Exam Details
Exam Code
:101Exam Name
:Application Delivery FundamentalsCertification
:F5 CertificationsVendor
:F5Total Questions
:699 Q&AsLast Updated
:Apr 13, 2025
F5 F5 Certifications 101 Questions & Answers
-
Question 361:
If the BIG-IP device is NOT always located between the client and the server, it will NOT provide full optimization and security.
A. True
B. False
-
Question 362:
Which item is NOT a function of ASM?
A. Provides authentication and authorization services
B. Logs and reports full HTTP messages
C. Provides comprehensive Web application security
D. Provides application level performance information
-
Question 363:
Assume a client's traffic is being processed only by a NAT; no SNAT or virtual server processing takes place. Also assume that the NAT definition specifies a NAT address and an origin address while all other settings are left at their defaults. If the origin server were to initiate traffic via the BIG-IP, what changes, if any, would take place when the BIG-IP processes such packets?
A. The BIG-IP would drop the request since the traffic didn't arrive destined to the NAT address.
B. The source address would not change, but the destination address would be changed to the NAT address.
C. The source address would be changed to the NAT address and destination address would be left unchanged.
D. The source address would not change, but the destination address would be changed to a self-IP of the BIG-IP.
-
Question 364:
Given the configuration shown below, if a connection request arrived on the BIG-IP with a source address of 200.10.10.10:1050 and a destination of 150.10.10.75:80, what would the source IP address of the associated packet be when it
arrived on the choosen member of the web_pool
self 150.10.10.1 { netmask 255.255.255.0 unit I floating enable vlan external allow tcp https }
self 10.10.1.1 { netmask 255.255.255.0 unit I floating enable vlan internal allow default }
pool web_pool { member 10.10.1.11:80 member 10.10.1.12:80 member 10.10.1.13:80 }
snatpool client_pool { member 10.10.1.100 member 150.10.10.15 }
virtual VS_web { destination 150.10.10.10:80 ip protocol tcp snat automap pool web_pool }
virtual VS_network{ destination 150.10.1 0.0:any mask 255.255.255.0 snatpool client_pool ip protocol tcp pool web_pool }
virtual VS_network { destination 150.10.1 0.0:any mask 255.255.255.0 snatpool client_pool ip protocol tcp pool web_pool }
virtual VS_network { destination 150.10.10.0:any mask 255.255.255.0 snatpool client_pool ip protocol tcp pool web_pool }
A. 10.10.1.IA.10.10.1.1
B. 200.10.10.I0D.200.10.10.10
C. 10.10.1.I00B.10.10.1.100
D. 150.10.10.15C.150.10.10.15
-
Question 365:
If LTM uses the round robin load balancing method, which pool member in the diagram above will receive the next request?
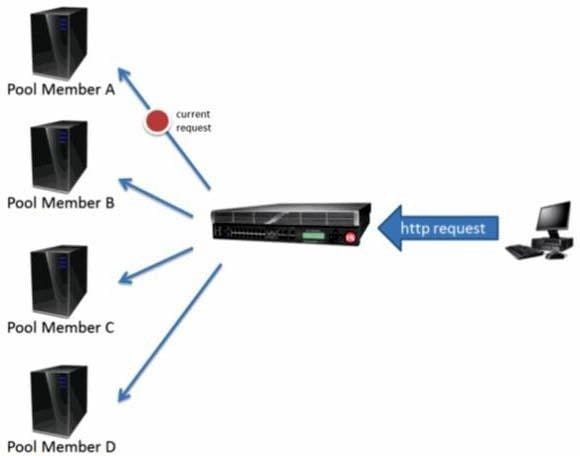
A. A
B. C
C. D
D. B
-
Question 366:
Under what condition must an appliance license be reactivated?
A. Licenses only have to be reactivated for RMAs no other situations.
B. Licenses generally have to be reactivated during system software upgrades.
C. Licenses only have to be reactivated when new features are added (IPv6, Routing Modules, etc.) no other situations.
D. Never. Licenses are permanent for the platform regardless the version of software installed.
-
Question 367:
Which dynamic load balancing mode affects load balancing decisions based on path metrics?
A. Packet Rate
B. Completion Rate
C. Least Connections
D. Virtual Server Capacity
-
Question 368:
Monitors can be assigned to which three resources? (Choose three.)
A. Pools
B. Servers
C. Wide-IPs
D. Data Centers
E. Pool Members
-
Question 369:
Which of the following is a client-side action in the Visual Policy Editor that prevents external access and deletes any files created during a secure access session?
A. Windows Group Policy
B. Resource Assign
C. Protected Workspace
D. Virtual Keyboard
E. Browser Cache and Session Control
-
Question 370:
The main drawback to using an APM Deployment Wizard is that it is not possible to edit the resulting objects, including the access policy.
A. True
B. False
Related Exams:
101
Application Delivery Fundamentals201
TMOS Administration301A
BIG-IP LTM Specialist: Architect, Set up and Deploy301B
BIG-IP Local Traffic Manager (LTM) Specialist: Maintain & Troubleshoot771-101
Application Delivery FundamentalsF50-506
F5 FirePass 600 V5F50-531
BIG-IP v10.x LTM Essentials V10.xF50-536
BIG-IP ASM v10.x
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only F5 exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 101 exam preparations and F5 certification application, do not hesitate to visit our Vcedump.com to find your solutions here.