Exam Details
Exam Code
:101Exam Name
:Application Delivery FundamentalsCertification
:F5 CertificationsVendor
:F5Total Questions
:699 Q&AsLast Updated
:Apr 13, 2025
F5 F5 Certifications 101 Questions & Answers
-
Question 321:
If your customer has a policy requirement that cannot be handled in the Visual Policy Editor, what would you use to supplement the Visual Policy Editor?
A. iApps
B. TMOS
C. iControl
D. iRules
-
Question 322:
What are some changes that must be made on the GTM System so that log messages are sent to centralized System Log servers?
A. The IP address of the server must be added to the wideip.conf file.
B. The IP address of the server must be added to the syslogng.conf file.
C. The IP address of the server and valid user id/password combination must be added to the hosts.allow file.
D. The IP address of the server and valid user id/password combination must be added to the syslog ng.conf file.
-
Question 323:
An LTM has the 3 virtual servers, 2 SNATs, four self IP addresses defined, and the networks shown in the exhibit. Selected options for each object are shown below. Settings not shown are at their defaults. Assume port exhaustion has not been reached.
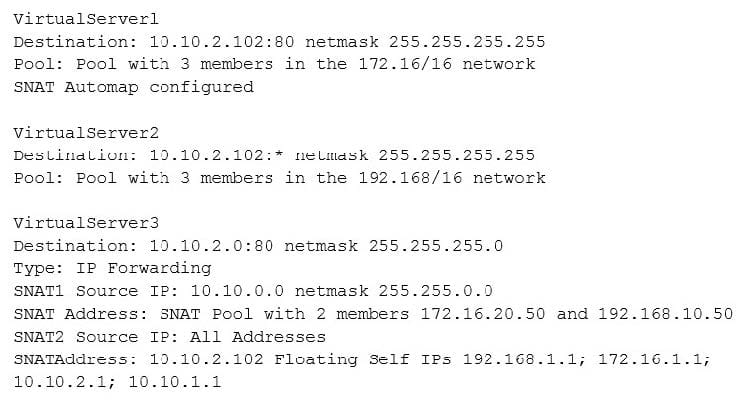
A connection attempt is made with a source IP and port of 10.10.100.50:2222 and a destination
IP and port of 10.10.2.10:80. When the request is processed, what will be the source and destination IP addresses?
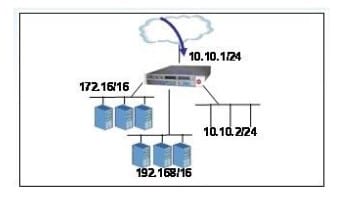
A. The request will be droped.
B. Source IP: 10.10.2.1; Destination IP: 10.10.2.10
C. Source IP: 10.10.2.102; Destination IP 10.10.2.10
D. Source IP: Either 172.16.20.50 or 192.168.10.50; Destination IP: 10.10.2.10
E. Source IP: 10.10.2.1; Destination IP: pool in the 172.16/16 network C
-
Question 324:
Which action will take place when a failover trigger is detected by the active system?
A. The active device will take the action specified for the failure.
B. The standby device also detects the failure and assumes the active role.
C. The active device will wait for all connections to terminate and then failover.
D. The standby device will begin processing virtual servers that have failed, but the active device will continue servicing the functional virtual servers.
-
Question 325:
GTM can load balance to LTM in addition to non-BIG-IP hosts.
A. True
B. False
-
Question 326:
How does the ARX eliminate the disruption caused by re-provisioning storage?
A. By identifying data that has not been modified and moving it to a secondary tier.
B. By reducing the time necessary to run a complete backup.
C. By allowing system administrators to apply policy to specific types data.
D. By automating capacity balancing and allowing seamless introduction of file systems into the environment after the ARX is installed.
-
Question 327:
Which of the following are properties of an ASM logging profile? (Choose three.)
A. storage type
B. storage filter
C. storage policy
D. web application
-
Question 328:
Match each persistence method with the correct statement describing it:
A. Cookie persistence
B. Source address persistence
C. SSL persistence
D. Universal persistence
-
Question 329:
When a business is hacked, they often lose more than money. What are the other consequences to a business as a result of being hacked? Select two.
A. Helpful third party reviews of the security needs of the customer's web applications.
B. Valuable free press that occurs as companies address hacking incidents.
C. Penalties related to non-compliance with laws and regulations.
D. Final resolution of all security vulnerabilities of the business' web applications.
E. Loss of customers when slow connections drive customers to competitor's site.
-
Question 330:
GTM solves which three of these standard DNS limitations? (Choose three.)
A. It can verify that a host is available before resolving a host name for a client.
B. It can use HTTPS for the connection between itself and the client.
C. It can ensure that clients remain at the same data center for stateful applications.
D. It can verify that a client does not have any viruses before sending the IP address.
E. It has more complex load balancing methods.
Related Exams:
101
Application Delivery Fundamentals201
TMOS Administration301A
BIG-IP LTM Specialist: Architect, Set up and Deploy301B
BIG-IP Local Traffic Manager (LTM) Specialist: Maintain & Troubleshoot771-101
Application Delivery FundamentalsF50-506
F5 FirePass 600 V5F50-531
BIG-IP v10.x LTM Essentials V10.xF50-536
BIG-IP ASM v10.x
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only F5 exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 101 exam preparations and F5 certification application, do not hesitate to visit our Vcedump.com to find your solutions here.