Exam Details
Exam Code
:MS-102Exam Name
:Microsoft 365 Certified: Enterprise Administrator ExpertCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:496 Q&AsLast Updated
:Apr 02, 2025
Microsoft Microsoft Certifications MS-102 Questions & Answers
-
Question 101:
You have a Microsoft 365 subscription.
You discover that some external users accessed center for a Microsoft SharePoint site.
You modify the sharePoint sharing policy to prevent sharing, outside your organization.
You need to be notified if the SharePoint sharing policy is modified in the future.
Solution: From the Security $ Compliance admin center you create a threat management policy.
Does this meet the goal?
A. Yes
B. No
-
Question 102:
You have a Microsoft 365 subscription.
You create a retention label named Retention1 as shown in the following exhibit.
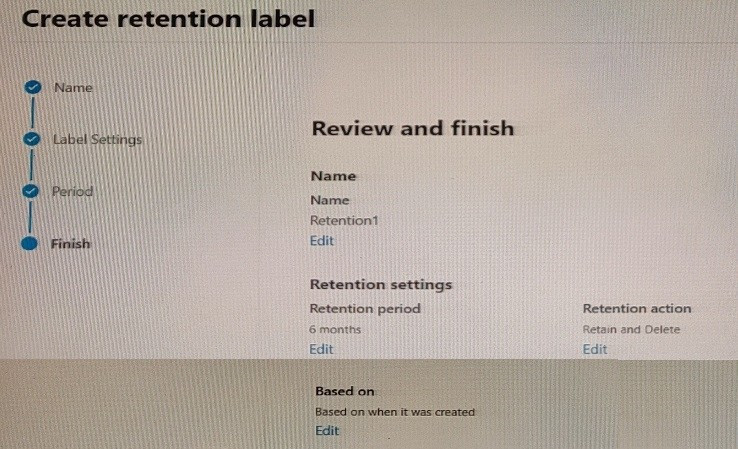
You apply Retention! to all the Microsoft OneDrive content.
On January 1, 2020, a user stores a file named File1 in OneDrive.
On January 10, 2020, the user modifies File1.
On February 1, 2020, the user deletes File1.
When will File1 be removed permanently and unrecoverable from OneDrive?
A. February 1, 2020
B. July 1.2020
C. July 10, 2020
D. August 1, 2020
-
Question 103:
You have a new Microsoft 365 E5 tenant.
You need to enable an alert policy that will be triggered when an elevation of Microsoft Exchange Online administrative privileges is detected.
What should you do first?
A. Enable auditing.
B. Enable Microsoft 365 usage analytics.
C. Create an Insider risk management policy.
D. Create a communication compliance policy.
-
Question 104:
You have a Microsoft 365 tenant that contains a Windows 10 device named Device1 and the Microsoft Endpoint Manager policies shown in the following table.
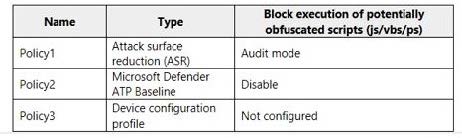
A. only the settings of Policy!
B. only the settings of Policy2
C. only the settings of Policy3
D. no settings
-
Question 105:
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps.
You need to be notified when a single user downloads more than 50 files during any 60- second period. What should you configure?
A. a session policy
B. a file policy
C. an activity policy
D. an anomaly detection policy
-
Question 106:
You have a Microsoft 365 E5 subscription.
Users have the devices shown in the following table.

On which devices can you manage apps by using app configuration policies in Microsoft Endpoint Manager?
A. Device1, Device4, and Device6
B. Device2, Device3, and Device5
C. Device1, Device2, Device3, and Device6
D. Device1, Device2, Device4, and Device5
-
Question 107:
You have a Microsoft 365 E5 subscription.
Conditional Access is configured to block high-risk sign-ins for all users.
All users are in France and are registered for multi-factor authentication (MFA).
Users in the media department will travel to various countries during the next month.
You need to ensure that if the media department users are blocked from signing in while traveling, the users can remediate the issue without administrator intervention.
What should you configure?
A. an exclusion group
B. the MFA registration policy
C. named locations
D. self-service password reset (SSPR)
-
Question 108:
You have a Microsoft 365 subscription.
Your company has a customer ID associated to each customer. The customer IDs contain 10 numbers followed by 10 characters. The following is a sample customer ID: 12-456-7890-abc-de- fghij.
You plan to create a data loss prevention (DLP) policy that will detect messages containing customer IDs.
D18912E1457D5D1DDCBD40AB3BF70D5D
What should you create to ensure that the DLP policy can detect the customer IDs?
A. a sensitive information type
B. a sensitivity label
C. a supervision policy
D. a retention label
-
Question 109:
You have a Microsoft 365 E5 subscription.
You need to compare the current Safe Links configuration to the Microsoft recommended configurations.
What should you use?
A. Microsoft Purview
B. Azure AD Identity Protection
C. Microsoft Secure Score
D. the configuration analyzer
-
Question 110:
You have a Microsoft 365 E5 subscription.
All users have Mac computers. All the computers are enrolled in Microsoft Endpoint Manager and onboarded to Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).
You need to configure Microsoft Defender ATP on the computers.
What should you create from the Endpoint Management admin center?
A. a device configuration profile
B. an update policy for iOS
C. a Microsoft Defender ATP baseline profile
D. a mobile device management (MDM) security baseline profile
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MS-102 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.