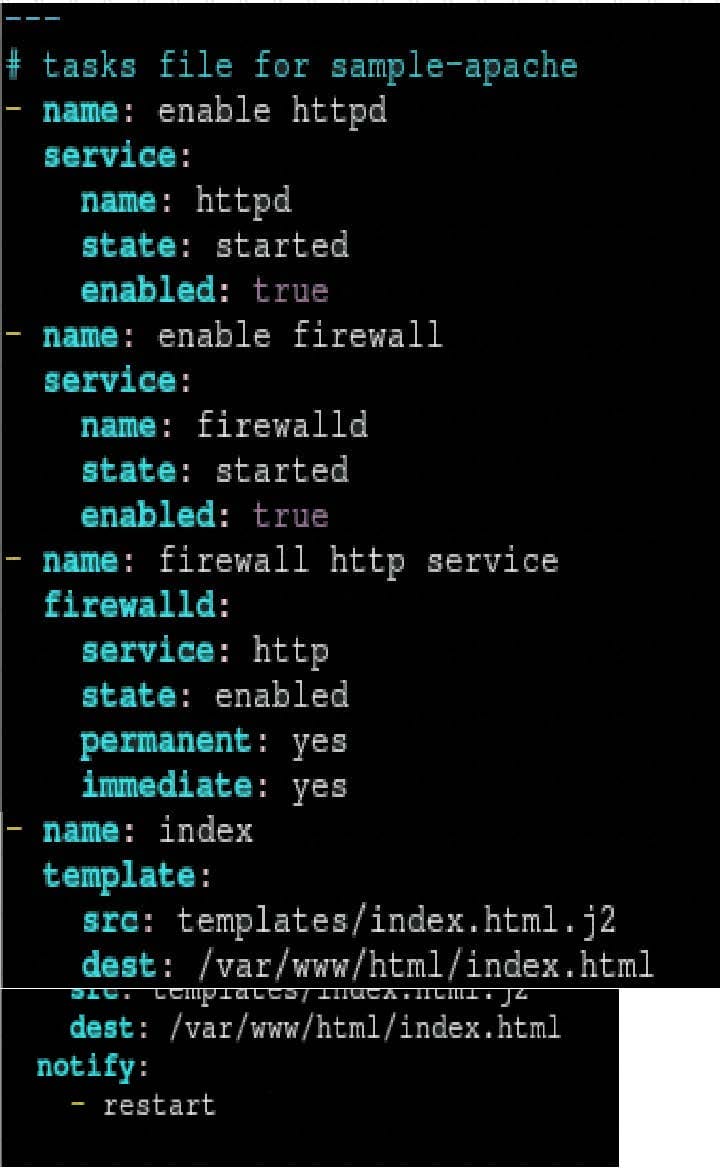
Question 107:
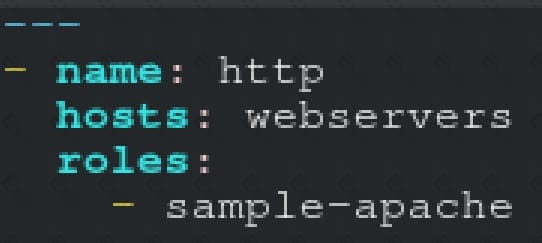
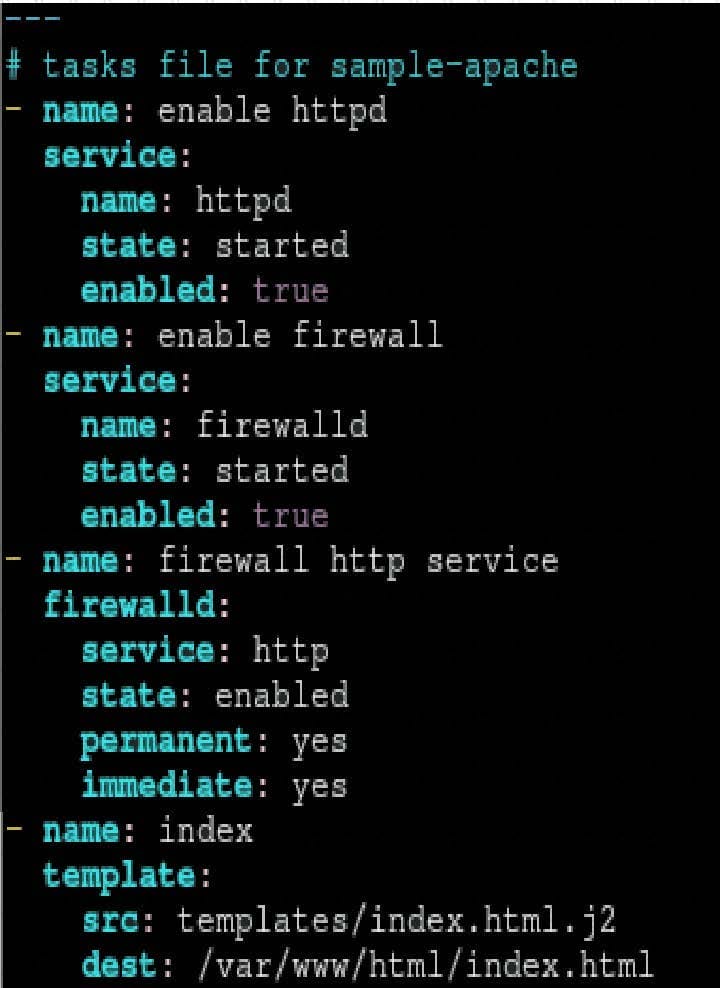
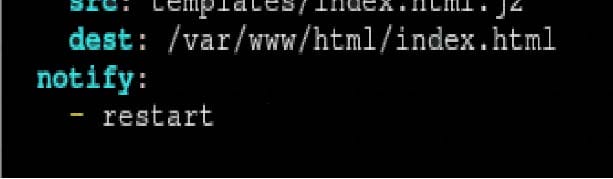
Create a role called sample-apache in /home/sandy/ansible/roles that enables and starts httpd, enables and starts the firewall and allows the webserver service. Create a templatecalled index.html.j2 which creates and serves a message from /var/www/html/index.html Whenever the content of the file changes, restart the webserver service.
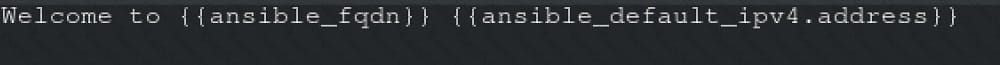
Welcome to [FQDN] on [IP]
Replace the FQDN with the fully qualified domain name and IP with theip address of the node using ansible facts. Lastly, create a playbook in /home/sandy/ansible/ called apache.yml and use the role to serve the index file on webserver hosts.
-
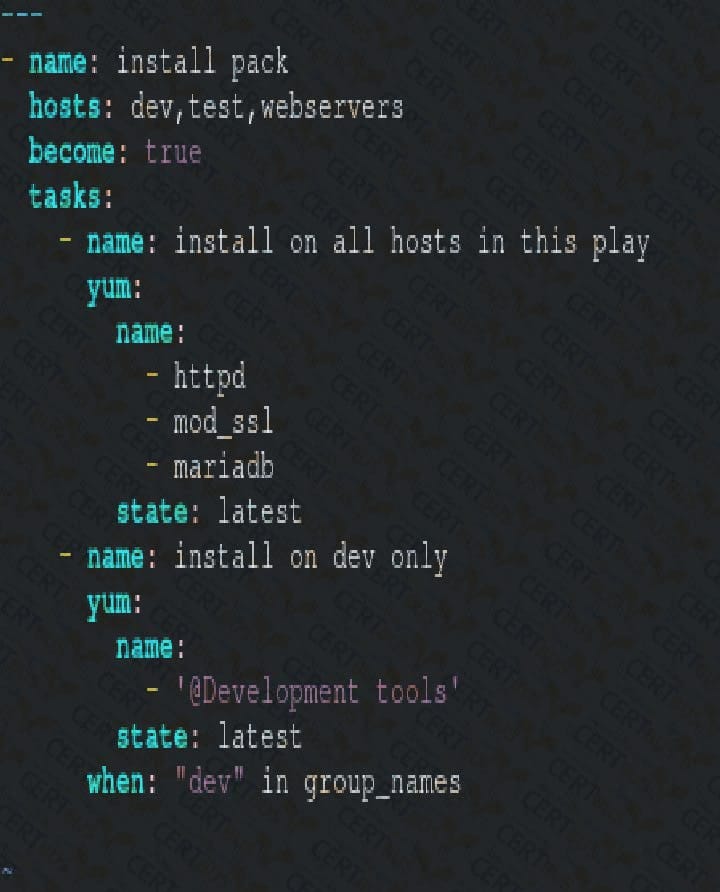
Question 108:
Create a file called packages.yml in /home/sandy/ansible to install somepackages for the following hosts. On dev, prod and webservers install packages httpd, mod_ssl, and mariadb. On dev only install the development tools package. Also, on dev host update all the packages to the latest.
-
Question 109:
Create a role called sample-apache and store it in /home/bob/ansible/roles. The role should
satisfy the following requirements:
*In the role, install and enable httpd. Also enable the firewall to allow http. Also run the template
*index.html.j2 and make sure this runs Create a template index.html.j2 that displays "Welcome to the server HOSTNAME"
In a play called apache.yml in /home/bob/ansible/ run the sample-apache role.
-
Question 110:
Install and configure ansible
User sandy has been created on your control node with the appropriate permissions already, do not change or modify ssh keys. Install the necessary packages to run ansible on the control node. Configure ansible.cfg to be in folder /home/ sandy/ansible/ansible.cfg and configure to access remote machines via the sandy user. All roles should be in the path /home/sandy/ansible/roles. The inventory path should be in /home/sandy/ansible/invenlory.
You will have access to 5 nodes.
1.
node1.example.com
2.
node2.example.com
3.
node3.example.com
4.
node4.example.com
5.
node5.example.com
Configure these nodes to be in an inventory file where node I is a member of group dev. nodc2 is a member of group test, node3 is a member of group proxy, nodc4 and node 5 are members of group prod. Also, prod is a member of group webservers.
Related Exams:
EX200
Red Hat Certified System Administrator (RHCSA)EX294
Red Hat Certified Engineer (RHCE)EX300
Red Hat Certified Engineer (RHCE)EX318
Red Hat Certified Specialist in Virtualization ExamEX407
Red Hat Certified Specialist in Ansible AutomationEX447
Red Hat Certified Specialist in Advanced Automation: Ansible Best PracticesRH033
Red Hat Linux EssentialsRH133
Red Hat Linux System AdministrationRH202
Red Hat Certified Technician on Red Hat Enterprise Linux 5 (Labs)RH302
Red Hat Certified Engineer on Red Hat Enterprise Linux 5 (Labs)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Red Hat exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your EX407 exam preparations and Red Hat certification application, do not hesitate to visit our Vcedump.com to find your solutions here.