Exam Details
Exam Code
:101Exam Name
:Application Delivery FundamentalsCertification
:F5 CertificationsVendor
:F5Total Questions
:699 Q&AsLast Updated
:Apr 13, 2025
F5 F5 Certifications 101 Questions & Answers
-
Question 341:
Administrators can customize APM to resemble other internal Web applications in the organization.
A. True
B. False
-
Question 342:
A virtual server is listening at 10.10.1.100:any and has the following iRule associated with it:

If a user connects to 10.10.1.100 and port 22, which pool will receive the request?
A. ftp pool
B. telnet pool
C. None. The request will be dropped.
D. Unknown. The pool cannot be determined from the information provided.
-
Question 343:
As a full TCP proxy, LTM acts as the termination point for both requests from the client and responses from the server.
A. True
B. False
-
Question 344:
A pool is using Round Trip Time as its load balancing method (Alternate: Round Robin; Fallback:
None). The last five resolutions have been C, D, C, D, C. Given the current conditions shown in the table below, which address will be used for the next resolution?
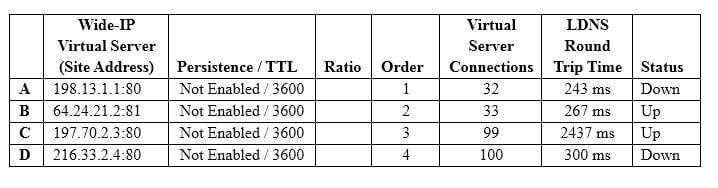
A. A
B. B
C. C
D. D
-
Question 345:
When using a redundant pair of LTMs, it is most advantageous to use them in an Active/Active scenario because this provides additional load balancing capabilities.
A. True
B. False
-
Question 346:
A user is building a security policy using the Deployment Wizard and the Rapid Deployment application template. By default, which settings will be applied to the security policy? (Choose three.)
A. Data Guard will be enabled.
B. The enforcement mode will be set to transparent.
C. The encoding language will be set to auto detect.
D. Wildcard tightening will be enabled on file types and parameters.
E. The Attack signature set applied will be Generic Detection Signatures.
-
Question 347:
Which two methods can be used to determine which BIG-IP is currently active? (Choose two.)
A. The bigtop command displays the status.
B. Only the active system's configuration screens are active.
C. The status (Active/Standby) is embedded in the command prompt.
D. The ifconfig a command displays the floating addresses on the active system.
-
Question 348:
Which of the following are four of the security benefits of TMOS? (Choose four.)
A. It verifies traffic based on antivirus signatures.
B. It provides protection against DDoS.
C. It uses SYN cookies and dynamic connection reapers.
D. It supplies guidance for poorly developed applications.
E. It denies all traffic that hasn't been defined.
F. It can hide confidential information from outbound traffic.
-
Question 349:
When initially configuring the BIG-IP system using the config utility, which two parameters can be set. (Choose two.)
A. the netmask of the SCCP
B. the IP address of the SCCP
C. the port lockdown settings for the SCCP
D. the netmask of the host via the management port
E. the IP address of the host via the management port
F. the port lockdown settings for the host via the management port
-
Question 350:
Which aspect of F5's Intelligent Services Platform helps you extend your security conversation to include F5professionals and customers?
A. Modular Functionality
B. iApps
C. TMOS
D. DevCentral
Related Exams:
101
Application Delivery Fundamentals201
TMOS Administration301A
BIG-IP LTM Specialist: Architect, Set up and Deploy301B
BIG-IP Local Traffic Manager (LTM) Specialist: Maintain & Troubleshoot771-101
Application Delivery FundamentalsF50-506
F5 FirePass 600 V5F50-531
BIG-IP v10.x LTM Essentials V10.xF50-536
BIG-IP ASM v10.x
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only F5 exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 101 exam preparations and F5 certification application, do not hesitate to visit our Vcedump.com to find your solutions here.