Exam Details
Exam Code
:MD-100Exam Name
:Windows ClientCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:409 Q&AsLast Updated
:Apr 07, 2025
Microsoft Microsoft Certifications MD-100 Questions & Answers
-
Question 251:
You have a Microsoft 365 Enterprise E3 license.
You have a computer named Computer1 that runs Windows 10.
You need to ensure that you can access the files on Computer1 by using a web browser on another computer. What should you configure?
A. Sync your settings in the Settings app
B. the File Explorer desktop app
C. the Microsoft OneDrive desktop app
D. Default apps in the Settings app
-
Question 252:
Your network contains an Active Directory domain named Contoso.com.
A user named User1 has a personal computer named Computer that runs Windows 10 Pro. User1 has a VPN connection to the corporate network. You need to ensure that when User1 connection to the corporate network.
You need to ensure that when user1 connects to the VPN, network traffic uses a proxy located in the corporate network. The solution must ensure that User1 can access the internet when disconnected from the VPN.
What should you do?
A. From the Settings app, modify the properties of the VPN connection.
B. From the Setting app, modify proxy settings for the local computer.
C. From Control panel, modify the properties of the VPN connection
D. From Control Panel, modify the Windows Defender Firewall settings
-
Question 253:
Your network contains an Active Directory domain. The domain contains computers that run Windows 10.
You need to provide a user with the ability to remotely create and modify shares on the computers. The solution must use the principle of least privilege.
To which group should you add the user?
A. Power Users
B. Remote Management Users
C. Administrators
D. Network Configuration Operators
-
Question 254:
You have a file named Reg1.reg that contains the following content.
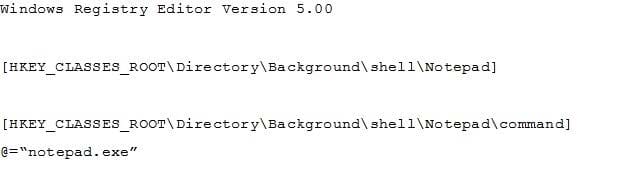
What is the effect of importing the file?
A. A key named command will be renamed as notepad.exe.
B. In a key named Notepad, the command value will be set to @="notepad.exe".
C. In a key named command, the default value will be set to notepad.exe.
-
Question 255:
You have a computer named Computer1 that runs Windows 10.
From Event Viewer on Computer1, you have a task named Action1 that is attached to the following event:
1.
Log: System
2.
Source: Kernel-General
3.
Event ID: 16
You need to modify the settings of Action1.
What should you use?
A. the Settings app
B. Task Scheduler
C. Event Viewer
D. System Configuration
-
Question 256:
You have a computer that runs Windows 10.
You need to be able to recover the computer by using System Image Recovery.
What should you use to create a system image?
A. Windows System Image Manager (Windows SIM)
B. Backup and Restore (Windows 7)
C. File History
D. System Protection
-
Question 257:
You have a computer named Computer1 that runs Windows 10.
You are troubleshooting connectivity issues on Computer1.
You need to view the remote addresses to which Computer1 has active TCP connections.
Which tool should you use?
A. Performance Monitor
B. Task Manager
C. Resource Monitor
D. Windows Defender Firewall with Advanced Security
-
Question 258:
Your network contains an Active Directory domain. The domain contains 10 computers that run Windows 10. Users in the finance department use the computers.
You have a computer named Computer1 that runs Windows 10.
From Computer1, you plan to run a script that executes Windows PowerShell commands on the finance department computers.
You need to ensure that you can run the PowerShell commands on the finance department from Computer1.
What should you do on the finance department computers?
A. From the local Group Policy, enable the Allow Remote Shell Access setting.
B. From the local Group Policy, enable the Turn on Script Execution setting.
C. From the Windows PowerShell, run the Enable-MMAgent cmdlet.
D. From the Windows PowerShell, run the Enable-PSRemoting cmdlet.
-
Question 259:
You have a computer named Computer1 that runs Windows 10. Computer1 is in a workgroup. Computer1 contains the local users shown in the following table.
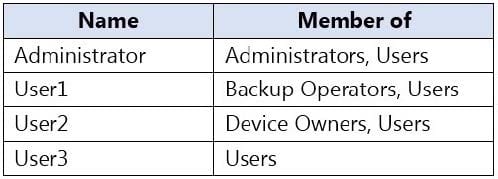
The Users group has Modify permissions to a folder named D:\Folder1.
User3 creates a file named File1.docx in Folder1.
Which users can take ownership of File1.docx?
A. Administrator and User1 only
B. Administrator only
C. Administrator, User1, and User2
D. Administrator and User2 only
-
Question 260:
You have 10 computers that run Windows 10 and have BitLocker Drive Encryption (BitLocker) enabled.
You plan to update the firmware of the computers.
You need to ensure that you are not prompted for the BitLocker recovery key on the next restart. The drive must be protected by BitLocker on subsequent restarts.
Which cmdlet should you run?
A. Unlock-BitLocker
B. Disable-BitLocker
C. Add-BitLockerKeyProtector
D. Suspend-BitLocker
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MD-100 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.