Exam Details
Exam Code
:N10-007Exam Name
:CompTIA Network+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1251 Q&AsLast Updated
:Jun 30, 2025
CompTIA CompTIA Certifications N10-007 Questions & Answers
-
Question 1:
A network technician is reviewing network logs and notices about 30,000 different hosts have been trying to hit the company employees' database server for the past week. However, none of the hosts are known to the network. Which of the following is MOST likely occurring within the network?
A. ARP poisoning
B. Brute forcing
C. SQL injection
D. Distributed DoS
-
Question 2:
A network administrator discovered a rogue access point was sending a signal from inside the corporate headquarters. Which of the following would prevent the access point from providing access to the company's internal network?
A. Disabling unnecessary services
B. Placing unused ports in a separate VLAN
C. Enabling BPDU guard
D. Configuring a geofence at the corporate boundary
-
Question 3:
A network manager has received reports that some employees have been using the company's WiFi to log onto their social media accounts from their personal devices. The network manager is looking for a solution to prevent this type of activity. The Chief Information Officer (CIO) wants to continue using a pre- shared key and add an additional layer of security to allow only authorized users to authenticate to the WiFi. Which of the following solutions would address this request? (Choose two.)
A. Port security
B. MAC filtering
C. Geofencing
D. 802.1X
E. Proxy server
F. SSO
-
Question 4:
A technician set up a small network, which is not connected to the company LAN, for several employees to play a peer-to-peer networking game during breaks. The users know how to set up the software, but they do not know anything about networking. The technician has wired the network but has not configured any networking information and does not want the employees to have access outside the network. Which of the following should be used to apply addressing to the network?
A. NAT
B. VLSM
C. APIPA
D. CIDR
-
Question 5:
Given the table below:
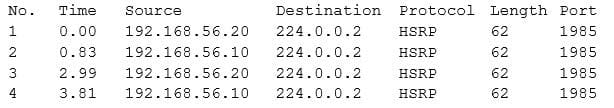
Which of the following describes the output?
A. Error rate
B. Network baseline
C. Traffic analysis
D. Port scan
-
Question 6:
Which of the following are reasons for enabling jumbo frames? (Choose two.)
A. To increase payload size
B. To increase bandwidth
C. To provide additional SANs storage capacity
D. To implement larger SQL queries
E. To reduce CPU overhead
-
Question 7:
Ann, a network technician, set up a new server and enabled the host-based firewall. She attempts to connect to the server from several different workstations using RDP but is not successful. Which of the following ports on the firewall should she verify is open?
A. 22
B. 389
C. 443
D. 3389
-
Question 8:
A network administrator is setting up a wireless network with poor security for a computer science class to hack. Which of the following security methods would be MOST easily circumvented?
A. MAC filtering
B. WPA
C. WPA2
D. Shared key
-
Question 9:
A network administrator has set up a corporate network at a branch office. Users are able to log into the wireless network with their network credentials after they accept the company root certificate. Which of the following is the wireless network MOST likely using?
A. WPA2 Enterprise with PSK
B. WPA2 Personal with PEAP
C. WPA2 Enterprise with Kerberos
D. WPA2 Personal with LEAP
-
Question 10:
An organization wants to implement a method of centrally managing logins to network services. Which of the following protocols should the organization use to allow for authentication, authorization, and auditing?
A. MS-CHAP
B. RADIUS
C. LDAPS
D. RSTP
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your N10-007 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.