Exam Details
Exam Code
:SC-100Exam Name
:Microsoft Cybersecurity ArchitectCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:251 Q&AsLast Updated
:Mar 23, 2025
Microsoft Microsoft Certifications SC-100 Questions & Answers
-
Question 111:
You are evaluating an Azure environment for compliance.
You need to design an Azure Policy implementation that can be used to evaluate compliance without changing any resources.
Which effect should you use in Azure Policy?
A. Deny
B. Modify
C. Append
D. Disabled
-
Question 112:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
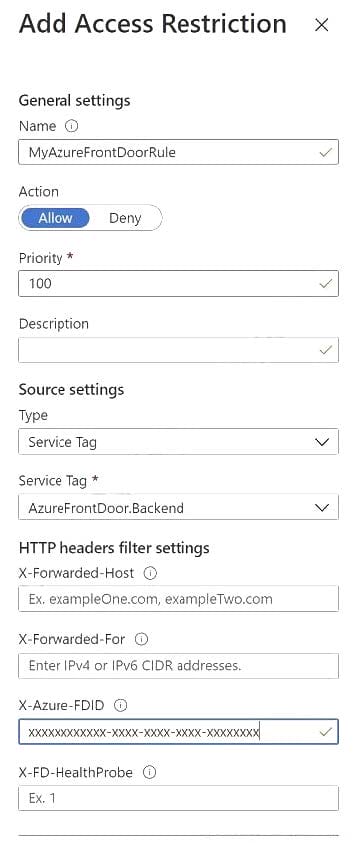
You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance.
You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance.
Solution: You recommend access restrictions to allow traffic from the backend IP address of the Front Door instance.
Does this meet the goal?
A. Yes
B. No
-
Question 113:
Your company has an on-premises network, an Azure subscription, and a Microsoft 365 E5 subscription. The company uses the following devices:
1.
Computers that run either Windows 10 or Windows 11
2.
Tablets and phones that run either Android or iOS
You need to recommend a solution to classify and encrypt sensitive Microsoft Office 365 data regardless of where the data is stored.
What should you include in the recommendation?
A. eDiscovery
B. Microsoft Information Protection
C. Compliance Manager
D. retention policies
-
Question 114:
A customer is deploying Docker images to 10 Azure Kubernetes Service (AKS) resources across four Azure subscriptions.
You are evaluating the security posture of the customer.
You discover that the AKS resources are excluded from the secure score recommendations.
You need to produce accurate recommendations and update the secure score.
Which two actions should you recommend in Microsoft Defender for Cloud? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Enable Defender plans.
B. Configure auto provisioning.
C. Add a workflow automation.
D. Assign regulatory compliance policies.
E. Review the inventory.
-
Question 115:
You are designing the security standards for containerized applications onboarded to Azure.
You are evaluating the use of Microsoft Defender for Containers.
In which two environments can you use Defender for Containers to scan for known vulnerabilities? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Linux containers deployed to Azure Container Instances
B. Windows containers deployed to Azure Kubernetes Service (AKS)
C. Windows containers deployed to Azure Container Registry
D. Linux containers deployed to Azure Container Registry
E. Linux containers deployed to Azure Kubernetes Service (AKS)
-
Question 116:
Your company has a hybrid cloud infrastructure.
The company plans to hire several temporary employees within a brief period. The temporary employees will need to access applications and data on the company' premises network.
The company's security policy prevents the use of personal devices for accessing company data and applications.
You need to recommend a solution to provide the temporary employee with access to company resources. The solution must be able to scale on demand.
What should you include in the recommendation?
A. Deploy Azure Virtual Desktop, Azure AD Conditional Access, and Microsoft Defender for Cloud Apps.
B. Redesign the VPN infrastructure by adopting a split tunnel configuration.
C. Deploy Microsoft Endpoint Manager and Azure AD Conditional Access.
D. Migrate the on-premises applications to cloud-based applications.
-
Question 117:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your on-premises network contains an e-commerce web app that was developed in Angular and Node,js. The web app uses a MongoDB database. You plan to migrate the web app to Azure. The solution architecture team proposes the following architecture as an Azure landing zone.
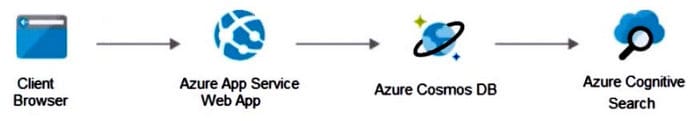
You need to provide recommendations to secure the connection between the web app and the database. The solution must follow the Zero Trust model.
Solution: You recommend creating private endpoints for the web app and the database layer.
Does this meet the goal?
A. Yes
B. No
-
Question 118:
Your company is developing a serverless application in Azure that will have the architecture shown in the following exhibit.
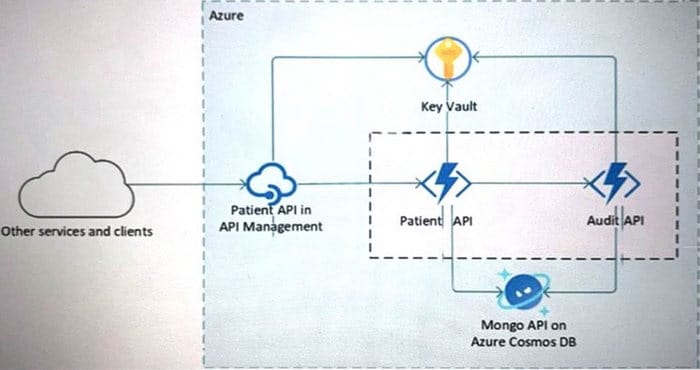
You need to recommend a solution to isolate the compute components on an Azure virtual network. What should you include in the recommendation?
A. Azure Active Directory (Azure AD) enterprise applications
B. an Azure App Service Environment (ASE)
C. Azure service endpoints
D. an Azure Active Directory (Azure AD) application proxy
-
Question 119:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8 points.
You need to recommend configurations to increase the score of the Secure management ports controls.
Solution: You recommend enabling just-in-time (JIT) VM access on all virtual machines.
Does this meet the goal?
A. Yes
B. No
-
Question 120:
A customer uses Azure to develop a mobile app that will be consumed by external users as shown in the following exhibit.
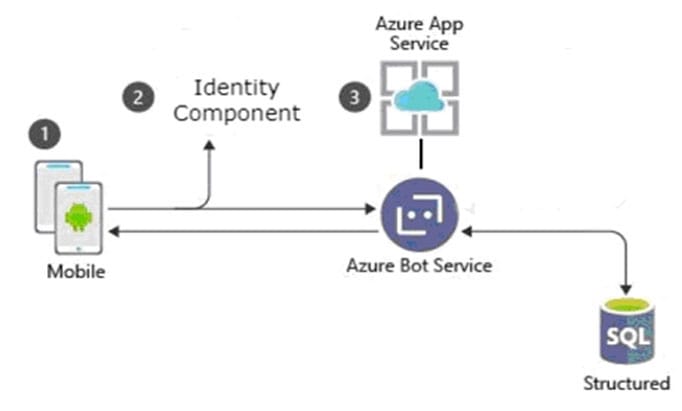
You need to design an identity strategy for the app. The solution must meet the following requirements:
1.
Enable the usage of external IDs such as Google, Facebook, and Microsoft accounts.
2.
Be managed separately from the identity store of the customer.
3.
Support fully customizable branding for each app. Which service should you recommend to complete the design?
A. Azure Active Directory (Azure AD) B2B
B. Azure Active Directory Domain Services (Azure AD DS)
C. Azure Active Directory (Azure AD) B2C
D. Azure AD Connect
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SC-100 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.