Exam Details
Exam Code
:PT0-002Exam Name
:CompTIA PenTest+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:455 Q&AsLast Updated
:Apr 13, 2025
CompTIA CompTIA Certifications PT0-002 Questions & Answers
-
Question 291:
Penetration tester who was exclusively authorized to conduct a physical assessment noticed there were no cameras pointed at the dumpster for company. The penetration tester returned at night and collected garbage that contained receipts for recently purchased networking :. The models of equipment purchased are vulnerable to attack. Which of the following is the most likely next step for the penetration?
A. Alert the target company of the discovered information.
B. Verify the discovered information is correct with the manufacturer.
C. Scan the equipment and verify the findings.
D. Return to the dumpster for more information.
-
Question 292:
Which of the following should a penetration tester attack to gain control of the state in the HTTP protocol after the user is logged in?
A. HTTPS communication
B. Public and private keys
C. Password encryption
D. Sessions and cookies
-
Question 293:
After compromising a system, a penetration tester wants more information in order to decide what actions to take next. The tester runs the following commands:
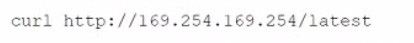
Which of the following attacks is the penetration tester most likely trying to perform?
A. Metadata service attack
B. Container escape techniques
C. Credential harvesting
D. Resource exhaustion
-
Question 294:
During a client engagement, a penetration tester runs the following Nmap command and obtains the following output:
nmap -sV -- script ssl-enum-ciphers -p 443 remotehost
| TLS_ECDHE_ECDSA_WITH_RC4_128_SHA
| TLS_ECDHE_RSA_WITH_RC4_128_SHA
TLS_RSA_WITH_RC4_128_SHA (rsa 2048)
TLS_RSA_WITH_RC4_128_MD5 (rsa 2048)
Which of the following should the penetration tester include in the report?
A. Old, insecure ciphers are in use.
B. The 3DES algorithm should be deprecated.
C. 2,048-bit symmetric keys are incompatible with MD5.
D. This server should be upgraded to TLS 1.2.
-
Question 295:
Which of the following are the MOST important items to include in the final report for a penetration test? (Choose two.)
A. The CVSS score of the finding
B. The network location of the vulnerable device
C. The vulnerability identifier
D. The client acceptance form
E. The name of the person who found the flaw
F. The tool used to find the issue
-
Question 296:
A penetration tester conducted an assessment on a web server. The logs from this session show the following: http://www.thecompanydomain.com/servicestatus.php?serviceID=892andserviceID=892 ` ; DROP TABLE SERVICES; -Which of the following attacks is being attempted?
A. Clickjacking
B. Session hijacking
C. Parameter pollution
D. Cookie hijacking
E. Cross-site scripting
-
Question 297:
Which of the following is the most secure method for sending the penetration test report to the client?
A. Sending the penetration test report on an online storage system.
B. Sending the penetration test report inside a password-protected ZIP file.
C. Sending the penetration test report via webmail using an HTTPS connection.
D. Encrypting the penetration test report with the client's public key and sending it via email.
-
Question 298:
A penetration tester has completed an analysis of the various software products produced by the company under assessment. The tester found that over the past several years the company has been including vulnerable third-party modules in multiple products, even though the quality of the organic code being developed is very good. Which of the following recommendations should the penetration tester include in the report?
A. Add a dependency checker into the tool chain.
B. Perform routine static and dynamic analysis of committed code.
C. Validate API security settings before deployment.
D. Perform fuzz testing of compiled binaries.
-
Question 299:
During the assessment of a client's cloud and on-premises environments, a penetration tester was able to gain ownership of a storage object within the cloud environment using the provided on-premises credentials. Which of the following best describes why the tester was able to gain access?
A. Federation misconfiguration of the container
B. Key mismanagement between the environments
C. laaS failure at the provider
D. Container listed in the public domain
-
Question 300:
A penetration tester has identified several newly released CVEs on a VoIP call manager. The scanning tool the tester used determined the possible presence of the CVEs based off the version number of the service. Which of the following methods would BEST support validation of the possible findings?
A. Manually check the version number of the VoIP service against the CVE release
B. Test with proof-of-concept code from an exploit database
C. Review SIP traffic from an on-path position to look for indicators of compromise
D. Utilize an nmap -sV scan against the service
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.