Exam Details
Exam Code
:SC-900Exam Name
:Microsoft Security Compliance and Identity FundamentalsCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:242 Q&AsLast Updated
:Mar 29, 2025
Microsoft Microsoft Certifications SC-900 Questions & Answers
-
Question 141:
You have a Microsoft 365 E5 tenant that uses a domain named contoso.com.
A user named User1 sends link-based, branded emails that are encrypted by using Microsoft Office 365 Advanced Message Encryption to the recipients shown in the following table.
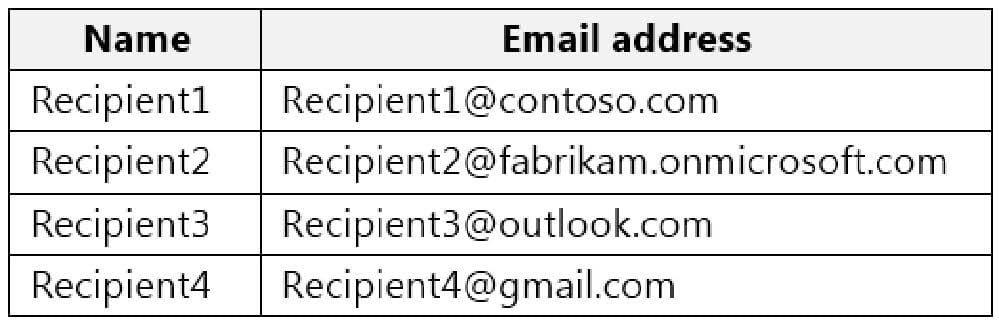
For which recipients can User1 revoke the emails?
A. Recipient4 only
B. Recipient1 only
C. Recipient1, Recipient2, Recipient3, and Recipient4
D. Recipient3 and Recipient4 only
E. Recipient1 and Recipient2 only
-
Question 142:
You receive an email that contains a list of words that will be used for a sensitive information type.
You need to create a file that can be used as the source of a keyword dictionary.
In which format should you save the list?
A. a JSON file that has an element for each word
B. an ACCDB database file that contains a table named Dictionary
C. an XML file that contains a keyword tag for each word
D. a CSV file that contains words separated by commas
-
Question 143:
A user reports that she can no longer access a Microsoft Excel file named Northwind Customer Data.xlsx. From the Cloud App Security portal, you discover the alert shown in the exhibit.
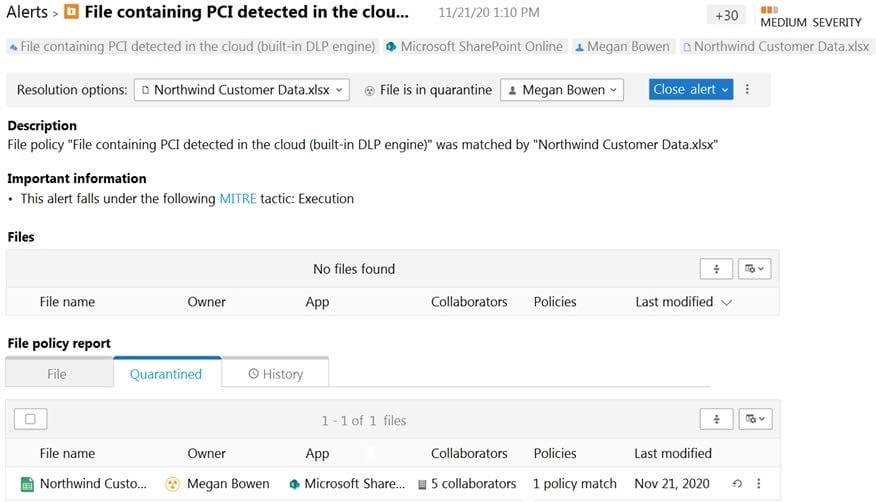
You restore the file from quarantine.
You need to prevent files that match the policy from being quarantined. Files that match the policy must generate an alert.
What should you do?
A. Modify the policy template.
B. Assign the Global reader role to the file owners.
C. Exclude file matching by using a regular expression.
D. Update the governance action.
-
Question 144:
You create a custom sensitive info type that uses Exact Data Match (EDM).
You plan to periodically update and upload the data used for EDM.
What is the maximum frequency with which the data can be uploaded?
A. twice per week
B. twice per day
C. once every six hours
D. once every 48 hours
E. twice per hour
-
Question 145:
Each product group at your company must show a distinct product logo in encrypted emails instead of the standard Microsoft Office 365 logo. What should you do to create the branding templates?
A. Create a Transport rule.
B. Create an RMS template.
C. Run the Set-IRMConfiguration cmdlet.
D. Run the New-OMEConfiguration cmdlet.
-
Question 146:
What can you specify in Microsoft 365 sensitivity labels?
A. how long files must be preserved
B. when to archive an email message
C. which watermark to add to files
D. where to store files
-
Question 147:
You are creating a custom trainable classifier to identify organizational product codes referenced in Microsoft 365 content.
You identify 300 files to use as seed content.
Where should you store the seed content?
A. a Microsoft SharePoint Online folder
B. a Microsoft OneDrive for Business folder
C. an Azure file share
D. Microsoft Exchange Online shared mailbox
-
Question 148:
Which Microsoft portal provides information about how Microsoft manages privacy, compliance, and security?
A. Microsoft Service Trust Portal
B. Compliance Manager
C. Microsoft 365 compliance center
D. Microsoft Support
-
Question 149:
What can you protect by using the information protection solution in the Microsoft 365 compliance center?
A. computers from zero-day exploits
B. users from phishing attempts
C. files from malware and viruses
D. sensitive data from being exposed to unauthorized users
-
Question 150:
Which Microsoft 365 feature can you use to restrict users from sending email messages that contain lists of customers and their associated credit card numbers?
A. retention policies
B. data loss prevention (DLP) policies
C. conditional access policies
D. information barriers
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SC-900 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.