Exam Details
Exam Code
:NS0-527Exam Name
:NetApp Certified Implementation Engineer - Data ProtectionCertification
:NetApp CertificationsVendor
:NetAppTotal Questions
:156 Q&AsLast Updated
:Mar 27, 2025
NetApp NetApp Certifications NS0-527 Questions & Answers
-
Question 71:
Using ONTAPSystem Manager, you are asked to replicate all the volumes contained in a Storage VM to a remote ONTAP 9.7 system for quick disaster recovery. Which two steps need to be completed to accomplish this task? (Choose two.)
A. Create a SnapMirror relationshipfor each volume.
B. Create a cluster peering relationship.
C. Create an SVM-DR relationship.
D. Create an SVM peering relationship.
-
Question 72:
A customer is planning the cloud strategy for their Microsoft SQLdatabases and must be able to protect them from outages. They are planning on using multiple cloud providers for their solution with their current NetApp storage system.
In this scenario, which two products are required to satisfy their backup managementneeds? (Choose two.)
A. Cloud Volumes ONTAP
B. SnapCenter
C. CloudSync
D. FlashPool
-
Question 73:
A customer has a new cloud strategy. They want to replicate mission-critical SAN volumes to the cloud for DR. Which NetApp technology satisfies the requirement?
A. Cloud Sync service
B. Fabric Pool technology
C. Cloud Volumes Service
D. Cloud Volumes ONTAP
-
Question 74:
Click the Exhibit button.
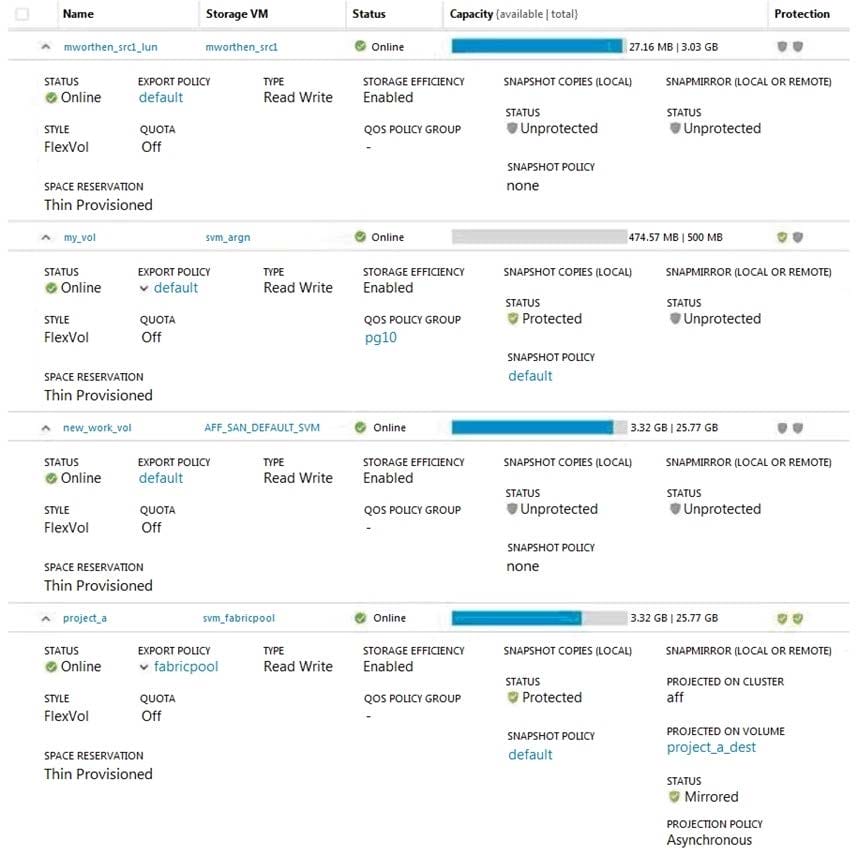
Referring to the exhibit, which volume has the highest level of protection assigned to it?
A. project_a
B. mworthen_src1_lun
C. my_vol
D. new_work_vol
-
Question 75:
Click the Exhibit button.
Your customer wants to protect a volume and replicate it to a secondary volume. The customer has tried to configure this relationship using OnCommand System Manager. Upon reviewing this newly configured relationship, you discover that the configuration does not satisfy the customer's stated requirements.
Referring to the exhibit, what should you do to ensure that the volume is protected?
A. Deletethe relationship and recreate it.
B. Resynchronize the relationship.
C. Initialize the relationship.
D. Change the schedule to hourly.
-
Question 76:
You want to set up an important management solution that must comply with FIPS 140-2. The solution should support a multi-clusters environment and should provide centralized management of the encryption keys.
In this scenario, which solution accomplishes the task?
A. NetApp Storage Encryption (NSE)with external key management using the Key Management Interoperability Protocol (KMIP)
B. NetApp Volume Encryption (NVE) with onboard key manager using the Key Management Interoperability Protocol (KMIP)
C. NetApp Storage Encryption (NSE) with onboard keymanager using the Key Management Interoperability Protocol (KMIP)
D. NetApp Volume Encryption (NVE) with external key management server using the Key Management Interoperability Protocol (KMIP)
-
Question 77:
Your customer is running an older cluster that uses Data ONTAP 8.1 Cluster-Mode. They would like to create a SnapMirror relationship with their new ONTAP 9.5 cluster.
In this scenario, what must the customer do tocreate the SnapMirror relationship?
A. The customer can create a DP type SnapMirror relationship without needing to perform an upgrade.
B. The customer must first upgrade the Data ONTAP 8.1 Cluster-Mode storage array to at least ONTAP 9.1 and then createthe XDP SnapMirror relationship.
C. The customer must first upgrade the Data ONTAP 8.1 Cluster-Mode storage array to at least ONTAP 8.3 and then create the XDP SnapMirror relationship.
D. The customer can create a XDP type SnapMirror relationship withoutneeding to perform an upgrade.
-
Question 78:
A company just installed SnapCenter to help manage their ONTAP 9.7 environment. The database administrator wants to add new volumes withLUNs for a 10 TB Oracle database. Which two tools would accomplish this task? (Choose two.)
A. SnapCenter Plug-in for Oracle Database
B. OnCommand Insight
C. ONTAP System Manager
D. Active IQ Unified Manager
-
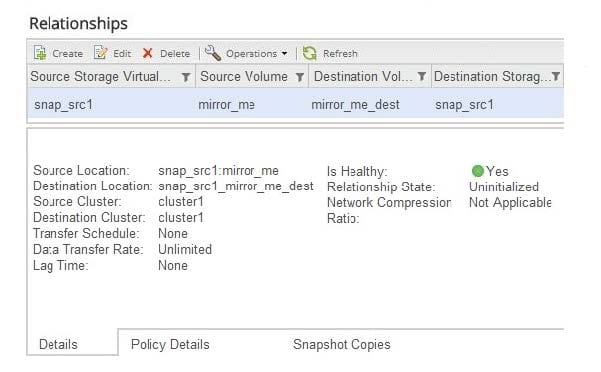
Question 79:
Click the Exhibit button.

Referring to the exhibit, which two statements are true? (Choosetwo.)
A. The source volume is available for I/O.
B. A manual re-synchronization is not needed.
C. The source volume is unavailable for I/O
D. A manual re-synchronization is needed.
-
Question 80:
You are asked to protect your customer's Exchange environment. You deploy SnapCenter 4.1 and the plug-in for Microsoft Exchange Server. While creating the backup policy, you select the Full and Log Backup from the list of supported backup types.
In this scenario, what would the Full and Log Backup type allow you to protect within Exchange?
A. all databases but no transaction logs
B. all databases and all transaction logs
C. all uncommitted transaction logs and all of the databases
D. all transaction logs but none of thedatabases
Related Exams:
NS0-002
NetApp Certified Technology Associate - NCSA - HCNS0-003
NetApp Certified Technology AssociateNS0-004
NetApp Certified Technology Solutions ProfessionalNS0-093
NetApp Accredited Hardware Support EngineerNS0-101
NetApp Accredited Sales ProfessionalNS0-111
Network Appliance Storage AssociateNS0-120
Data ONTAP AdvancedNS0-121
Network Appliance Data ONTAP Advanced Exam 7GNS0-130
Storage Professional Data ProtectionNS0-131
Network Appliance Data Protection Exam 7G
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only NetApp exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NS0-527 exam preparations and NetApp certification application, do not hesitate to visit our Vcedump.com to find your solutions here.