Exam Details
Exam Code
:FC0-U61Exam Name
:CompTIA IT Fundamentals+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:518 Q&AsLast Updated
:Apr 13, 2025
CompTIA CompTIA Certifications FC0-U61 Questions & Answers
-
Question 251:
SQL databases use primary and foreign keys to enable which of the following?
A. Rows
B. Fields
C. Schemas
D. Relationships
-
Question 252:
Which of the following is a logical structure for storing files?
A. Folder
B. Extension
C. Permissions
D. Shortcut
-
Question 253:
Which of the following are the primary functions of an operating system? (Choose two.)
A. Provide structure for file and data management.
B. Provide protection against malware and viruses.
C. Provide peer-to-peer networking capability.
D. Provide user data encryption.
E. Provide virtual desktop capability.
F. Provide system resources.
-
Question 254:
Given the following pseudocode:
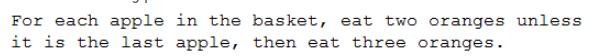
If there are seven apples in the basket, which of the following would be the number of oranges a person eats?
A. 10
B. 14
C. 15
D. 17
-
Question 255:
Concerned with vulnerabilities on a home network, an administrator replaces the wireless router with a recently released new device. After configuring the new device utilizing the old SSID and key, some light switches are no longer communicating. Which of the following is the MOST likely cause?
A. The light switches do not support WPA2.
B. The router is operating on a different channel.
C. The key does not meet password complexity requirements.
D. The SSID is not being broadcast.
-
Question 256:
Which of the following storage types is MOST vulnerable to magnetic damage?
A. Flash
B. SSD
C. Optical
D. HDD
-
Question 257:
When developing a game, a developer creates a boss object that has the ability to jump. Which of the following programming concepts does jump represent?
A. Method
B. Object
C. Property
D. Attribute
-
Question 258:
A technician is troubleshooting an error message and tests the same program on a separate, identical machine. Which of the following troubleshooting methodology steps is this an example of?
A. Duplicate the problem
B. Gather information
C. Question users
D. Divide and conquer
-
Question 259:
Which of the following is a reason why complex passwords are required?
A. To encourage password variety
B. To prevent someone from guessing them
C. To make them harder to remember
D. To reduce social engineering attacks
-
Question 260:
Consider the following statements:

Given the input (userin) of `analyst`, to which of the following would the clearance variable be set?
A. topsecret
B. normal
C. analyst
D. restricted
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your FC0-U61 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.