Exam Details
Exam Code
:PT0-002Exam Name
:CompTIA PenTest+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:455 Q&AsLast Updated
:Apr 13, 2025
CompTIA CompTIA Certifications PT0-002 Questions & Answers
-
Question 251:
Which of the following documents describes activities that are prohibited during a scheduled penetration test?
A. MSA
B. NDA
C. ROE
D. SLA
-
Question 252:
Performing a penetration test against an environment with SCADA devices brings additional safety risk because the:
A. devices produce more heat and consume more power.
B. devices are obsolete and are no longer available for replacement.
C. protocols are more difficult to understand.
D. devices may cause physical world effects.
-
Question 253:
In Python socket programming, SOCK_DGRAM type is:
A. reliable.
B. matrixed.
C. connectionless.
D. slower.
-
Question 254:
A penetration tester conducts an Nmap scan against a target and receives the following results:

Which of the following should the tester use to redirect the scanning tools using TCP port 1080 on the target?
A. Nessus
B. ProxyChains
C. OWASPZAP
D. Empire
-
Question 255:
During a code review assessment, a penetration tester finds the following vulnerable code inside one of the web application files:
<% String id = request.getParameter("id"); %>
Employee ID: <%= id %>
Which of the following is the best remediation to prevent a vulnerability from being exploited, based on this code?
A. Parameterized queries
B. Patch application
C. Output encoding
-
Question 256:
A security company has been contracted to perform a scoped insider-threat assessment to try to gain access to the human resources server that houses PII and salary data. The penetration testers have been given an internal network starting position.
Which of the following actions, if performed, would be ethical within the scope of the assessment?
A. Exploiting a configuration weakness in the SQL database
B. Intercepting outbound TLS traffic
C. Gaining access to hosts by injecting malware into the enterprise-wide update server
D. Leveraging a vulnerability on the internal CA to issue fraudulent client certificates
E. Establishing and maintaining persistence on the domain controller
-
Question 257:
A penetration tester is starting an assessment but only has publicly available information about the target company. The client is aware of this exercise and is preparing for the test. Which of the following describes the scope of the assessment?
A. Partially known environment testing
B. Known environment testing
C. Unknown environment testing
D. Physical environment testing
-
Question 258:
Which of the following concepts defines the specific set of steps and approaches that are conducted during a penetration test?
A. Scope details
B. Findings
C. Methodology
D. Statement of work
-
Question 259:
A penetration tester has gained access to part of an internal network and wants to exploit on a different network segment. Using Scapy, the tester runs the following command:
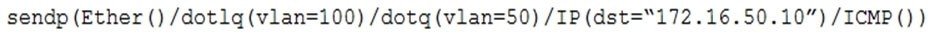
Which of the following represents what the penetration tester is attempting to accomplish?
A. DNS cache poisoning
B. MAC spoofing
C. ARP poisoning
D. Double-tagging attack
-
Question 260:
A penetration tester is looking for a vulnerability that enables attackers to open doors via a specialized TCP service that is used for a physical access control system. The service exists on more than 100 different hosts, so the tester would like to automate the assessment. Identification requires the penetration tester to: Have a full TCP connection Send a "hello" payload Walt for a response Send a string of characters longer than 16 bytes
Which of the following approaches would BEST support the objective?
A. Run nmap –Pn –sV –script vuln
. B. Employ an OpenVAS simple scan against the TCP port of the host.
C. Create a script in the Lua language and use it with NSE.
D. Perform a credentialed scan with Nessus.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.