Exam Details
Exam Code
:VCS-255Exam Name
:Administration of Veritas Storage Foundation 6.1 for UNIXCertification
:VCSVendor
:VeritasTotal Questions
:408 Q&AsLast Updated
:Apr 12, 2025
Veritas VCS VCS-255 Questions & Answers
-
Question 141:
Refer to the exhibit.
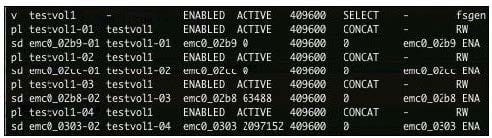
A volume layout is displayed in the exhibit. Which two commands should the administrator use to remove the mirror from disk emc0_02b9? (Select two.)
A. vxassist -g datadg remove mirror testvol1 emc0_02b9
B. vxassist -g datadg remove mirror testvol1 !emc0_02b9
C. vxedit -g datadg -rf rm testvol1-01
D. vxplex -g datadg -o rm dis testvol1-01
E. vxassist -g datadg remove mirror testvol1 testvol1-01
-
Question 142:
Which point-in-time copy solution provided by Veritas Storage Foundation requires an amount of free disk space equal to that of the original volume?
A. Full file system snapshot
B. Full-sized instant snapshot
C. Full buffer-optimized instant snapshot
D. Storage checkpoint
-
Question 143:
Which command removes the datavol volume from the datadg disk group?
A. vxedit -g datadg -rf remove datavol
B. vxvol -g datadg rm datavol
C. vxvol -g datadg remove datavol
D. vxedit -g datadg -rf rm datavol
-
Question 144:
What are the key components of a group policy in Symantec Mail Security 8300?
A. a list of sender groups, sender authentication profiles, and scan settings for an organization
B. disposition configuration, user email addresses, and quarantine settings
C. an LDAP source and a local domain
D. conditions, a set of actions, and groups to whom the policy applies
-
Question 145:
What is only configured during the Site Setup wizard?
A. Local domains
B. Policy configuration
C. Add administrator accounts
D. Appliance role
-
Question 146:
What is an advantage of the Veritas Storage Foundation 6.1 for UNIX checkpoint visibility feature?
A. ensures checkpoint is automatically deleted under certain conditions
B. eliminates the need for manually mounting storage checkpoints
C. specifies verbose mode, which displays extensive statistical information
D. automatically creates new checkpoints as changes are made to the file system
-
Question 147:
Which region stores the information that manages virtual devices when a LUN is brought under Veritas Storage Foundation 6.1 for UNIX control?
A. private region
B. VTOC region
C. virtual region
D. public region
-
Question 148:
After initial setup, what is the default action for suspected spam messages?
A. Qauarantine the suspected spam message to the Email Spam Quarantine
B. Delete the suspected spam message
C. Insert the text [Suspected Spam] into the subject line
D. Bounce the suspected spam message to the sender
-
Question 149:
A Storage Checkpoint is created with the command:
fsckptadm -R create thu_8pm /data1
Which statement about this checkpoint is correct if the file system runs out of space?
A. It can only be removed manually because it is a non-removable checkpoint.
B. It is removed even if it is mounted.
C. This and all subsequent checkpoints are recursively removed.
D. It is removed only if the checkpoint is unused.
-
Question 150:
When creating a new volume with the New Volume Wizard in VEA, which layout options are available to create a layered volume? (Choose two.)
A. Concatenate-mirror
B. Stripe-mirror
C. Mirror-stripe
D. Mirror-concatenate
E. Concatenate-stripe
F. Stripe-concatenate
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Veritas exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your VCS-255 exam preparations and Veritas certification application, do not hesitate to visit our Vcedump.com to find your solutions here.