Exam Details
Exam Code
:PT0-002Exam Name
:CompTIA PenTest+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:455 Q&AsLast Updated
:Mar 28, 2025
CompTIA CompTIA Certifications PT0-002 Questions & Answers
-
Question 361:
A penetration tester is enumerating shares and receives the following output:
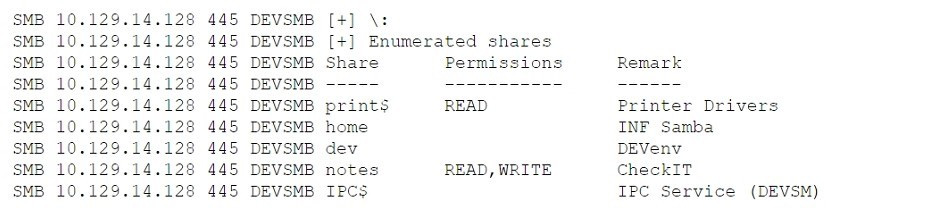
Which of the following should the penetration tester enumerate next?
A. dev
B. print$
C. home
D. notes
-
Question 362:
During a test of a custom-built web application, a penetration tester identifies several vulnerabilities. Which of the following would be the most interested in the steps to reproduce these vulnerabilities?
A. Operations staff
B. Developers
C. Third-party stakeholders
D. C-suite executives
-
Question 363:
A penetration tester wants to find the password for any account in the domain without locking any of the accounts. Which of the following commands should the tester use?
A. enum4linux -u userl -p /passwordList.txt 192.168.0.1
B. enum4linux -u userl -p Passwordl 192.168.0.1
C. cme smb 192.168.0.0/24 -u /userList.txt -p /passwordList.txt
D. cme smb 192.168.0.0/24 -u /userList.txt -p Summer123
-
Question 364:
Which of the following tools would help a penetration tester locate a file that was uploaded to a content management system?
A. DirBuster
B. Open VAS
C. Scout Suite
D. CeWL
-
Question 365:
Which of the following describes a globally accessible knowledge base of adversary tactics and techniques based on real-world observations?
A. OWASP Top 10
B. MITRE ATTandCK
C. Cyber Kill Chain
D. Well-Architected Framework
-
Question 366:
Given the following code:
$p = (80, 110, 25)
$network = (192.168.0)
$range = 1 .. 254
$ErrorActionPreference = 'silentlycontinue'
$Foreach ($add in $range)
$Foreach ($x in $p)
{ {$ip = "{0} . {1} -F $network, $add"
If (Test-Connection -BufferSize 32 -Count 1 -quiet -ComputerName $ip)
{$socket = new-object System.Net. Sockets. TcpClient (andip, $x)
If ($socket. Connected) { $ip $p open"
$socket. Close () }
}
}}
Which of the following tasks could be accomplished with the script?
A. Reverse shell
B. Ping sweep
C. File download
D. Port scan
-
Question 367:
In Java and C/C++, variable initialization is critical because:
A. the unknown value, when used later, will cause unexpected behavior.
B. the compiler will assign null to the variable, which will cause warnings and errors.
C. the initial state of the variable creates a race condition.
D. the variable will not have an object type assigned to it.
-
Question 368:
A security engineer is trying to bypass a network IPS that isolates the source when the scan exceeds 100 packets per minute. The scope of the scan is to identify web servers in the 10.0.0.0/16 subnet. Which of the following commands should the engineer use to achieve the objective in the least amount of time?
A. nmap -T3 -p 80 10.0.0.0/16 -- max-hostgroup 100
B. nmap -TO -p 80 10.0.0.0/16
C. nmap -T4 -p 80 10.0.0.0/16 -- max-rate 60
D. nmap -T5 -p 80 10.0.0.0/16 -- min-rate 80
-
Question 369:
Which of the following documents would be the most helpful in determining who is at fault for a temporary outage that occurred during a penetration test?
A. Non-disclosure agreement
B. Business associate agreement
C. Assessment scope and methodologies
D. Executive summary
-
Question 370:
Which of the following members of a client organization are most likely authorized to provide a signed authorization letter prior to the start date of a penetration test?
A. The IT department
B. The executive management team and legal personnel
C. Organizational security personnel
D. The human resources team
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.