Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Mar 29, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 1311:
A vendor needs to remotely and securely transfer files from one server to another using the command line. Which of the following protocols should be implemented to allow for this type of access? (Choose two.)
A. SSH
B. SNMP
C. RDP
D. S/MIME
E. SMTP
F. SFTP
-
Question 1312:
A security analyst needs to propose a remediation plan for each item in a risk register. The item with the highest priority requires employees to have separate logins for SaaS solutions and different password complexity requirements for each solution. Which of the following implementation plans will most likely resolve this security issue?
A. Creating a unified password complexity standard
B. Integrating each SaaS solution with the identity provider
C. Securing access to each SaaS by using a single wildcard certificate
D. Configuring geofencing on each SaaS solution
-
Question 1313:
Callers speaking a foreign language are using company phone numbers to make unsolicited phone calls to a partner organization. A security analyst validates through phone system logs that the calls are occurring and the numbers are not being spoofed. Which of the following is the most likely explanation?
A. The executive team is traveling internationally and trying to avoid roaming charges.
B. The company's SIP server security settings are weak.
C. Disgruntled employees are making calls to the partner organization.
D. The service provider has assigned multiple companies the same numbers.
-
Question 1314:
Which of the following best describes a penetration test that resembles an actual external attack?
A. Known environment
B. Partially known environment
C. Bug bounty
D. Unknown environment
-
Question 1315:
A security analyst is reviewing the following system command history on a computer that was recently utilized in a larger attack on the corporate infrastructure:
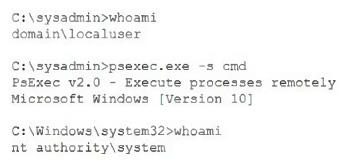
Which of the following best describes what the analyst has discovered?
A. A successful privilege escalation attack by a local user
B. A user determining what level of permissions the user has
C. A systems administrator performing routine maintenance
D. An attempt to utilize living-off-the-land binaries
-
Question 1316:
A security administrator is reviewing reports about suspicious network activity occurring on a subnet. Users on the network report that connectivity to various websites is intermittent. The administrator logs in to a workstation and reviews the following command output:
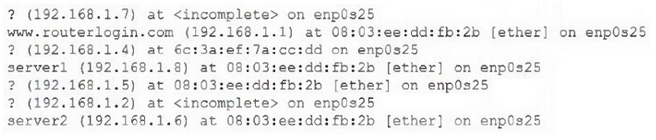
Which of the following best describes what is occurring on the network?
A. ARP poisoning
B. On-path attack
C. URL redirection
D. IP address conflicts
-
Question 1317:
A web application for a bank displays the following output when showing details about a customer's bank account:
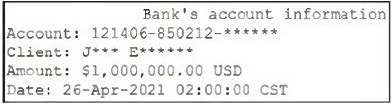
Which of the following techniques is most likely implemented in this web application?
A. Data minimization
B. Data scrambling
C. Data masking
D. Anonymization
-
Question 1318:
The security operations center is researching an event concerning a suspicious IP address. A security analyst looks at the following event logs and discovers that a significant portion of the user accounts have experienced failed log-in attempts when authenticating from the same IP address: Which of the following most likely describes the attack that took place?
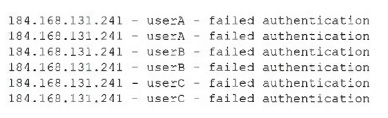
A. Spraying
B. Brute-force
C. Dictionary
D. Rainbow table
-
Question 1319:
A security analyst finds a rogue device during a monthly audit of current endpoint assets that are connected to the network. The corporate network utilizes 802.1 X for access control. To be allowed on the network, a device must have a known hardware address, and a valid username and password must be entered in a captive portal. The following is the audit report:
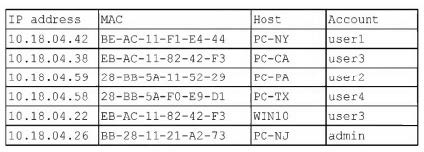
Which of the following is the most likely way a rogue device was allowed to connect?
A. A user performed a MAC cloning attack with a personal device.
B. A DHCP failure caused an incorrect IP address to be distributed.
C. An administrator bypassed the security controls for testing.
D. DNS hijacking let an attacker intercept the captive portal traffic.
-
Question 1320:
A security administrator recently reset local passwords and the following values were recorded in the system:
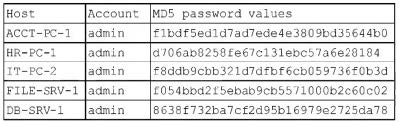
Which of the following is the security administrator most likely protecting against?
A. Account sharing
B. Weak password complexity
C. Pass-the-hash attacks
D. Password compromise
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.