Exam Details
Exam Code
:N10-008Exam Name
:CompTIA Network+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1219 Q&AsLast Updated
:Feb 16, 2025
CompTIA CompTIA Certifications N10-008 Questions & Answers
-
Question 1141:
The following instructions were published about the proper network configuration for a videoconferencing device:
"Configure a valid static RFC1918 address accordingly to your network. Check the option to use a connection over NAT".
Which of the following is a valid IP address configuration for the device?
A. FE80::1
B. 100.64.0.1
C. 169.254.1.2
D. 172.19.0.2
E. 224.0.0.12
-
Question 1142:
Which of the following use cases would justify the deployment of an mGRE hub-and-spoke topology?
A. An increase in network securing using encryption and packet encapsulation
B. A network expansion caused by an increase in the number of branch locations to the headquarters
C. A mandatory requirement to increase the deployment of an SDWAN network.
D. An improvement in network efficiency by increasing the useful packet payload.
-
Question 1143:
A network administrator needs to extend an organization's network to a nearby building that has unused SMF already installed. The network administrator has decided to create a switch-to-switch uplink. Which of the following standards would be the BEST to use?
A. 10BASE-T
B. 100BASE-T
C. 1000BASE-LX
D. 1000BASE-SX
-
Question 1144:
A security team needs to restrict access to a wireless network in a certain area. Which of the following would be used to enforce this restriction?
A. Geofencing
B. WPA2-PSK
C. EAP-TLS
D. VLAN tagging
-
Question 1145:
Given the following information:
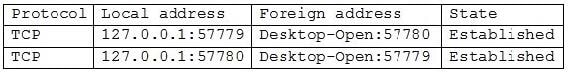
Which of the following command-line tools would generate this output?
A. netstat
B. arp
C. dig
D. tracert
-
Question 1146:
Which of the following provides redundancy on a file server to ensure the server is still connected to a LAN even in the event of a port failure on a switch?
A. NIC teaming
B. Load balancer
C. RAID array
D. PDUs
-
Question 1147:
Which of the following technologies is used to translate one public IP address to multiple private IP addresses?
A. NAT
B. ARP
C. DHCP
D. DNS
-
Question 1148:
A systems administrator is running a VoIP network and is experiencing jitter and high latency. Which of the following would BEST help the administrator determine the cause of these issues?
A. Enabling RADIUS on the network.
B. Configuring SNMP traps on the network.
C. Implementing LDAP on the network.
D. Establishing NTP on the network.
-
Question 1149:
A Chief Information Officer (CIO) is reviewing a proposal to provide access security for the IT department's restricted area. Which of the following is a preventive measure that should be implemented?
A. Motion detection
B. Cameras
C. Biometric lock
D. Asset tags
-
Question 1150:
Which of the following attacks blocks access to resources by flooding that resource with invalid requests?
A. On-path attack
B. IP spoofing attack
C. DoS attack
D. DNS poisoning attack
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your N10-008 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.