Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Apr 14, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 1211:
A security analyst has received several reports of an issue on an internal web application. Users state they are having to provide their credentials twice to log in. The analyst checks with the application team and notes this is not an expected behavior. After looking at several logs, the analyst decides to run some commands on the gateway and obtains the following output:

Which of the following BEST describes the attack the company is experiencing?
A. MAC flooding
B. URL redirection
C. ARP poisoning
D. DNS hijacking
-
Question 1212:
A security researcher has alerted an organization that its sensitive user data was found for sale on a website. Which of the following should the organization use to inform the affected parties?
A. A An incident response plan
B. A communications plan
C. A business continuity plan
D. A disaster recovery plan
-
Question 1213:
Which of the following uses six initial steps that provide basic control over system security by including hardware and software inventory, vulnerability management, and continuous monitoring to minimize risk in all network environments?
A. ISO 27701
B. The Center for Internet Security
C. SSAE SOC 2
D. NIST Risk Management Framework
-
Question 1214:
A backdoor was detected on the containerized application environment. The investigation detected that a zero-day vulnerability was introduced when the latest container image version was downloaded from a public registry. Which of the following is the BEST solution to prevent this type of incident from occurring again?
A. Enforce the use of a controlled trusted source of container images
B. Deploy an IPS solution capable of detecting signatures of attacks targeting containers
C. Define a vulnerability scan to assess container images before being introduced on the environment
D. Create a dedicated VPC for the containerized environment
-
Question 1215:
The following are the logs of a successful attack.
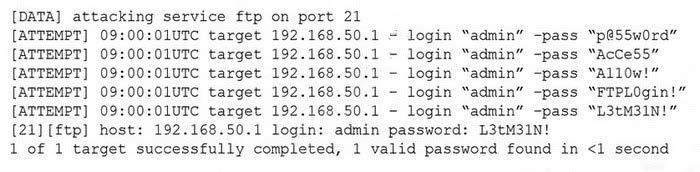
Which of the following controls would be BEST to use to prevent such a breach in the future?
A. Password history
B. Account expiration
C. Password complexity
D. Account lockout
-
Question 1216:
During a Chiet Information Securty Officer (CISO) comvenbon to discuss security awareness, the affendees are provided with a network connection to use as a resource. As the Convention progresses. and of the attendees starts to notice delays in the connection. and the HTTPS ste requests are reverting to HTTP. Which of the folowing BEST describes what is happening?
A. Birtuday colfisices on the cartificate key
B. DNS hijackeng to reroute tratic
C. Brute force 1 tho access point
D. A SSL/TLS downgrade
-
Question 1217:
Which of the following environments would MOST likely be used to assess the execution of component parts of a system at both the hardware and software levels and to measure performance characteristics?
A. Test
B. Staging
C. Development
D. Production
-
Question 1218:
Which of the following are the MOST likely vectors for the unauthorized inclusion of vulnerable code in a software company's final software releases? (Select TWO.)
A. Unsecure protocols
B. Use of penetration-testing utilities
C. Weak passwords
D. Included third-party libraries
E. Vendors/supply chain
F. Outdated anti-malware software
-
Question 1219:
Which of the following cryptographic concepts would a security engineer utilize while implementing non-repudiation? (Select TWO)
A. Block cipher
B. Hashing
C. Private key
D. Perfect forward secrecy
E. Salting
F. Symmetric keys
-
Question 1220:
After a phishing scam for a user's credentials, the red team was able to craft payload to deploy on a server. The attack allowed the installation of malicious software that initiates a new remote session
Which of the following types of attacks has occurred?
A. Privilege escalation
B. Session replay
C. Application programming interface
D. Directory traversal
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.