Exam Details
Exam Code
:JN0-637Exam Name
:Security, Professional (JNCIP-SEC)Certification
:Juniper CertificationsVendor
:JuniperTotal Questions
:65 Q&AsLast Updated
:Dec 17, 2024
Juniper Juniper Certifications JN0-637 Questions & Answers
-
Question 31:
A company has acquired a new branch office that has the same address space of one of its local networks, 192.168.100/24. The offices need to communicate with each other.
Which two NAT configurations will satisfy this requirement? (Choose two.)
A. [edit security nat source] user@OfficeA# show rule-set OfficeBtoA { from zone OfficeB; to zone OfficeA; rule 1 { match { source-address 192.168.210.0/24; destination-address 192.168.200.0/24; } then { source-nat { interface; } } } }
B. [edit security nat static] user@OfficeA# show rule-set From-Office-B { from interface ge-0/0/0.0; rule 1 { match { destination-address 192.168.200.0/24; } then { static-nat { prefix 192.168.100.0/24; } } } }
C. [edit security nat static] user@OfficeB# show rule-set From-Office-A { from interface ge-0/0/0.0; rule 1 { match { destination-address 192.168.210.0/24; } then { static-nat { prefix 192.168.100.0/24; } } } }
D. [edit security nat source] user@OfficeB# show rule-set OfficeAtoB { from zone OfficeA; to zone OfficeB; rule 1 { match { source-address 192.168.200.0/24; destination-address 192.168.210.0/24; } then { source-nat { interface; } } } }
-
Question 32:
Which two statements are true about the procedures the Junos security device uses when handling traffic destined for the device itself? (Choose two.)
A. If the received packet is addressed to the ingress interface, then the device first performs a security policy evaluation for the junos-host zone.
B. If the received packet is destined for an interface other than the ingress interface, then the device performs a security policy evaluation for the junos-host zone.
C. If the received packet is addressed to the ingress interface, then the device first examines the host- inbound-traffic configuration for the ingress interface and zone.
D. If the received packet is destined for an interface other than the ingress interface, then the device performs a security policy evaluation based on the ingress and egress zone.
-
Question 33:
Your IPsec tunnel is configured with multiple security associations (SAs). Your SRX Series device supports the CoS-based IPsec VPNs with multiple IPsec SAs feature. You are asked to configure CoS for this tunnel. Which two statements are true in this scenario? (Choose two.)
A. The local and remote gateways do not need the forwarding classes to be defined in the same order.
B. A maximum of four forwarding classes can be configured for a VPN with the multi-sa forwarding- classes statement.
C. The local and remote gateways must have the forwarding classes defined in the same order.
D. A maximum of eight forwarding classes can be configured for a VPN with the multi-sa forwarding- classes statement.
-
Question 34:
Referring to the exhibit,

which two statements about User1 are true? (Choose two.)
A. User1 has access to the configuration specific to their assigned logical system.
B. User1 is logged in to logical system LSYS-1.
C. User1 can add logical units to an interface that a primary administrator has not previously assigned.
D. User1 can view outputs from other user logical systems.
-
Question 35:
Referring to the exhibit.

You are asked to ensure that Internet users can access the company's internal webserver using its FQDN.
However, the internal DNS server's A record only points to the webserver's private address.
Referring to the exhibit, which two actions are required to complete this task? (Choose two.)
A. Disable the DNS ALG.
B. Configure static NAT for both the DNS server and the webserver.
C. Configure destination NAT for both the DNS server and the webserver.
D. Configure proxy ARP on ge-0/0/3.
-
Question 36:
What are three core components for enabling advanced policy-based routing? (Choose three.)
A. Filter-based forwarding
B. Routing options
C. Routing instance
D. APBR profile
E. Policies
-
Question 37:
Referring to the exhibit.
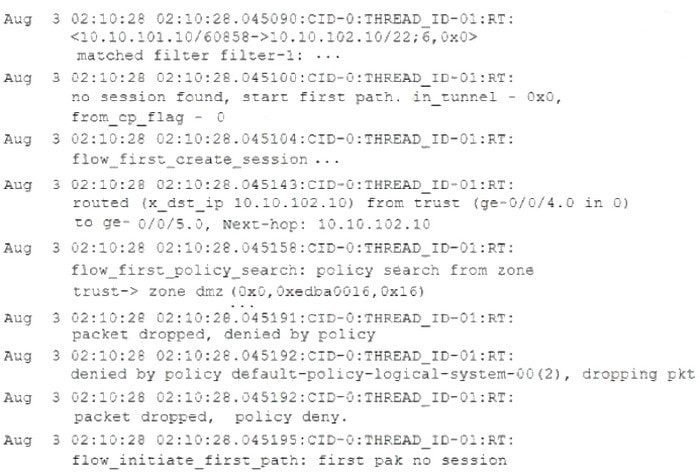
Which two statements are correct? (Choose two.)
A. The packet is dropped by the default security policy.
B. The packet is dropped by a configured security policy.
C. The data shown requires a traceoptions flag of host-traffic.
D. The data shown requires a traceoptions flag of basic-datapath.
-
Question 38:
Which two statements are correct about mixed mode? (Choose two.)
A. Layer 2 and Layer 3 interfaces can use the same security zone.
B. IRB interfaces can be used to route traffic.
C. Layer 2 and Layer 3 interfaces can use separate security zones.
D. IRB interfaces cannot be used to route traffic.
-
Question 39:
You are asked to configure tenant systems.
Which two statements are true in this scenario? (Choose two.)
A. A tenant system can have only one administrator.
B. After successful configuration, the changes are merged into the primary database for each tenant system.
C. Tenant systems have their own configuration database.
D. You can commit multiple tenant systems at a time.
-
Question 40:
Referring to the exhibit,
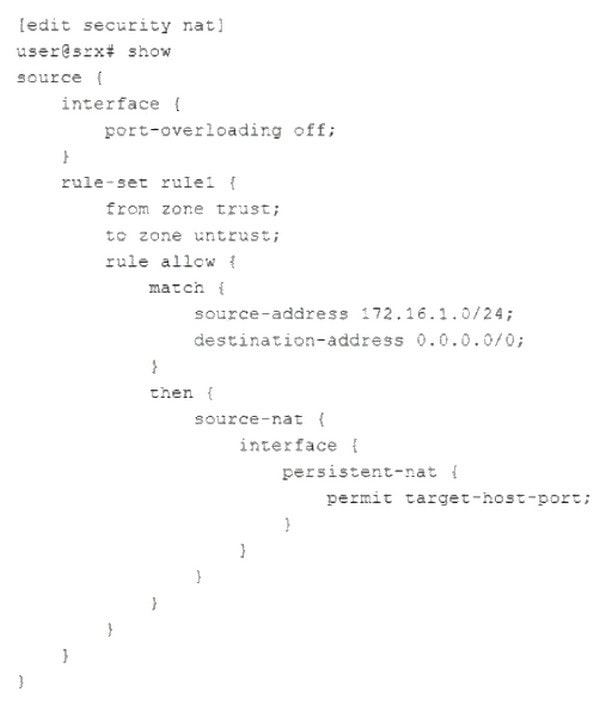
which two statements are correct about the NAT configuration? (Choose two.)
A. Both the internal and the external host can initiate a session after the initial translation.
B. Only a specific host can initiate a session to the reflexive address after the initial session.
C. Any external host will be able to initiate a session to the reflexive address.
D. The original destination port is used for the source port for the session.
Related Exams:
JN0-102
Internet Associate, Junos(JNCIA-Junos)JN0-104
Junos, Associate (JNCIA-Junos)JN0-105
Junos, Associate (JNCIA-Junos)JN0-1101
Juniper Networks Certified Design Associate (JNCDA)JN0-130
Juniper networks Certified internet specialist.e(jncis-e)JN0-1301
Data Center Design, Specialist (JNCDS-DC)JN0-1302
Data Center Design Specialist (JNCDS-DC)JN0-1331
Security Design, Specialist (JNCDS-SEC)JN0-1332
Security Design, Specialist (JNCDS-SEC)JN0-1361
Service Provider Design Specialist (JNCDS-SP)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Juniper exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JN0-637 exam preparations and Juniper certification application, do not hesitate to visit our Vcedump.com to find your solutions here.