Exam Details
Exam Code
:SC-400Exam Name
:Microsoft Information Protection AdministratorCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:362 Q&AsLast Updated
:Mar 24, 2025
Microsoft Microsoft Certifications SC-400 Questions & Answers
-
Question 41:
You have a Microsoft OneDrive for Business folder that contains the files shown in the following table.
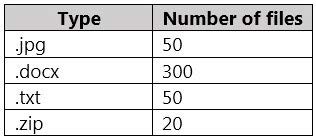
In Microsoft Cloud App Security, you create a file policy to automatically apply a classification. What is the effect of applying the policy?
A. The policy will apply to only the .docx and .txt files. The policy will classify the files within 24 hours.
B. The policy will apply to all the files. The policy will classify only 100 files daily.
C. The policy will apply to only the .docx files. The policy will classify only 100 files daily.
D. The policy will apply to only the .docx and .txt files. The policy will classify the files immediately.
-
Question 42:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant and 500 computers that run Windows 10. The computers are onboarded to the Microsoft 365 compliance center.
You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers.
You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents.
Solution: From the Microsoft 365 Endpoint data loss prevention (Endpoint DLP) settings, you add the application to the unallowed apps list.
Does this meet the goal?
A. Yes
B. No
-
Question 43:
You have a Microsoft 365 tenant that has devices onboarded to Microsoft Defender for Endpoint as shown in the following table.
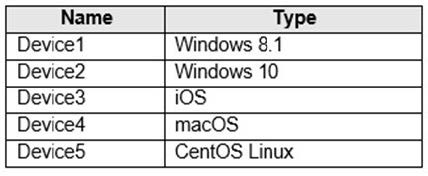
You plan to start using Microsoft 365 Endpoint data loss protection (Endpoint DLP). Which devices support Endpoint DLP?
A. Device5 only
B. Device2 only
C. Device 1, Device2, Device3, Device4, and Device5
D. Device3 and Device4 only
E. Device1 and Device2 only
-
Question 44:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant and 500 computers that run Windows 10. The computers are onboarded to the Microsoft 365 compliance center.
You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers.
You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents.
Solution: From the Cloud App Security portal, you mark the application as Unsanctioned.
Does this meet the goal?
A. Yes
B. No
-
Question 45:
You have a Microsoft 365 subscription that uses Microsoft Exchange Online.
You need to receive an alert if a user emails sensitive documents to specific external domains. What should you create?
A. a data loss prevention (DLP) policy that uses the Privacy category
B. a Microsoft Cloud App Security activity policy
C. a Microsoft Cloud App Security file policy
D. a data loss prevention (DLP) alert filter
-
Question 46:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You recently discovered that the developers at your company emailed Azure Storage keys in plain text to third parties.
You need to ensure that when Azure Storage keys are emailed, the emails are encrypted.
Solution: You configure a mail flow rule that matches the text patterns.
Does this meet the goal?
A. Yes
B. No
-
Question 47:
You create a retention label that has a retention period of seven years.
You need to ensure that documents containing a credit card number are retained for seven years. Other documents must not be retained.
What should you create?
A. a retention label policy of type publish
B. a retention policy that retains file automatically
C. a retention policy that deletes files automatically
D. a retention label policy of type auto-apply
-
Question 48:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant and 500 computers that run Windows 10. The computers are onboarded to the Microsoft 365 compliance center.
You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers.
You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents.
Solution: From the Microsoft 365 Endpoint data loss prevention (Endpoint DLP) settings, you add a folder path to the file path exclusions.
Does this meet the goal?
A. Yes
B. No
-
Question 49:
You are planning a data loss prevention (DLP) solution that will apply to computers that run Windows 10.
You need to ensure that when users attempt to copy a file that contains sensitive information to a USB storage device, the following requirements are met:
1.
If the users are members of a group named Group1, the users must be allowed to copy the file, and an event must be recorded in the audit log.
2.
All other users must be blocked from copying the file. What should you create?
A. two DLP policies that each contains one DLP rule
B. one DLP policy that contains one DLP rule
C. one DLP policy that contains two DLP rules
-
Question 50:
You need to be alerted when users share sensitive documents from Microsoft One Drive to any users outside your company. What should you do?
A. From the Exchange admin center, create a data loss prevention (DLP) policy.
B. From the Azure portal, create an Azure Active Directory (Azure AD) Identity Protection policy.
C. From the Microsoft 365 compliance center, create an insider risk policy.
D. From the Cloud App Security portal, create a file policy.
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SC-400 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.