Exam Details
Exam Code
:1Z0-821Exam Name
:Oracle Solaris 11 System AdministrationCertification
:Oracle CertificationsVendor
:OracleTotal Questions
:243 Q&AsLast Updated
:Apr 03, 2025
Oracle Oracle Certifications 1Z0-821 Questions & Answers
-
Question 151:
Which network protocol is responsible for routing packets from one network to another?
A. TCP
B. UDP
C. IP
D. ICMP
E. Ethernet
-
Question 152:
How should you permanently restrict the non-global zone testzone so that it does not use more than 20 CPU shares while it is running?
A. While configuring the zone, add this entry:add rct1set name = capped.cpu-sharesadd value (priv = privileged, limit = 20, action = none)endexit
B. While configuring the zone, add this entry: add rct1set name= zone.cpu-sharesadd value (priv=privileged, limit=20, action=none)endexitfrom command line, enter: # dispadmin - d FSS
C. From the command line enter: #prct1 -n zone.cpu-shares - r - v 20 - i zone testzone
D. From the command line, enter:#prct1 - n zone.cpu-shares - v 80 - r - i zone global
-
Question 153:
In a fresh installation of Oracle Solaris 11, default datalinks are named with a genetic naming convention, and they increment as you add interfaces. What is the default name?
A. eth#
B. net#
C. el000g#
D. lo#
E. nic#
-
Question 154:
Which option displays the result of running the zfs list command?
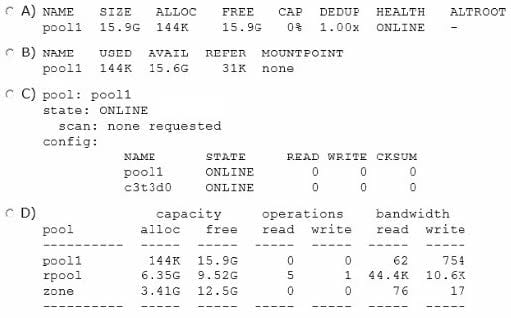
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 155:
Which network protocol provides connectionless, packet-oriented communication between applications?
A. TCP
B. UDP
C. IP
D. ICMP
E. NFS
F. IPSec
-
Question 156:
User1 is attempting to run the following command:
cp bigfile verybig
The system displays the following errer:
cp: cannot create verybig: Disc quota exceeded
Your initial troubleshooting shows that the df -h command indicates the account is at 100% capacity. What command would you use to determine how much disk space the user has available?
A. zfs get quota rpool/export/home/user1
B. zfs userused@user1
C. zfs quota=1M /rpool/export/home/user1
D. df -h | grep user1
-
Question 157:
You are using AI to install a new system. You have added to following information to the AI manifest:
source = "http://sysA.example.com/zone_cfg/zone.cfg"/>
Which statement is true with regard to the zone.cfg?
A. The zone.cfg file is text file in a zonecfg export format.
B. The zone.cfg file is an AI manifest that specifies how the zone is to be installed.
C. The zone.cfg file is an xml file in a form suitable for use as a command file for the zonecfg command.
D. The zone.cfg file is an SC profile with keywords that are specific for configuring a as part of the installation process.
E. It is am xml configuration file from the /etc/zone directory. It will be used as a profile for the zone. It specifies the zonename, zonepath, and other zonecfg parameters.
-
Question 158:
When issuing the zonestat 2 1h is command, the following information is displayed:
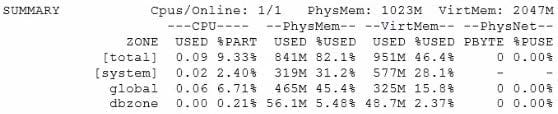
Which two options accurately describe the statistics contained in the output?
A. dbzone is using 0.21% of the total CPU resource available in the zone's processor set.
B. dbzone is using 0.21% of the global zone's total CPU.
C. dbzone is using 5.48% of the total physical memory that has been allocated to the zone.
D. dbzone is using 2.37% of the global zone's total virtual memory.
E. The network is being utilized 100% with no physical bandwidth remaining.
-
Question 159:
Identify the correct description of an IPS image.
A. An ISO image of the Solaris media DVD
B. An IPS repository
C. A depot location or source where Solaris packages can be installed from
D. A location where packages can be installed, for example, your Solaris instance
-
Question 160:
You are asked to determine user jack's default login directory. Which command would provide you with useful information?
A. cat /etc/passwd | grep jack
B. cat /etc/group | grep jack
C. cat /etc/shadow | grep jack
D. cat /etc/default/passwd | grep jack
Related Exams:
1Z0-020
Oracle8i: New Features for Administrators1Z0-023
Architecture and Administration1Z0-024
Performance Tuning1Z0-025
Backup and Recovery1Z0-026
Network Administration1Z0-034
Upgrade Oracle9i/10g OCA to Oracle Database OCP1Z0-036
Managing Oracle9i on Linux1Z0-041
Oracle Database 10g: DBA Assessment1Z0-052
Oracle Database 11g: Administration Workshop I1Z0-053
Oracle Database 11g: Administration II
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Oracle exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 1Z0-821 exam preparations and Oracle certification application, do not hesitate to visit our Vcedump.com to find your solutions here.