Exam Details
Exam Code
:MS-100Exam Name
:Microsoft 365 Identity and ServicesCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:535 Q&AsLast Updated
:Apr 10, 2025
Microsoft Microsoft Certifications MS-100 Questions & Answers
-
Question 181:
HOTSPOT
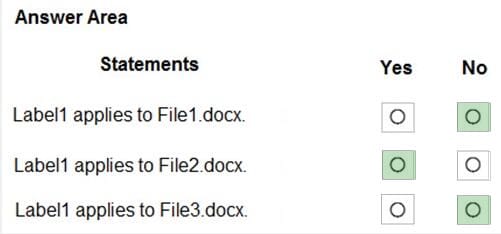
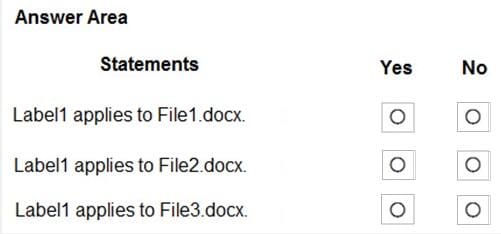
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. A user named User1 has files on a Windows 10 device as shown in the following table.

In Azure Information Protection, you create a label named Label1 that is configured to apply automatically. Label1 is configured as shown in the following exhibit.
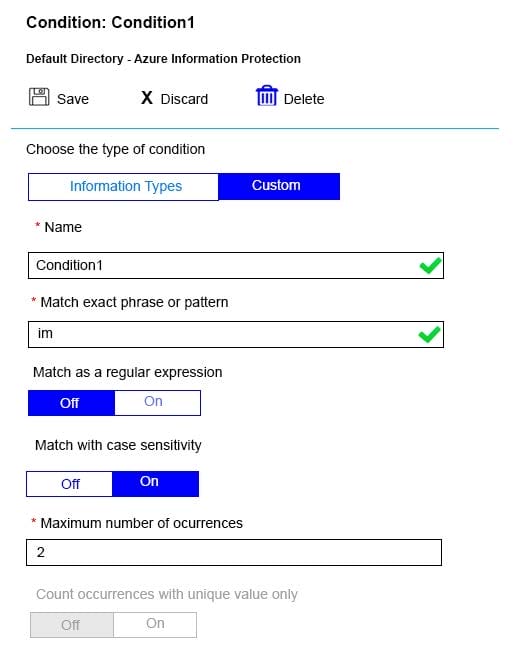
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 182:
HOTSPOT
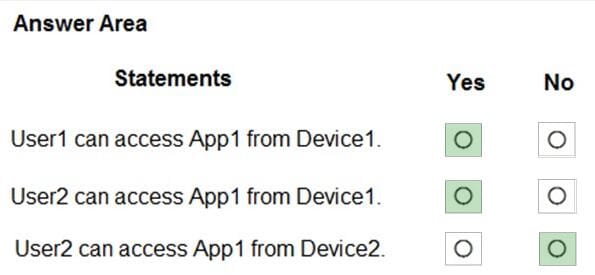
You have a Microsoft 365 subscription that uses a default domain named contoso.com. The domain contains the users shown in the following table.
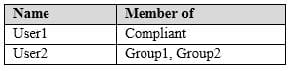
The domain contains the devices shown in the following table.
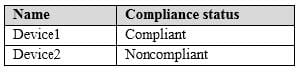
The domain contains conditional access policies that control access to a cloud app named App1. The policies are configured as shown in the following table.

For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Hot Area:
-
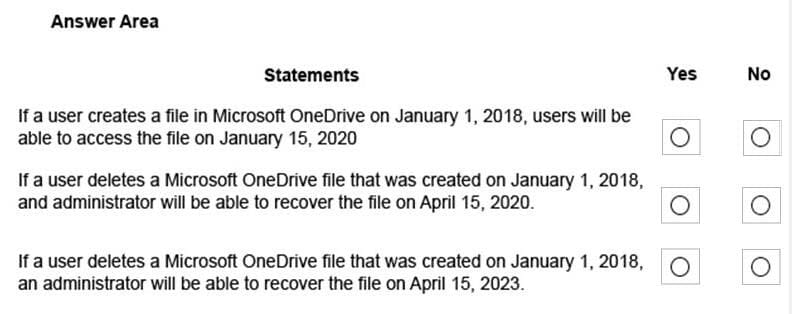
Question 183:
HOTSPOT
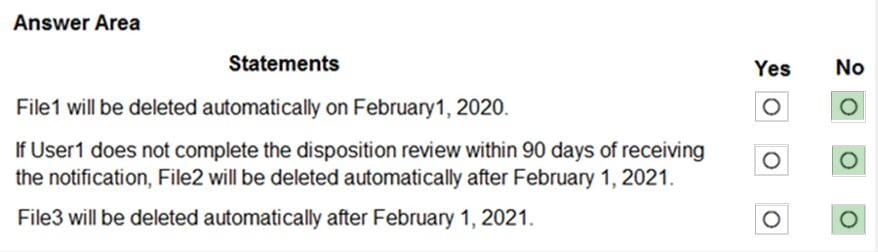
You have a Microsoft 365 subscription that uses a default named contoso.com. Three files were created on February 1, 2019, as shown in the following table.
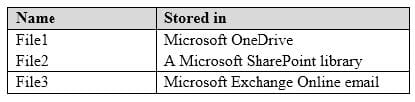
On March 1, 2019, you create two retention labels named Label1 and label2.
The settings for Label1 are configured as shown in the Label1 exhibit. (Click the Label1 tab.) Label 1
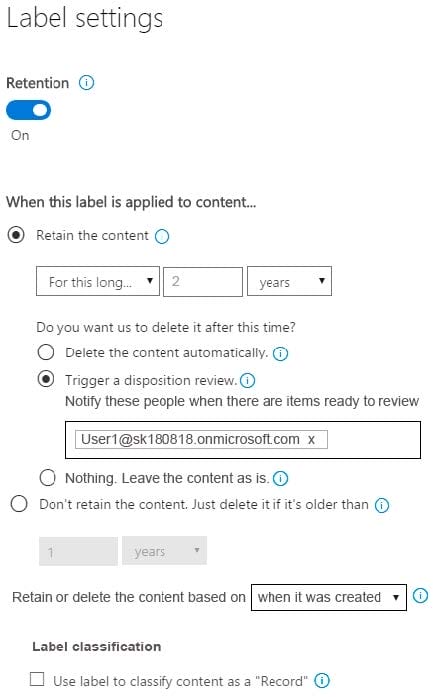
The settings for Label2 are configured as shown in the Label1 exhibit. (Click the Label2 tab.) Label 2
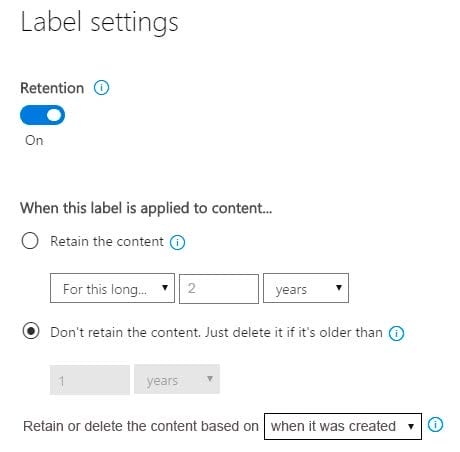
You apply the retention labels to Exchange email, SharePoint sites, and OneDrive accounts. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Hot Area:
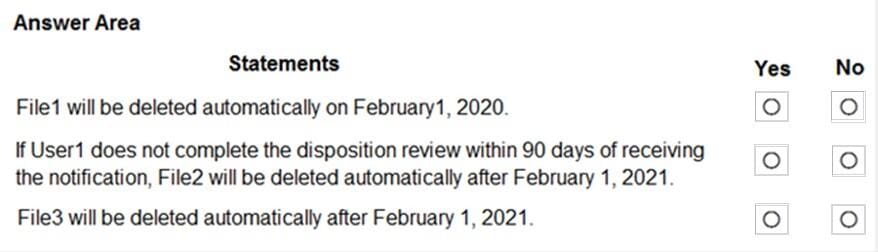
-
Question 184:
HOTSPOT
You have retention policies in Microsoft 365 as shown in the following table.
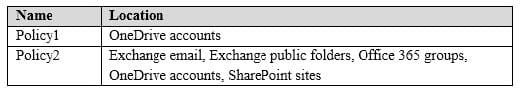
Policy1 is configured as shown in the Policy1 exhibit. (Click the Policy1 tab.) Policy1
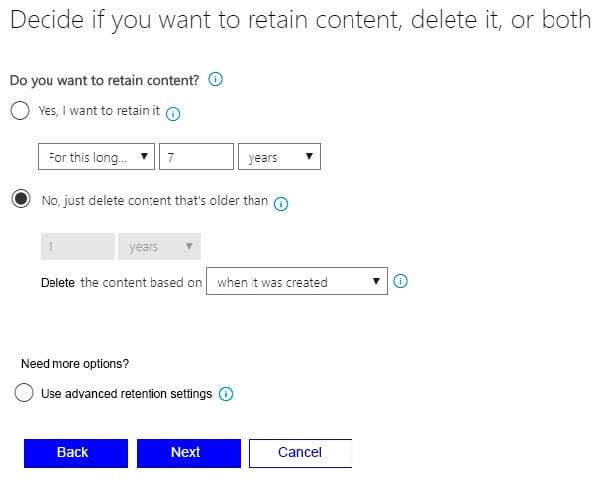
Policy1 is configured as shown in the Policy2 exhibit. (Click the Policy2 tab.) Policy2

For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Hot Area:
-
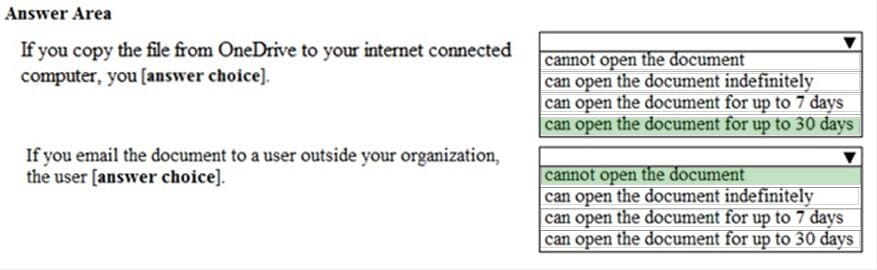
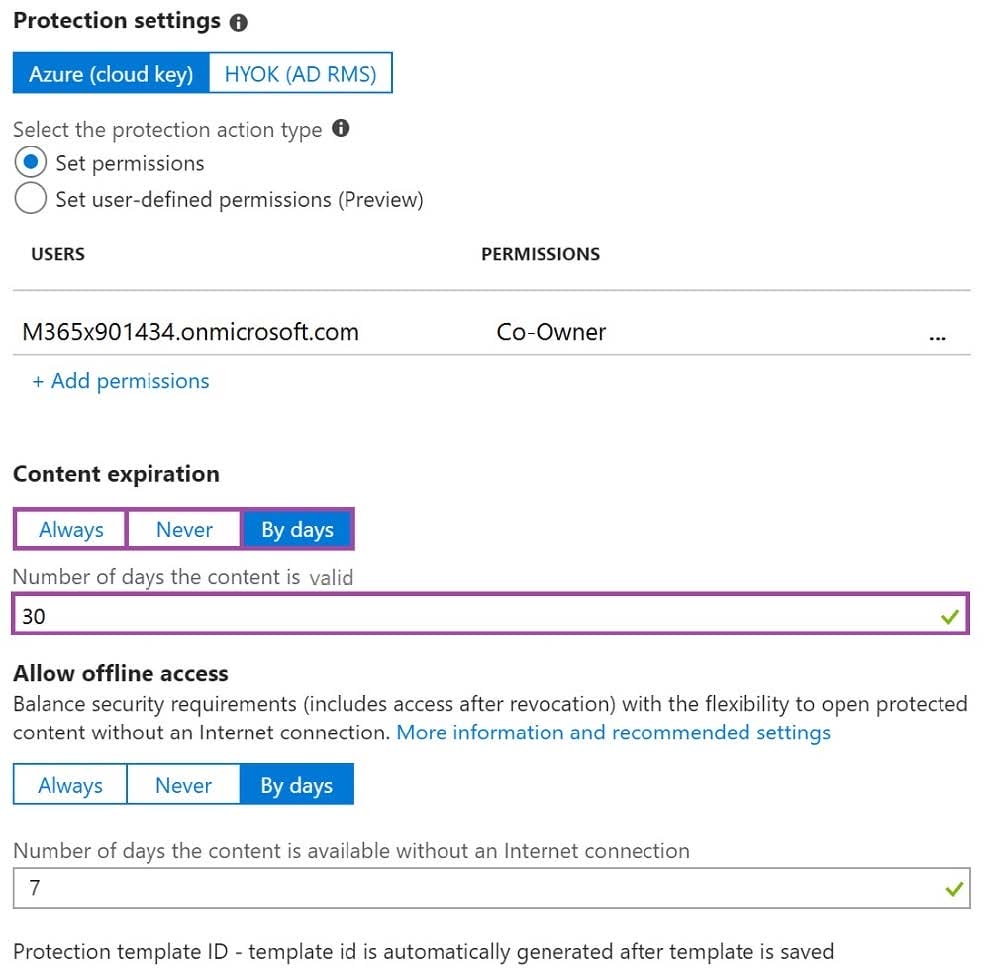
Question 185:
HOTSPOT
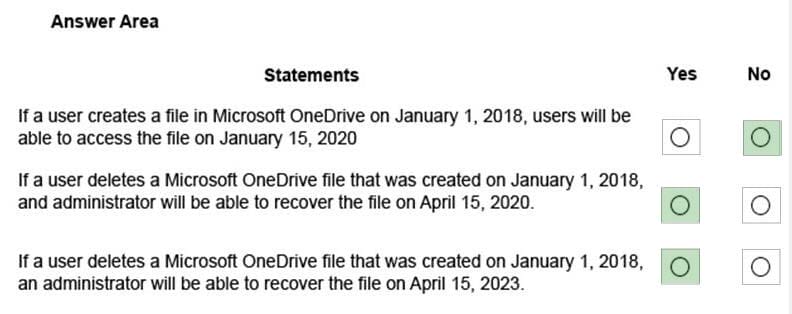
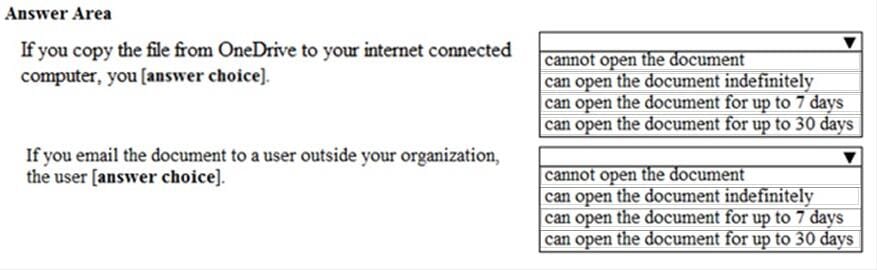
You have a document in Microsoft OneDrive that is encrypted by using Microsoft Azure Information Protection as shown in the following exhibit.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
Hot Area:
-
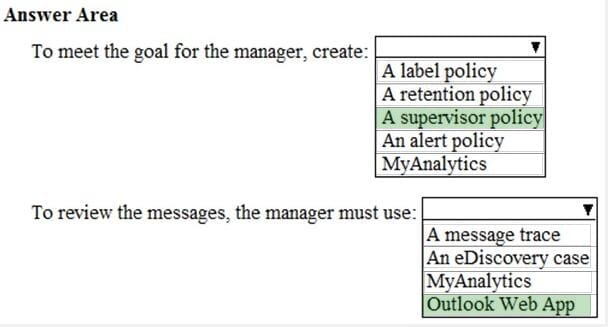
Question 186:
HOTSPOT
You have a Microsoft 365 subscription.
You have a group named Support. Users in the Support group frequently send email messages to external users.
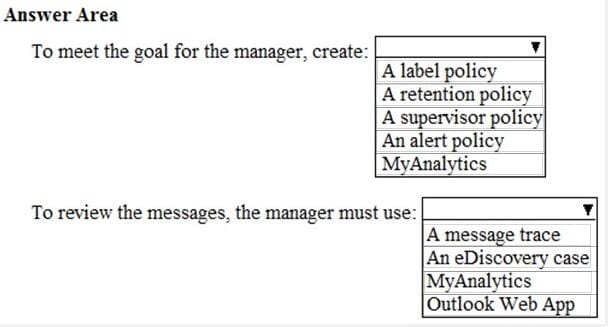
The manager of the Support group wants to randomly review messages that contain attachments.
You need to provide the manager with the ability to review messages that contain attachments sent from the Support group users to external users. The manager must have access to only 10 percent of the messages.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
-
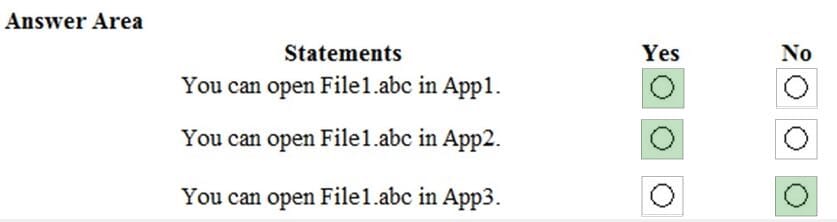
Question 187:
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains the file servers shown in the following table.
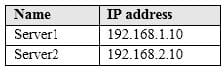
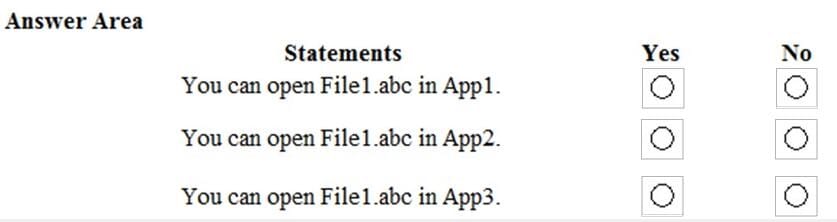
A file named File1.abc is stored on Server1. A file named File2.abc is stored on Server2. Three apps named App1, App2, and App3 all open files that have the .abc file extension. You implement Windows Information Protection (WIP) by using the following configurations:
1.
Exempt apps: App2
2.
Protected apps: App1
3.
Windows Information Protection mode: Block
4.
Network boundary: IPv4 range of 192.168.1.1-192.168.1.255
You need to identify the apps from which you can open File1.abc
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
-
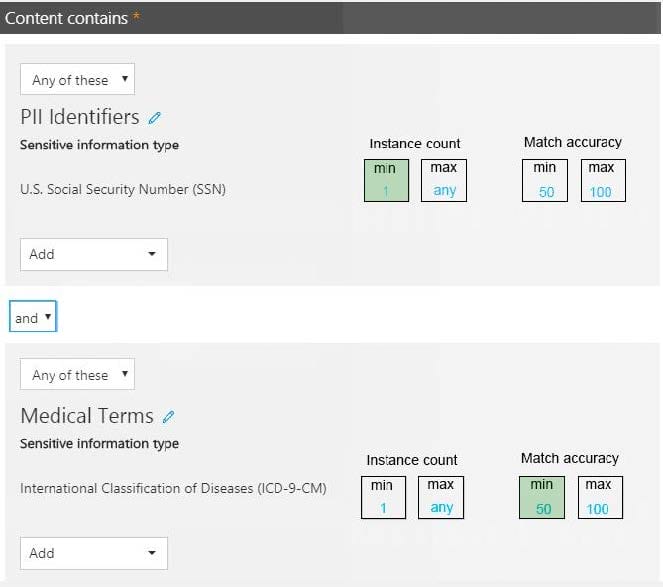
Question 188:
HOTSPOT
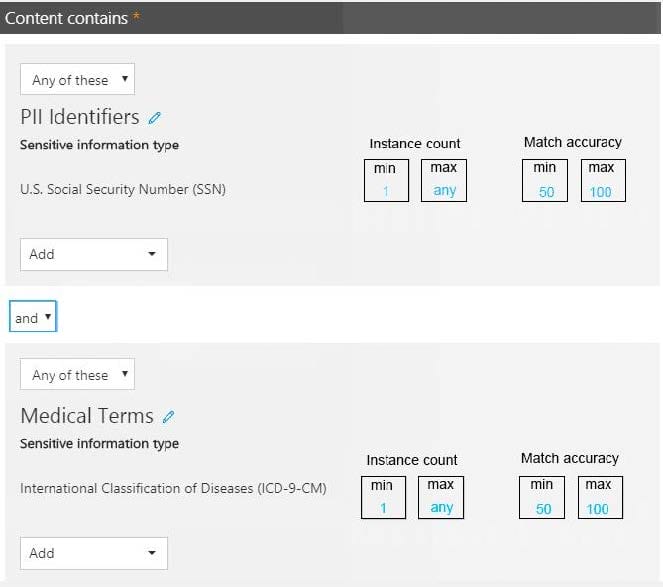
You have a data loss prevention (DLP) policy.
You need to increase the likelihood that the DLP policy will apply to data that contains medical terms from the International Classification of Diseases (ICD-9-CM). The solution must minimize the number of false positives.
Which two settings should you modify? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 189:
HOTSPOT
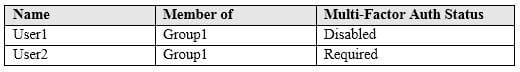
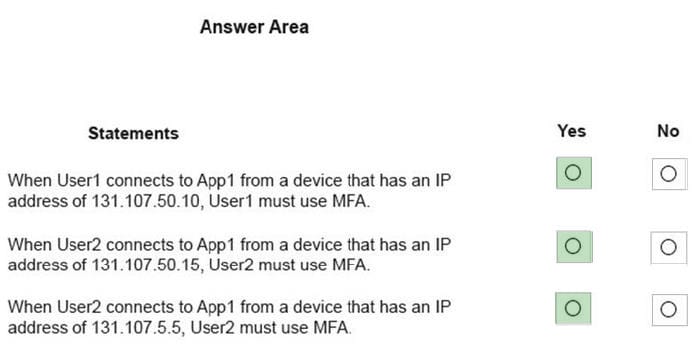
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.
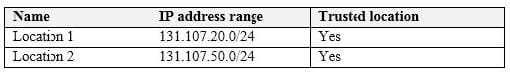
Multi-factor authentication (MFA) is configured to use 131.107.50/24 for trusted IPs. The tenant contains the named locations shown in the following table.
You create a conditional access policy that has the following configurations:
1.
Users and groups assignment: All users
2.
Cloud apps assignment: App1
3.
Conditions: Include all trusted locations
4.
Grant access: require multi-factor authentication
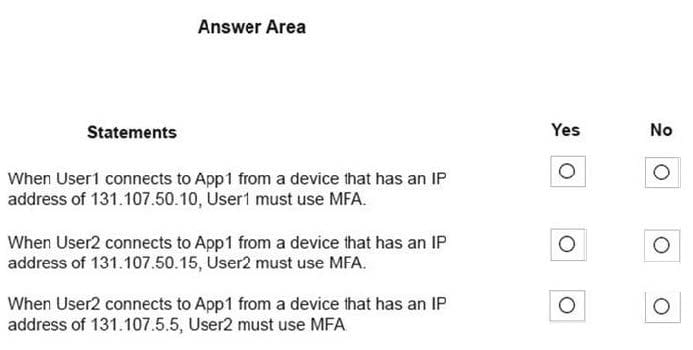
For each of the following statements, select Yes if the statement is true. otherwise, select No.
NOTE: Each correct selection is worth one point.
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.
Hot Area:
-
Question 190:
HOTSPOT
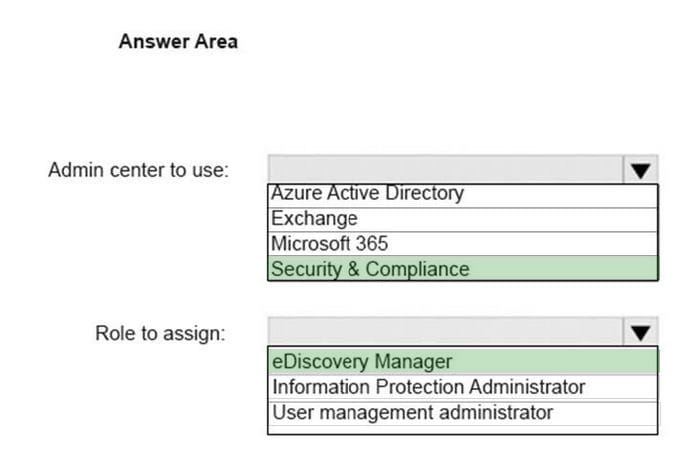
You have a Microsoft 365 subscription.
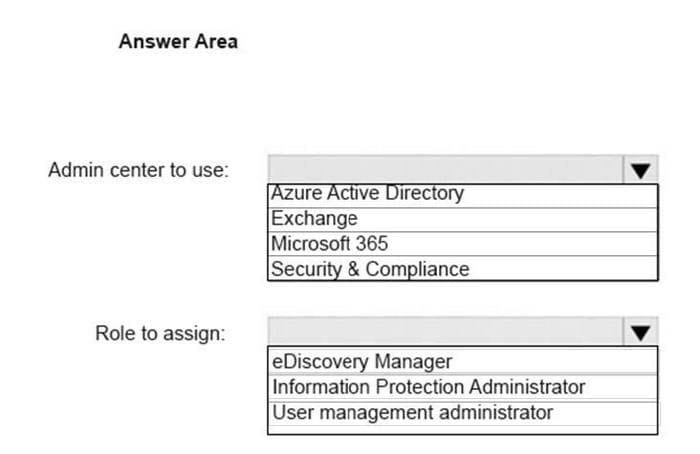
You need to provide an administrator named Admin1 with the ability to place holds on mailboxes, SharePoint Online sites, and OneDrive for Business locations. The solution must use the principle of least privilege.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MS-100 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.