Exam Details
Exam Code
:PT0-003Exam Name
:CompTIA PenTest+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:271 Q&AsLast Updated
:Mar 21, 2025
CompTIA CompTIA Certifications PT0-003 Questions & Answers
-
Question 41:
Company.com has hired a penetration tester to conduct a phishing test. The tester wants to set up a fake log-in page and harvest credentials when target employees click on links in a phishing email. Which of the following commands would best help the tester determine which cloud email provider the log-in page needs to mimic?
A. dig company.com MX
B. whois company.com
C. cur1 www.company.com
D. dig company.com A
-
Question 42:
An assessor wants to use Nmap to help map out a stateful firewall rule set. Which of the following scans will the assessor MOST likely run?
A. nmap 192.168.0.1/24
B. nmap 192.168.0.1/24
C. nmap oG 192.168.0.1/24
D. nmap 192.168.0.1/24
-
Question 43:
Given the following output:
User-agent:* Disallow: /author/
Disallow: /xmlrpc.php
Disallow: /wp-admin
Disallow: /page/
During which of the following activities was this output MOST likely obtained?
A. Website scraping
B. Website cloning
C. Domain enumeration
D. URL enumeration
-
Question 44:
A penetration tester found several critical SQL injection vulnerabilities during an assessment of a client's system. The tester would like to suggest mitigation to the client as soon as possible.
Which of the following remediation techniques would be the BEST to recommend? (Choose two.)
A. Closing open services
B. Encryption users' passwords
C. Randomizing users' credentials
D. Users' input validation
E. Parameterized queries
F. Output encoding
-
Question 45:
A penetration tester has been given eight business hours to gain access to a client's financial system. Which of the following techniques will have the highest likelihood of success?
A. Attempting to tailgate an employee going into the client's workplace
B. Dropping a malicious USB key with the company's logo in the parking lot
C. Using a brute-force attack against the external perimeter to gain a foothold
D. Performing spear phishing against employees by posing as senior management
-
Question 46:
During an assessment, a penetration tester obtains a list of 30 email addresses by crawling the target company's website and then creates a list of possible usernames based on the email address format. Which of the following types of attacks would MOST likely be used to avoid account lockout?
A. Mask
B. Rainbow
C. Dictionary
D. Password spraying
-
Question 47:
A penetration tester initiated the transfer of a large data set to verify a proof-of-concept attack as permitted by the ROE. The tester noticed the client's data included PII, which is out of scope, and immediately stopped the transfer. Which of the following MOST likely explains the penetration tester's decision?
A. The tester had the situational awareness to stop the transfer.
B. The tester found evidence of prior compromise within the data set.
C. The tester completed the assigned part of the assessment workflow.
D. The tester reached the end of the assessment time frame.
-
Question 48:
A penetration tester is conducting an assessment on 192.168.1.112. Given the following output:
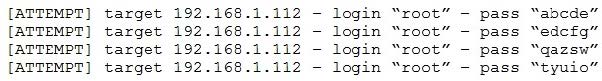
Which of the following is the penetration tester conducting?
A. Port scan
B. Brute force
C. Credential stuffing
D. DoS attack
-
Question 49:
A Chief Information Security Officer wants a penetration tester to evaluate the security awareness level of the company's employees.
Which of the following tools can help the tester achieve this goal?
A. Metasploit
B. Hydra
C. SET
D. WPScan
-
Question 50:
A penetration tester has identified several newly released CVEs on a VoIP call manager. The scanning tool the tester used determined the possible presence of the CVEs based off the version number of the service. Which of the following methods would BEST support validation of the possible findings?
A. Manually check the version number of the VoIP service against the CVE release
B. Test with proof-of-concept code from an exploit database
C. Review SIP traffic from an on-path position to look for indicators of compromise D. Utilize an nmap -sV scan against the service
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.