Exam Details
Exam Code
:HPE6-A78Exam Name
:Aruba Certified Network Security AssociateCertification
:HP CertificationsVendor
:HPTotal Questions
:60 Q&AsLast Updated
:Mar 28, 2025
HP HP Certifications HPE6-A78 Questions & Answers
-
Question 31:
You are managing an Aruba Mobility Controller (MC). What is a reason for adding a "Log Settings" definition in the ArubaOS Diagnostics > System > Log Settings page?
A. Configuring the Syslog server settings for the server to which the MC forwards logs for a particular category and level
B. Configuring the MC to generate logs for a particular event category and level, but only for a specific user or AP.
C. Configuring a filter that you can apply to a defined Syslog server in order to filter events by subcategory
D. Configuring the log facility and log format that the MC will use for forwarding logs to all Syslog servers
-
Question 32:
Refer to the exhibit.
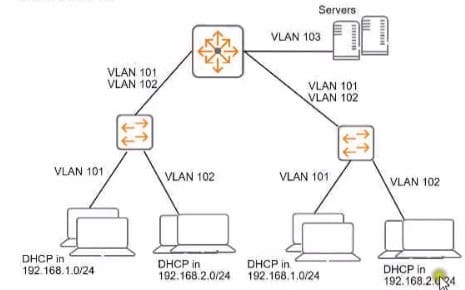
You need to ensure that only management stations in subnet 192.168.1.0/24 can access the ArubaOS-
Switches' CLI. Web Ul. and REST interfaces The company also wants to let managers use these stations
to access other parts of the network.
What should you do?
A. Establish a Control Plane Policing class that selects traffic from 192.168 1.0/24.
B. Specify 192.168.1.0.255.255.255.0 as authorized IP manager address
C. Configure the switch to listen for these protocols on OOBM only.
D. Specify vlan 100 as the management vlan for the switches.
-
Question 33:
Which correctly describes a way to deploy certificates to end-user devices?
A. ClearPass Onboard can help to deploy certificates to end-user devices, whether or not they are members of a Windows domain
B. ClearPass Device Insight can automatically discover end-user devices and deploy the proper certificates to them
C. ClearPass OnGuard can help to deploy certificates to end-user devices, whether or not they are members of a Windows domain
D. in a Windows domain, domain group policy objects (GPOs) can automatically install computer, but not user certificates
-
Question 34:
You need to deploy an Aruba instant AP where users can physically reach It. What are two recommended options for enhancing security for management access to the AP? (Select two )
A. Disable Its console ports
B. Place a Tamper Evident Label (TELS) over its console port
C. Disable the Web Ul.
D. Configure WPA3-Enterpnse security on the AP
E. install a CA-signed certificate
-
Question 35:
You have detected a Rogue AP using the Security Dashboard.
Which two actions should you take in responding to this event? (Select two)
A. There is no need to locale the AP If you manually contain It.
B. This is a serious security event, so you should always contain the AP immediately regardless of your company's specific policies.
C. You should receive permission before containing an AP. as this action could have legal Implications.
D. For forensic purposes, you should copy out logs with relevant information, such as the time mat the AP was detected and the AP's MAC address.
E. There is no need to locate the AP If the Aruba solution is properly configured to automatically contain it.
-
Question 36:
What is a Key feature of me ArubaOS firewall?
A. The firewall is stateful which means that n can track client sessions and automatically allow return traffic for permitted sessions
B. The firewall Includes application layer gateways (ALGs). which it uses to filter Web traffic based on the reputation of the destination web site.
C. The firewall examines all traffic at Layer 2 through Layer 4 and uses source IP addresses as the primary way to determine how to control traffic.
D. The firewall is designed to fitter traffic primarily based on wireless 802.11 headers, making it ideal for mobility environments
-
Question 37:
What is symmetric encryption?
A. It simultaneously creates ciphertext and a same-size MAC.
B. It any form of encryption mat ensures that thee ciphertext Is the same length as the plaintext.
C. It uses the same key to encrypt plaintext as to decrypt ciphertext.
D. It uses a Key that is double the size of the message which it encrypts.
-
Question 38:
Which attack is an example or social engineering?
A. An email Is used to impersonate a Dank and trick users into entering their bank login information on a fake website page.
B. A hacker eavesdrops on insecure communications, such as Remote Desktop Program (RDP). and discovers login credentials.
C. A user visits a website and downloads a file that contains a worm, which sell-replicates throughout the network.
D. An attack exploits an operating system vulnerability and locks out users until they pay the ransom.
-
Question 39:
Refer to the exhibit.
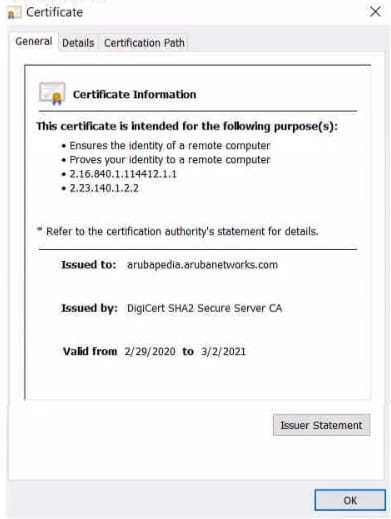
Device A is establishing an HTTPS session with the Arubapedia web sue using Chrome. The Arubapedia web server sends the certificate shown in the exhibit.
What does the browser do as part of vacating the web server certificate?
A. It uses the public key in the DigCen SHA2 Secure Server CA certificate to check the certificate's signature.
B. It uses the public key in the DigCert root CA certificate to check the certificate signature
C. It uses the private key in the DigiCert SHA2 Secure Server CA to check the certificate's signature.
D. It uses the private key in the Arubapedia web site's certificate to check that certificate's signature
-
Question 40:
What is an Authorized client as defined by ArubaOS Wireless Intrusion Prevention System (WIP)?
A. a client that has a certificate issued by a trusted Certification Authority (CA)
B. a client that is not on the WIP blacklist
C. a client that has successfully authenticated to an authorized AP and passed encrypted traffic
D. a client that is on the WIP whitelist.
Related Exams:
HP0-D15
Administering HP CloudSystem Matrix SolutionsHP0-D20
Architecting the HP Matrix Operating EnvironmentHP2-E56
Selling HP SMB SolutionsHP2-H88
Selling HP Business Personal Systems Hardware 2019HP2-I14
Selling HP Supplies 2020HP2-I15
Selling HP Business Personal Systems Hardware 2020HP2-I17
Selling HP Printing Hardware 2020HP2-I44
Selling HP Workstations 2022HP2-I73
Selling HP Retail and Hospitality Solutions 2024HP2-N51
HP Application Lifecycle Management 12.x Software
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only HP exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your HPE6-A78 exam preparations and HP certification application, do not hesitate to visit our Vcedump.com to find your solutions here.