Exam Details
Exam Code
:JN0-347Exam Name
:Enterprise Routing and Switching, Specialist (JNCIS-ENT)Certification
:Juniper CertificationsVendor
:JuniperTotal Questions
:136 Q&AsLast Updated
:Mar 27, 2025
Juniper Juniper Certifications JN0-347 Questions & Answers
-
Question 21:
You manage a Layer 2 network that spans two buildings. You are asked to ensure that all traffic that
traverses this connection between the two buildings is secured.
Which port security feature should be used to secure this Layer 2 traffic?
A. IP source guard
B. MACsec
C. DHCP snooping
D. dynamic ARP inspection
-
Question 22:
Click the Exhibit button.
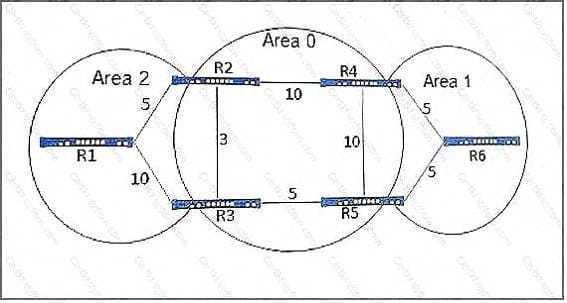
Referring to the exhibit, which path will traffic from R6 take to reach R1?
A. R6 > R4 > R2 > R1
B. R6 > R4 > R2 > R3 > R1
C. R6 > R5 > R3 > R1
D. R6 > R5 > R3 > R2 > R1
-
Question 23:
Click the Exhibit button. Referring to the exhibit, which policy will export routes to IBGP peers?
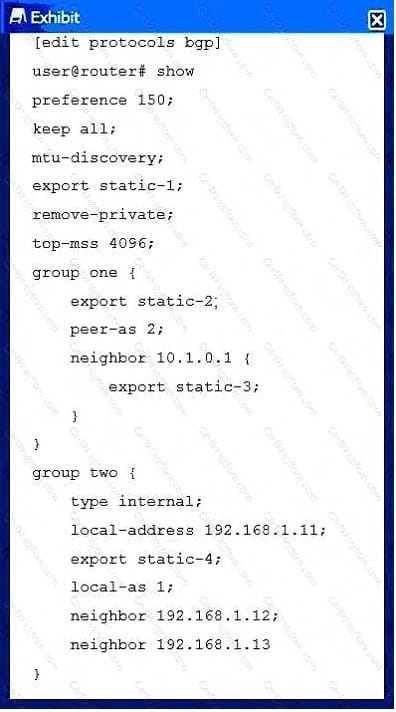
A. static-4
B. static-1
C. static-3
D. static-2
-
Question 24:
Depending on the link type, OSPF sends link state update packets to which two addresses? (Choose two.)
A. 224.0.0.8
B. 224.0.0.6
C. 224.0.0.9
D. 224.0.0.5
-
Question 25:
Click the Exhibit button. Based on the trace options output shown in the exhibit, what is the problem with the adjacency?
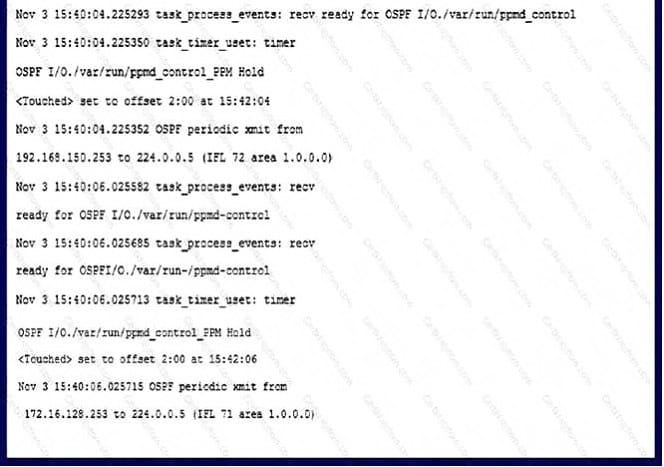
A. connectivity
B. authentication mismatch
C. area mismatch
D. MTU mismatch
-
Question 26:
You notice that there are currently two MAC addresses associated with a single access port in the bridge table on one of your EX Series switches. What are two explanations for this behavior? (Choose two.)
A. The access port connects to an IP phone which connects to a host device.
B. The native VLAN feature has been associated with the access port.
C. The mac-move-limit feature has been disabled on the access port.
D. The access port connects to multiple hosts through a rogue device.
-
Question 27:
Which statement about IS-IS adjacencies is true?
A. Adjacency formation between Level 2 routers must have different area IDs.
B. Adjacency formation between Level 2 routers must have the same area ID.
C. Adjacency formation between Level 1 routers must have the same area ID.
D. Adjacency formation between Level 1 routers must have different area IDs.
-
Question 28:
Click the Exhibit button. A number of reports from end-users indicate that internal and external
communications are intermittent and not reliable.
You verified the status of the switch ports and have determined that they are up and operational. You also
noticed a very high level of link bandwidth utilization on those same ports.
The current topology of the affected environment is shown in the exhibit. What would be the cause of the
reported issues?
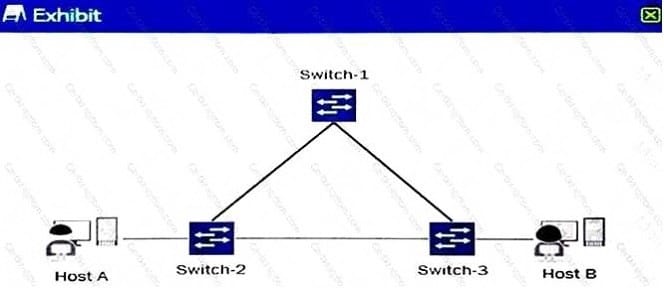
A. A lack of port-based ACLs filtering the traffic flows.
B. A lack of a loop-prevention mechanism or protocol.
C. A malformed route-based ACL improperly filtering traffic flows.
D. A misconfigured interior gateway protocol (IGP).
-
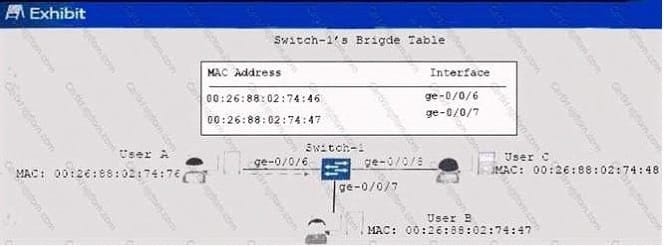
Question 29:
Click the Exhibit button. Switch-1 in the exhibit receives a packet from User A with a destination MAC address of
00:26:88:02:74:48.
Which statement is correct?
A.
Switch-1 floods the packet out ge-0/0/6, ge-0/0/7, and ge-0/0/8.
B.
Switch-1 sends the packet out ge-0/0/7 only.
C.
Switch-1 sends the packet out ge-0/0/8 only.
D.
Switch-1 floods the packet out ge-0/0/7 and ge-0/0/8.
-
Question 30:
Which statement is true about GRE tunnels?
A. GRE tunnels can be used for only IP packets.
B. GRE tunnels ensure that a packet does not live forever.
C. Packets are encapsulated unchanged before entering the tunnel.
D. GRE tunnels support point-to-multipoint.
Related Exams:
JN0-102
Internet Associate, Junos(JNCIA-Junos)JN0-104
Junos, Associate (JNCIA-Junos)JN0-105
Junos, Associate (JNCIA-Junos)JN0-1101
Juniper Networks Certified Design Associate (JNCDA)JN0-130
Juniper networks Certified internet specialist.e(jncis-e)JN0-1301
Data Center Design, Specialist (JNCDS-DC)JN0-1302
Data Center Design Specialist (JNCDS-DC)JN0-1331
Security Design, Specialist (JNCDS-SEC)JN0-1332
Security Design, Specialist (JNCDS-SEC)JN0-1361
Service Provider Design Specialist (JNCDS-SP)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Juniper exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JN0-347 exam preparations and Juniper certification application, do not hesitate to visit our Vcedump.com to find your solutions here.