Exam Details
Exam Code
:MD-100Exam Name
:Windows ClientCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:409 Q&AsLast Updated
:Mar 21, 2025
Microsoft Microsoft Certifications MD-100 Questions & Answers
-
Question 31:
You have a Windows 11 Pro device.
You need to perform a scan in Microsoft Defender to check for rootkits.
Which type of scan should you use?
A. full
B. offline
C. custom
D. quick
-
Question 32:
You have a computer named Computer1 that runs Windows 11 and hosts two Hyper-V virtual machines named VM1 and VM2.
You need to ensure that VM1 can connect to the network shares on VM2. The solution must prevent Computer1 from establishing network connections to VM1 or VM2.
Which type of virtual switch should you use?
A. external
B. private
C. internal
-
Question 33:
You have computers that run Windows 11 as shown in the following table.
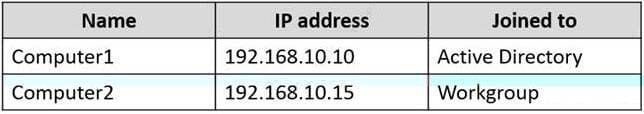
You ping 192.168.10.15 from Computer1 and discover that the request timed out.
You need to ensure that you can successfully ping 192.168.10.15 from Computer1.
Solution: On Computer2, you share a folder.
Does this meet the goal?
A. Yes
B. No
-
Question 34:
Your network contains an Active Directory domain. The domain contains computers that run Windows 10.
All users use Roaming User Profiles.
You have a user named Public1 that is used to sign-in to a public computer.
You need to prevent changes to the user settings of Public1 from being saved to the user profile.
What should you do?
A. Rename Ntuser.dat to Ntuser.v6.
B. Rename the Roaming User Profile folder to Public 1.v1.
C. Rename the Roaming User Profile folder to Public1.man.
D. Rename Ntuser.dat to Ntuser.man.
-
Question 35:
You have the computers shown in the following table.
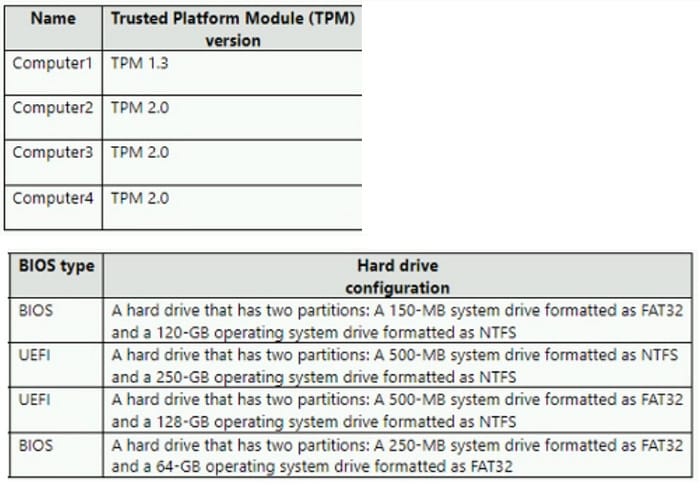
You plan to install Windows 11 and enable BitLocker Drive Encryption (BitLocker). On which computer should you install Windows 11 and enable BitLocker?
A. Computer1
B. Computer2
C. Computer3
D. Computer4
-
Question 36:
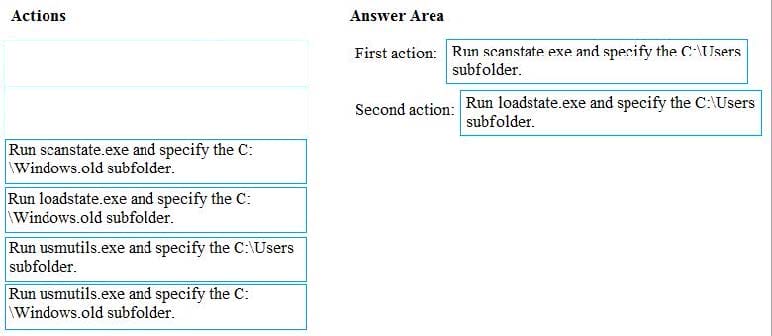
You have a computer named Computer1 that runs Windows 7. Computer1 has a local user named User1 who has a customized profile.
On Computer1, you perform a clean installation of Windows 10 without formatting the drives.
You need to migrate the settings of User1 from Windows7 to Windows 10.
Which two actions should you perform? To answer, drag the appropriate actions to the correct targets. Each action may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
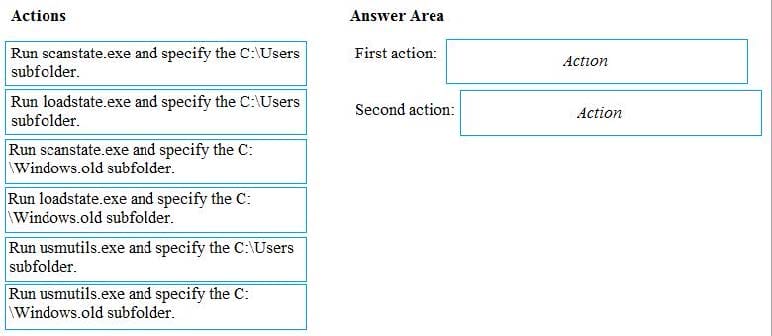
-
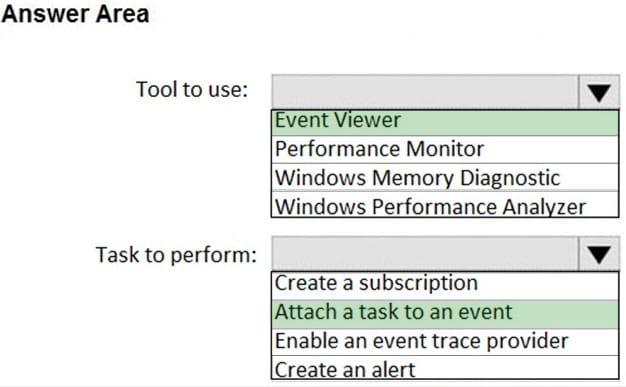
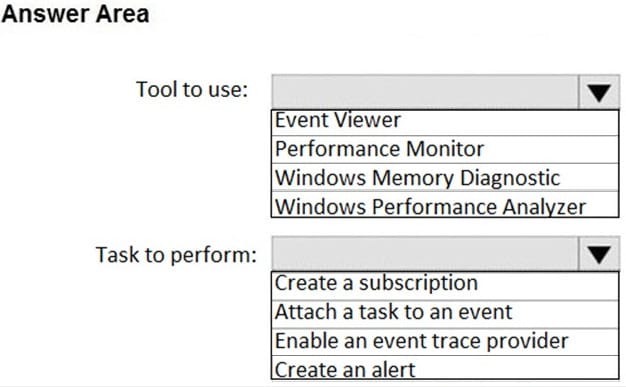
Question 37:
HOTSPOT
You need to reduce the amount of time it takes to restart Application1 when the application crashes.
What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
-
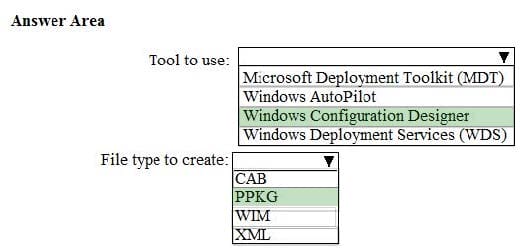
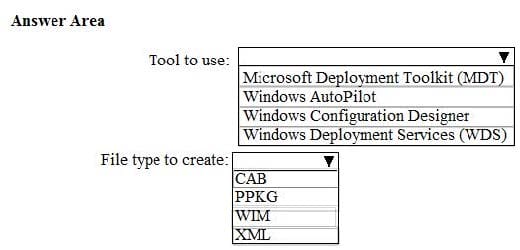
Question 38:
HOTSPOT
You need to implement a solution to configure the contractors’ computers.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
-
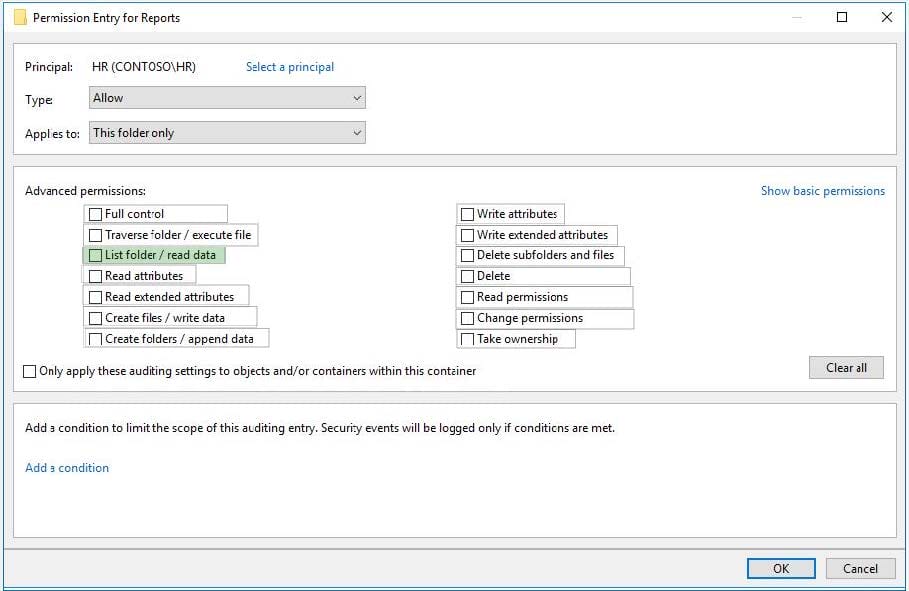
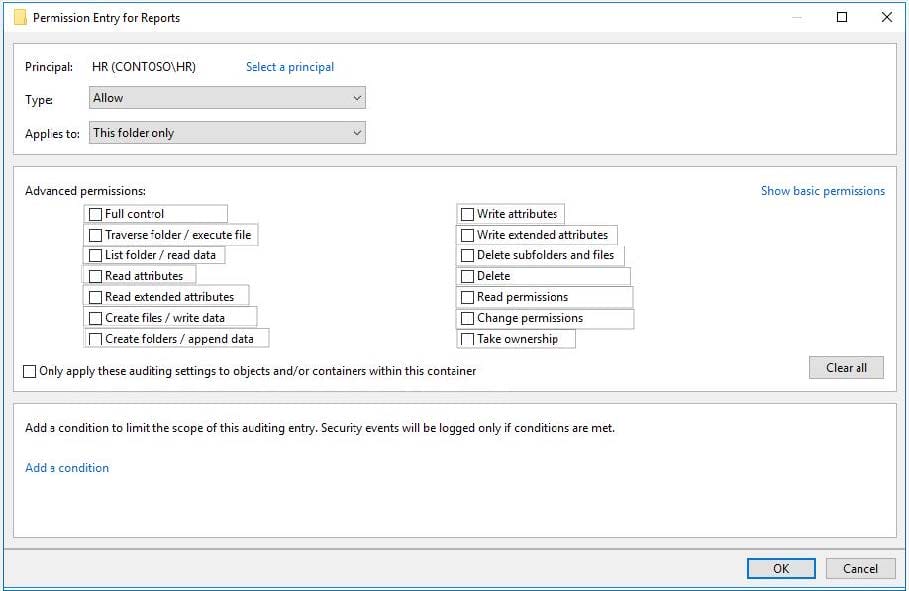
Question 39:
You need to meet the technical requirements for the HR department users.
Which permissions should you assign to the HR department users for the D:\Reports folder? To answer, select the appropriate permissions in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
-
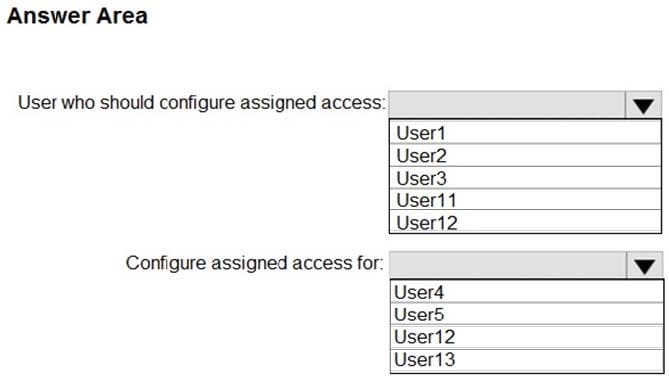
Question 40:
HOTSPOT
You need to meet the technical requirement for Computer1.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MD-100 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.