Exam Details
Exam Code
:MS-102Exam Name
:Microsoft 365 Certified: Enterprise Administrator ExpertCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:496 Q&AsLast Updated
:Apr 10, 2025
Microsoft Microsoft Certifications MS-102 Questions & Answers
-
Question 131:
You have a Microsoft 365 E5 tenant that contains the devices shown in the following table.
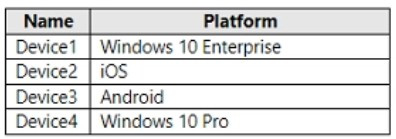
The devices are managed by using Microsoft Intune.
You plan to use a configuration profile to assign the Delivery Optimization settings.
Which devices will support the settings?
A. Device1 only
B. Device1 and Device4
C. Device1, Device3, and Device4
D. Device1, Device2, Device3, and Device4
-
Question 132:
You have a Microsoft 365 E5 subscription that contains the following user:
Name: User1 UPN: [email protected] Email address: [email protected] MFA enrollment status: Disabled When User1 attempts to sign in to Outlook on the web by using the [email protected] email address, the user cannot sign in.
You need to ensure that User1 can sign in to Outlook on the web by using [email protected]. What should you do?
A. Assign an MFA registration policy to User1.
B. Reset the password of User1.
C. Add an alternate email address for User1.
D. Modify the UPN of User1.
-
Question 133:
Your company has a Microsoft 365 E5 subscription.
Users in the research department work with sensitive data.
You need to prevent the research department users from accessing potentially unsafe websites by using hyperlinks embedded in email messages and documents. Users in other departments must not be restricted.
What should you do?
A. Create a data loss prevention (DLP) policy that has a Content is shared condition.
B. Modify the safe links policy Global settings.
C. Create a data loss prevention (DLP) policy that has a Content contains condition.
D. Create a new safe links policy.
-
Question 134:
You have a Microsoft 365 subscription.
All users have their email stored in Microsoft Exchange Online.
In the mailbox of a user named User1. you need to preserve a copy of all the email messages that contain the word ProjectX.
What should you do first?
A. From the Exchange admin center create a mail flow rule.
B. From Microsoft 365 Defender, start a message trace.
C. From Microsoft Defender for Cloud Apps, create an activity policy.
D. From the Microsoft Purview compliance portal, create a label and a label policy.
-
Question 135:
You have a Microsoft 365 tenant that is signed up for Microsoft Store for Business and contains a user named User1. You need to ensure that User1 can perform the following tasks in Microsoft Store for Business:
Assign licenses to users.
Procure apps from Microsoft Store.
Manage private store availability for all items.
The solution must use the principle of least privilege.
Which Microsoft Store for Business role should you assign to User1?
A. Basic Purchaser
B. Device Guard signer
C. Admin
D. Purchaser
-
Question 136:
You have a Microsoft Azure Active Directory (Azure AD) tenant named Contoso.com.
You create a Microsoft Defender for identity instance Contoso.
The tenant contains the users shown in the following table.

You need to modify the configuration of the Defender for identify sensors.
Solutions: You instruct User3 to modify the Defender for identity sensor configuration.
Does this meet the goal?
A. Yes
B. No
-
Question 137:
Your company has a Microsoft E5 tenant.
The company must meet the requirements of the ISO/IEC 27001:2013 standard.
You need to assess the company's current state of compliance.
What should you use?
A. eDiscovery
B. Information governance
C. Compliance Manager
D. Data Subject Requests (DSRs)
-
Question 138:
You have a Microsoft 365 subscription that contains a user named User1.
You need to ensure that User1 can search the Microsoft 365 audit logs from the Security and Compliance admin center.
Which role should you assign to User1?
A. View-Only Audit Logs in the Security and Compliance admin center
B. View-Only Audit Logs in the Exchange admin center
C. Security reader in the Azure Active Directory admin center
D. Security Reader in the Security and Compliance admin center
-
Question 139:
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains the users shown in the following table.

The domain syncs to an Azure AD tenant named contoso.com as shown in the exhibit. (Click the Exhibit tab.)
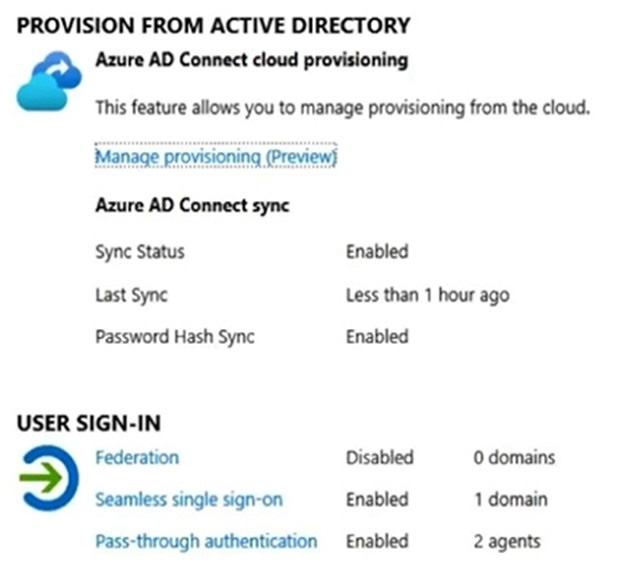
User2 fails to authenticate to Azure AD when signing in as [email protected].
You need to ensure that User2 can access the resources in Azure AD.
Solution: From the Microsoft Entra admin center, you assign User2 the Security Reader role. You instruct User2 to sign in as [email protected].
Does this meet the goal?
A. Yes
B. No
-
Question 140:
You have a Microsoft 365 E5 subscription that uses Microsoft intune.
in the Microsoft Endpoint Manager admin center, you discover many stale and inactive devices,
You enable device clean-up rules
What can you configure as the minimum number of days before a device a removed automatically?
A. 10
B. 30
C. 45
D. 90
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MS-102 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.