Exam Details
Exam Code
:SC-300Exam Name
:Microsoft Identity and Access AdministratorCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:305 Q&AsLast Updated
:Mar 29, 2025
Microsoft Microsoft Certifications SC-300 Questions & Answers
-
Question 31:
Your company purchases 2 new Microsoft 365 ES subscription and an app named App.
You need to create a Microsoft Defender for Cloud Apps access policy for App1.
What should you do you first? (Choose Correct Answer based on Microsoft Identity and Access Administrator at microsoft.com)
A. Configure a Token configuration for App1.
B. Add an API permission for App.
C. Configure a Conditional Access policy to use app-enforced restrictions.
D. Configure a Conditional Access policy to use Conditional Access App Control.
-
Question 32:
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains an Azure AD enterprise application named App1.
A contractor uses the credentials of [email protected].
You need to ensure that you can provide the contractor with access to App1.
The contractor must be able to authenticate as [email protected].
What should you do?
A. Run the New-AzADUser cmdlet.
B. Configure the External collaboration settings.
C. Add a WS-Fed identity provider.
D. Create a guest user account in contoso.com.
-
Question 33:
You have a Microsoft 365 E5 subscription.
You create a user named User1.
You need to ensure that User1 can update the status of Identity Secure Score improvement actions.
Solution: You assign the Exchange Administrator role to User1.
Does this meet the goal?
A. Yes
B. No
-
Question 34:
You have an Azure Active Directory (Azure AD) Azure AD tenant.
You need to bulk create 25 new user accounts by uploading a template file.
Which properties are required in the template file?
A. displayName, identityIssuer, usageLocation, and userType
B. accountEnabled, givenName, surname, and userPrincipalName
C. accountEnabled, displayName, userPrincipalName, and passwordProfile
D. accountEnabled, passwordProfile, usageLocation, and userPrincipalName
-
Question 35:
You have a Microsoft 365 E5 subscription.
You create a user named User1.
You need to ensure that User1 can update the status of Identity Secure Score improvement actions.
Solution: You assign the User Administrator role to User1.
Does this meet the goal?
A. Yes
B. No
-
Question 36:
You have an Azure Active Directory (Azure AD) tenant that uses Azure AD Identity Protection and contains the resources shown in the following table.

Azure Multi-factor Authentication (MFA) is enabled for all users.
User1 triggers a medium severity alert that requires additional investigation.
You need to force User1 to reset his password the next time he signs in. The solution must minimize administrative effort.
What should you do?
A. Reconfigure the user risk, policy to trigger on medium or low severity.
B. Mark User1 as compromised.
C. Reset the Azure MIFA registration for User1.
D. Configure a sign-in risk policy.
-
Question 37:
You have a Microsoft 365 tenant.
All users have mobile phones and laptops.
The users frequently work from remote locations that do not have Wi-Fi access or mobile phone connectivity.
While working from the remote locations, the users connect their laptop to a wired network that has internet access.
You plan to implement multi-factor authentication (MFA).
Which MFA authentication method can the users use from the remote location?
A. a notification through the Microsoft Authenticator app
B. email
C. security questions
D. a verification code from the Microsoft Authenticator app
-
Question 38:
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.
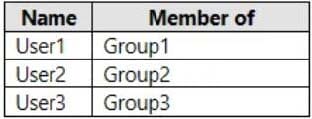
The tenant has the authentication methods shown in the following table.
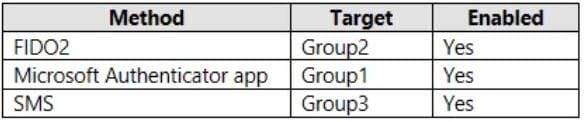
Which users will sign in to cloud apps by matching a number shown in the app with a number shown on their phone?
A. User1 only
B. User2 only
C. User3 only
D. User1 and User2 only
E. User2 and User3 only
-
Question 39:
You have an Azure Active Directory (Azure AD) tenant that contains a user named User1 and the conditional access policies shown in the following table.
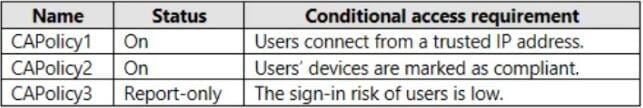
You need to evaluate which policies will be applied to User1 when User1 attempts to sign-in from various IP addresses. Which feature should you use?
A. Access reviews
B. Identity Secure Score
C. The What If tool
D. the Microsoft 365 network connectivity test tool
-
Question 40:
You have a Microsoft 365 tenant.
All users have mobile phones and Windows 10 laptops.
The users frequently work from remote locations that do not have Wi-Fi access or mobile phone connectivity.
While working from the remote locations, the users connect their laptops to a wired network that has internet access.
You plan to implement multi-factor authentication (MFA).
Which MFA authentication method can the users use from the remote location?
A. an app password
B. voice
C. Windows Hello for Business
D. security questions
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SC-300 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.