Exam Details
Exam Code
:PT0-002Exam Name
:CompTIA PenTest+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:455 Q&AsLast Updated
:Apr 13, 2025
CompTIA CompTIA Certifications PT0-002 Questions & Answers
-
Question 201:
A final penetration test report has been submitted to the board for review and accepted. The report has three findings rated high. Which of the following should be the NEXT step?
A. Perform a new penetration test.
B. Remediate the findings.
C. Provide the list of common vulnerabilities and exposures.
D. Broaden the scope of the penetration test.
-
Question 202:
When planning a penetration-testing effort, clearly expressing the rules surrounding the optimal time of day for test execution is important because:
A. security compliance regulations or laws may be violated.
B. testing can make detecting actual APT more challenging.
C. testing adds to the workload of defensive cyber- and threat-hunting teams.
D. business and network operations may be impacted.
-
Question 203:
A client evaluating a penetration testing company requests examples of its work. Which of the following represents the BEST course of action for the penetration testers?
A. Redact identifying information and provide a previous customer's documentation.
B. Allow the client to only view the information while in secure spaces.
C. Determine which reports are no longer under a period of confidentiality.
D. Provide raw output from penetration testing tools.
-
Question 204:
An Nmap scan of a network switch reveals the following:
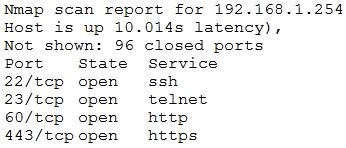
Which of the following technical controls will most likely be the FIRST recommendation for this device?
A. Encrypted passwords
B. System-hardening techniques
C. Multifactor authentication
D. Network segmentation
-
Question 205:
During an assessment, a penetration tester found a suspicious script that could indicate a prior compromise. While reading the script, the penetration tester noticed the following lines of code:
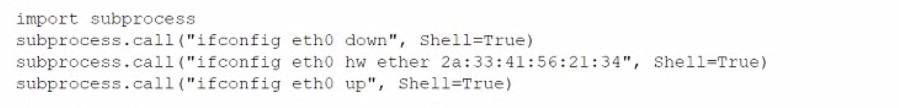
Which of the following was the script author trying to do?
A. Spawn a local shell.
B. Disable NIC.
C. List processes.
D. Change the MAC address
-
Question 206:
Which of the following commands will allow a penetration tester to permit a shell script to be executed by the file owner?
A. chmod u+x script.sh
B. chmod u+e script.sh
C. chmod o+e script.sh
D. chmod o+x script.sh
-
Question 207:
A penetration tester will be performing a vulnerability scan as part of the penetration test on a client's website. The tester plans to run several Nmap scripts that probe for vulnerabilities while avoiding detection. Which of the following Nmap options will the penetration tester MOST likely utilize?
A. -8 -T0
B. --script "http*vuln*"
C. -sn
D. -O -A
-
Question 208:
A penetration tester is trying to restrict searches on Google to a specific domain. Which of the following commands should the penetration tester consider?
A. inurl:
B. link:
C. site:
D. intitle:
-
Question 209:
A penetration tester who is performing an engagement notices a specific host is vulnerable to EternalBlue. Which of the following would BEST protect against this vulnerability?
A. Network segmentation
B. Key rotation
C. Encrypted passwords
D. Patch management
-
Question 210:
An organization wants to identify whether a less secure protocol is being utilized on a wireless network. Which of the following types of attacks will achieve this goal?
A. Protocol negotiation
B. Packet sniffing
C. Four-way handshake
D. Downgrade attack
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.