Exam Details
Exam Code
:MS-101Exam Name
:Microsoft 365 Mobility and SecurityCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:525 Q&AsLast Updated
:Apr 11, 2025
Microsoft Microsoft Certifications MS-101 Questions & Answers
-
Question 211:
You have a Microsoft 365 E5 subscription that uses Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).
From Microsoft Defender ATP, you turn on the Allow or block file advanced feature.
You need to block users from downloading a file named File1.exe.
What should you use?
A. a suppression rule
B. an indicator
C. a device configuration profile
-
Question 212:
You have a Microsoft 365 subscription that contains 500 users.
You have several hundred computers that run the 64-bit version of Windows 10 Enterprise and have the following configurations:
1.
Two volumes that contain data
2.
A CPU that has two cores
3.
TPM disabled
4.
4 GB of RAM
All the computers are managed by using Microsoft Intune.
You need to ensure that you can turn on Windows Defender Application Guard on the computers.
What should you do first?
A. Modify the edition of Windows 10.
B. Create an additional volume.
C. Replace the CPU and enable TPM.
D. Replace the CPU and increase the RAM.
-
Question 213:
You have a Microsoft 365 E5 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com.
You need to ensure that users can enroll devices in Microsoft Endpoint Manager without manually entering the address of Microsoft Endpoint Manager.
Which two DNS records should you create? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. a CNAME record for AutoDiscover.contoso.com
B. a CNAME record for EnterpriseEnrollment.contoso.com
C. a TXT record for EnterpriseRegistration.contoso.com
D. an SRV record for _SIP._TLS.contoso.com
E. an SRV record for _SIPfederationTLS.contoso.com
F. a CNAME record for EnterpriseRegistration.contoso.com
G. a TXT record for EnterpriseEnrollment.contoso.com
-
Question 214:
You have two conditional access policies named Policy1 and Policy2.
Policy1 has the following settings:
Assignments:
-Users and groups: User1
-Cloud apps or actions: Office 365 Exchange Online
-Conditions: 0 conditions selected Access controls:
-Grant: Grant access
-Session: 0 controls selected Enable policy: On
Policy2 has the following settings: Assignments:
-Users and groups: User1
-Cloud apps or actions: Office 365 Exchange Online
-Conditions: 0 conditions selected Access controls:
-Grant: Block access
-Session: 0 controls selected Enable policy: On
You need to ensure that User1 can access Microsoft Exchange Online only from devices that are marked as compliant. What should you do?
A. Modify the Grant settings of Policy2.
B. Disable Policy2.
C. Modify the Conditions settings of Policy2.
D. Modify the Grant settings of Policy1.
-
Question 215:
You have an Azure Active Directory (Azure AD) tenant and a Microsoft 365 E5 subscription. The tenant contains the users shown in the following table.
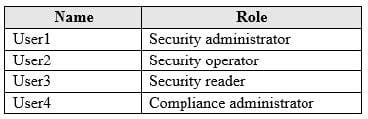
You plan to implement Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).
You verify that role-based access control (RBAC) is turned on in Microsoft Defender ATP.
You need to identify which user can view security incidents from the Microsoft Defender Security Center.
Which user should you identify?
A. User1
B. User2
C. User3
D. User4
-
Question 216:
You have a Microsoft 365 subscription that uses Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).
All the devices in your organization are onboarded to Microsoft Defender ATP.
You need to ensure that an alert is generated if malicious activity was detected on a device during the last 24 hours.
What should you do?
A. From Alerts queue, create a suppression rule and assign an alert
B. From the Security and Compliance admin center, create an audit log search
C. From Advanced hunting, create a query and a detection rule
D. From the Security and Compliance admin center, create a data loss prevention (DLP) policy
-
Question 217:
Your company has a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com.
The tenant is configured to use Azure AD Identity Protection.
You plan to use an application named App1 that creates reports of Azure AD Identity Protection usage.
You register App1 in the tenant.
You need to ensure that App1 can read the risk event information of contoso.com.
To which API should you delegate permissions?
A. Windows Azure Service Management API
B. Windows Azure Active Directory
C. Microsoft Graph
D. Office 365 Management
-
Question 218:
Your company has a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains computers that run Windows 10 Enterprise and are managed by using Microsoft Intune. The computers are configured as shown in the following table.
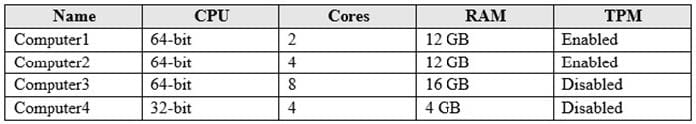
You plan to implement Windows Defender Application Guard for contoso.com.
You need to identify on which two Windows 10 computers Windows Defender Application Guard can be installed.
Which two computers should you identify? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Computer1
B. Computer3
C. Computer2
D. Computer4
-
Question 219:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant that contains a user named User1.
Your company purchases a Microsoft 365 subscription.
You need to ensure that User1 is assigned the required role to create file policies and manage alerts in the Cloud App Security admin center.
Solution: From the Cloud App Security admin center, you assign the App/instance admin role for all Microsoft Online Services to User1.
Does this meet the goal?
A. Yes
B. No
-
Question 220:
You have a Microsoft 365 subscription.
You plan to connect to Microsoft Exchange Online PowerShell and run the following cmdlets:
1.
Search-MailboxAuditLog
2.
Test-ClientAccessRule
3.
Set-GroupMailbox
4.
Get-Mailbox
Which cmdlet will generate an entry in the Microsoft Office 365 audit log?
A. Search-MailboxAuditLog
B. Test-ClientAccessRule
C. Set-GroupMailbox
D. Get-Mailbox
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MS-101 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.