Exam Details
Exam Code
:RC0-501Exam Name
:CompTIA Security+ Recertification ExamCertification
:CompTIA Security+Vendor
:CompTIATotal Questions
:349 Q&AsLast Updated
:Apr 15, 2025
CompTIA CompTIA Security+ RC0-501 Questions & Answers
-
Question 201:
A security analyst accesses corporate web pages and inputs random data in the forms. The response received includes the type of database used and SQL commands that the database accepts. Which of the following should the security analyst use to prevent this vulnerability?
A. Application fuzzing
B. Error handling
C. Input validation
D. Pointer dereference
-
Question 202:
An employee receives an email, which appears to be from the Chief Executive Officer (CEO), asking for a report of security credentials for all users. Which of the following types of attack is MOST likely occurring?
A. Policy violation
B. Social engineering
C. Whaling
D. Spear phishing
-
Question 203:
An information security analyst needs to work with an employee who can answer questions about how data for a specific system is used in the business. The analyst should seek out an employee who has the role of:
A. steward
B. owner
C. privacy officer
D. systems administrator
-
Question 204:
A group of non-profit agencies wants to implement a cloud service to share resources with each other and minimize costs. Which of the following cloud deployment models BEST describes this type of effort?
A. Public
B. Hybrid
C. Community
D. Private
-
Question 205:
A director of IR is reviewing a report regarding several recent breaches. The director complies the following statistics:
Initial IR engagement time frame
Length of time before an executive management notice went out Average IR phase completion
The director wants to use data to shorten the response time. Which of the following would accomplish this?
A. CSIRT
B. Containment phase
C. Escalation notifications
D. Tabletop exercise
-
Question 206:
A copy of a highly confidential salary report was recently found on a printer in the IT department. The human resources department does not have this specific printer mapped to its devices, and it is suspected that an employee in the IT department browsed to the share where the report was located and printed it without authorization. Which of the following technical controls would be the BEST choice to immediately prevent this from happening again?
A. Implement a DLP solution and classify the report as confidential, restricting access only to human resources staff
B. Restrict access to the share where the report resides to only human resources employees and enable auditing
C. Have all members of the IT department review and sign the AUP and disciplinary policies
D. Place the human resources computers on a restricted VLAN and configure the ACL to prevent access from the IT department
-
Question 207:
A security analyst reviews the following output:
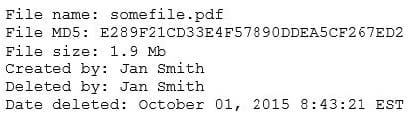
The analyst loads the hash into the SIEM to discover if this hash is seen in other parts of the network. After inspecting a large number of files, the security analyst reports the following:
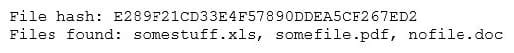
Which of the following is the MOST likely cause of the hash being found in other areas?
A. Jan Smith is an insider threat
B. There are MD5 hash collisions
C. The file is encrypted
D. Shadow copies are present
-
Question 208:
A company's AUP requires:
Passwords must meet complexity requirements.
Passwords are changed at least once every six months.
Passwords must be at least eight characters long.
An auditor is reviewing the following report:
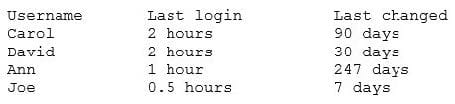
Which of the following controls should the auditor recommend to enforce the AUP?
A. Account lockout thresholds
B. Account recovery
C. Password expiration
D. Prohibit password reuse
-
Question 209:
An organization's primary datacenter is experiencing a two-day outage due to an HVAC malfunction. The node located in the datacenter has lost power and is no longer operational, impacting the ability of all users to connect to the alternate datacenter. Which of the following BIA concepts BEST represents the risk described in this scenario?
A. SPoF
B. RTO
C. MTBF
D. MTTR
-
Question 210:
A security analyst notices anomalous activity coming from several workstations in the organizations. Upon identifying and containing the issue, which of the following should the security analyst do NEXT?
A. Document and lock the workstations in a secure area to establish chain of custody
B. Notify the IT department that the workstations are to be reimaged and the data restored for reuse
C. Notify the IT department that the workstations may be reconnected to the network for the users to continue working
D. Document findings and processes in the after-action and lessons learned report
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your RC0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.