Exam Details
Exam Code
:156-215.80Exam Name
:Check Point Certified Security Administrator (CCSA)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:535 Q&AsLast Updated
:Mar 03, 2025
CheckPoint Checkpoint Certifications 156-215.80 Questions & Answers
-
Question 451:
You are the Check Point administrator for Alpha Corp with an R80 Check Point estate. You have received a call by one of the management users stating that they are unable to browse the Internet with their new tablet connected to the company Wireless. The Wireless system goes through the Check Point Gateway. How do you review the logs to see what the problem may be?
A. Open SmartLog and connect remotely to the IP of the wireless controller
B. Open SmartView Tracker and filter the logs for the IP address of the tablet
C. Open SmartView Tracker and check all the IP logs for the tablet
D. Open SmartLog and query for the IP address of the Manager's tablet
-
Question 452:
Consider the Global Properties following settings: The selected option "Accept Domain Name over UDP (Queries)" means:
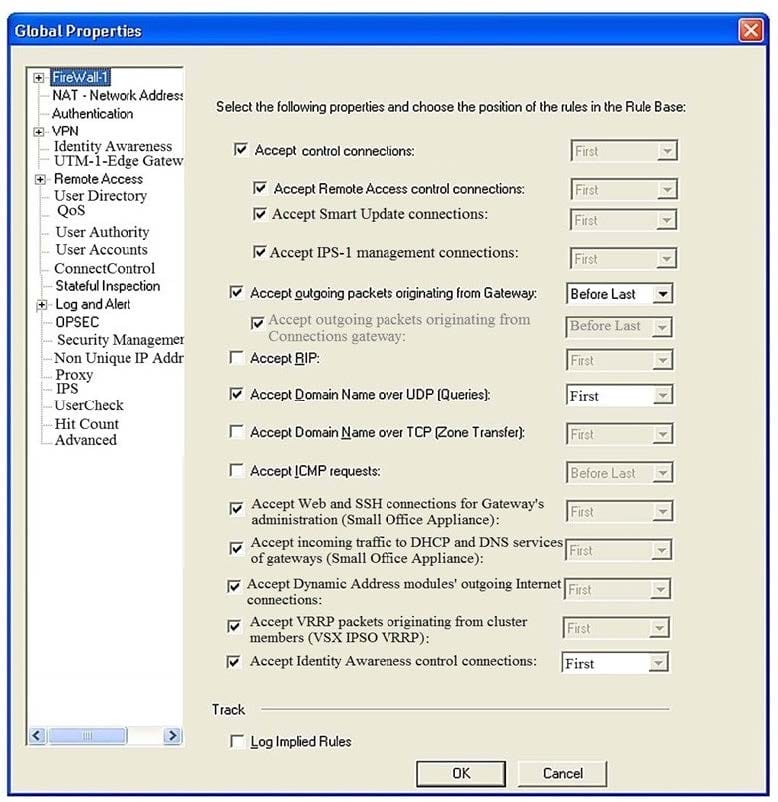
A. UDP Queries will be accepted by the traffic allowed only through interfaces with external anti-spoofing topology and this will be done before first explicit rule written by Administrator in a Security Policy.
B. All UDP Queries will be accepted by the traffic allowed through all interfaces and this will be done before first explicit rule written by Administrator in a Security Policy.
C. No UDP Queries will be accepted by the traffic allowed through all interfaces and this will be done before first explicit rule written by Administrator in a Security Policy.
D. All UDP Queries will be accepted by the traffic allowed by first explicit rule written by Administrator in a Security Policy.
-
Question 453:
How is communication between different Check Point components secured in R80? As with all questions, select the best answer.
A. By using IPSEC
B. By using SIC
C. By using ICA
D. By using 3DES
-
Question 454:
Identify the ports to which the Client Authentication daemon listens on by default?
A. 259, 900
B. 256, 257
C. 8080, 529
D. 80, 256
-
Question 455:
What is the purpose of the CPCA process?
A. Monitoring the status of processes
B. Sending and receiving logs
C. Communication between GUI clients and the SmartCenter server
D. Generating and modifying certificates
-
Question 456:
Which Check Point software blade monitors Check Point devices and provides a picture of network and security performance?
A. Application Control
B. Threat Emulation
C. Logging and Status
D. Monitoring
-
Question 457:
Your internal networks 10.1.1.0/24, 10.2.2.0/24 and 192.168.0.0/16 are behind the Internet Security Gateway. Considering that Layer 2 and Layer 3 setup is correct, what are the steps you will need to do in SmartConsole in order to get the connection working?
A. 1. Define an accept rule in Security Policy.
2.
Define Security Gateway to hide all internal networks behind the gateway's external IP.
3.
Publish and install the policy.
B. 1. Define an accept rule in Security Policy.
2.
Define automatic NAT for each network to NAT the networks behind a public IP.
3.
Publish the policy.
C. 1. Define an accept rule in Security Policy.
2.
Define automatic NAT for each network to NAT the networks behind a public IP.
3.
Publish and install the policy.
D. 1. Define an accept rule in Security Policy.
2.
Define Security Gateway to hide all internal networks behind the gateway's external IP.
3.
Publish the policy.
-
Question 458:
True or False: The destination server for Security Gateway logs depends on a Security Management Server configuration.
A. False, log servers are configured on the Log Server General Properties
B. True, all Security Gateways will only forward logs with a SmartCenter Server configuration
C. True, all Security Gateways forward logs automatically to the Security Management Server
D. False, log servers are enabled on the Security Gateway General Properties
-
Question 459:
What are the three types of UserCheck messages?
A. inform, ask, and block
B. block, action, and warn
C. action, inform, and ask
D. ask, block, and notify
-
Question 460:
What two ordered layers make up the Access Control Policy Layer?
A. URL Filtering and Network
B. Network and Threat Prevention
C. Application Control and URL Filtering
D. Network and Application Control
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215.71
Check Point Certified Security Administrator R71156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)156-315.80
Check Point Certified Security Expert - R80 (CCSE)156-315.81
Check Point Certified Security Expert - R81 (CCSE)156-315.81.20
Check Point Certified Security Expert - R81.20156-560
Check Point Certified Cloud Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.80 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.