Exam Details
Exam Code
:SK0-005Exam Name
:CompTIA Server+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:457 Q&AsLast Updated
:Mar 24, 2025
CompTIA CompTIA Certifications SK0-005 Questions & Answers
-
Question 41:
A human resources analyst is attempting to email the records for new employees to an outside payroll company. Each time the analyst sends an email containing employee records, the email is rejected with an error message. Other emails outside the company are sent correctly. Which of the following is most likely generating the error?
A. DHCP configuration
B. Firewall rules
C. DLP software
D. Intrusion detection system
-
Question 42:
A data center employee shows a driver's license to enter the facility Once the employee enters, the door immediately doses and locks, triggering a scale that then weighs the employee before granting access to another locked door. This is an example of.
A. mantrap.
B. a bollard
C. geofencing
D. RFID.
-
Question 43:
The HIDS logs on a server indicate a significant number of unauthorized access attempts via USB devices at startup. Which of the following steps should a server administrator take to BEST secure the server without limiting functionality?
A. Set a BIOS/UEFI password on the server.
B. Change the boot order on the server and restrict console access.
C. Configure the host OS to deny login attempts via USB.
D. Disable all the USB ports on the server.
-
Question 44:
A server administrator wants to check the open ports on a server.
Which of the following commands should the administrator use to complete the task?
A. nslookup
B. nbtstat
C. telnet
D. netstat -a
-
Question 45:
A server administrator receives the following output when trying to ping a local host:
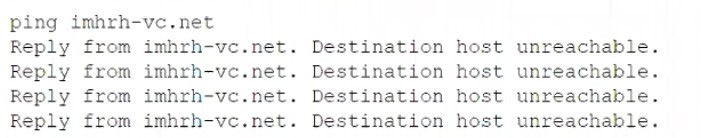
Which of the following is MOST likely the issue?
A. Firewall
B. DHCP
C. DNS
D. VLAN
-
Question 46:
An application needs 10GB of RAID 1 for log files, 20GB of RAID 5 for data files, and 20GB of RAID 5 for the operating system. All disks will be 10GB in capacity. Which of the following is the MINIMUM number of disks needed for this application?
A. 6
B. 7
C. 8
D. 9
-
Question 47:
Which of the following testing exercises for disaster recovery is primarily used to discuss incident response strategies for critical systems without affecting production data?
A. Tabletcp
B. Backup recovery test
C. Lrverail over
D. Hot-site visit audit
-
Question 48:
A new application server has been configured in the cloud to provide access to all clients within the network. On-site users are able to access all resources, but remote users are reporting issues connecting to the new application. The server administrator verifies that all users are configured with the appropriate group memberships. Which of the following is MOST likely causing the issue?
A. Telnet connections are disabled on the server.
B. Role-based access control is misconfigured.
C. There are misconfigured firewall rules.
D. Group policies have not been applied.
-
Question 49:
A technician is troubleshooting a server issue. The technician has determined several possible causes of the issue and has identified various solutions. Which of the following should the technician do NEXT?
A. Consult internet forums to determine which is the most common cause and deploy only that solution.
B. Test each solution individually to determine the root cause, rolling back the changes in between each test.
C. Implement the shortest solution first to identify the issue and minimize downtime.
D. Test each solution in succession and restore the server from the latest snapshot.
-
Question 50:
A data center technician is assigned the daily task of walking through the data center to perform a health check on all the systems. Which of the following issues can the technician detect without logging on to any of the systems? (Choose two.)
A. VLAN mismatch
B. UPS battery fault
C. Overheating
D. Memory exhaustion
E. IP conflict
F. OS failure
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SK0-005 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.