Exam Details
Exam Code
:SY0-701Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:700 Q&AsLast Updated
:Mar 24, 2025
CompTIA CompTIA Certifications SY0-701 Questions & Answers
-
Question 31:
A user would like to install software and features that are not available with a smartphone's default software. Which of the following would allow the user to install unauthorized software and enable new features?
A. SOU
B. Cross-site scripting
C. Jailbreaking
D. Side loading
-
Question 32:
An organization implemented cloud-managed IP cameras to monitor building entry points and sensitive areas. The service provider enables direct TCP/IP connection to stream live video footage from each camera. The organization wants to ensure this stream is encrypted and authenticated. Which of the following protocols should be implemented to best meet this objective?
A. SSH
B. SRTP
C. S/MIME
D. PPTP
-
Question 33:
While investigating a recent security breach an analyst finds that an attacker gained access by SOL infection through a company website. Which of the following should the analyst recommend to the website developers to prevent this from reoccurring?
A. Secure cookies
B. Input sanitization
C. Code signing
D. Blocklist
-
Question 34:
An administrator is reviewing a single server's security logs and discovers the following:
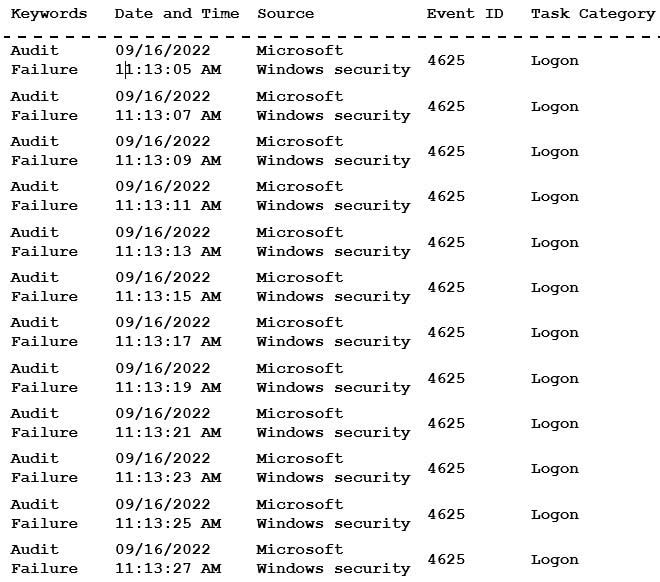
Which of the following best describes the action captured in this log file?
A. Brute-force attack
B. Privilege escalation
C. Failed password audit
D. Forgotten password by the user
-
Question 35:
An organization has too many variations of a single operating system and needs to standardize the arrangement prior to pushing the system image to users. Which of the following should the organization implement first?
A. Standard naming convention
B. Mashing
C. Network diagrams
D. Baseline configuration
-
Question 36:
An organization wants to ensure the integrity of compiled binaries in the production environment. Which of the following security measures would best support this objective?
A. Input validation
B. Code signing
C. SQL injection
D. Static analysis
-
Question 37:
Which of the following best describes configuring devices to log to an off-site location for possible future reference?
A. Log aggregation
B. DLP
C. Archiving
D. SCAP
-
Question 38:
Which of the following threat vectors is most commonly utilized by insider threat actors attempting data exfiltration?
A. Unidentified removable devices
B. Default network device credentials
C. Spear phishing emails
D. Impersonation of business units through typosquatting
-
Question 39:
An IT manager is putting together a documented plan describing how the organization will keep operating in the event of a global incident. Which of the following plans is the IT manager creating?
A. Business continuity
B. Physical security
C. Change management
D. Disaster recovery
-
Question 40:
Which of the following best describe a penetration test that resembles an actual external attack?
A. Known environment
B. Partially known environment
C. Bug bounty
D. Unknown environment
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-701 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.