Exam Details
Exam Code
:200-301Exam Name
:Implementing and Administering Cisco Solutions (CCNA) (Include Newest Simulation Labs)Certification
:CCNAVendor
:CiscoTotal Questions
:1606 Q&AsLast Updated
:Apr 14, 2025
Cisco CCNA 200-301 Questions & Answers
-
Question 1231:
Which set of actions satisfy the requirement for multifactor authentication?
A. The user enters a user name and password, and then re-enters the credentials on a second screen.
B. The user swipes a key fob, then clicks through an email link.
C. The users enters a user name and password, and then clicks a notification in an authentication app on a mobile device.
D. The user enters a PIN into an RSA token, and then enters the displayed RSA key on a login screen.
-
Question 1232:
Which configuration is needed to generate an RSA key for SSH on a router?
A. Configure VTY access.
B. Configure the version of SSH.
C. Assign a DNS domain name.
D. Create a user with a password.
-
Question 1233:
Refer to the exhibit.
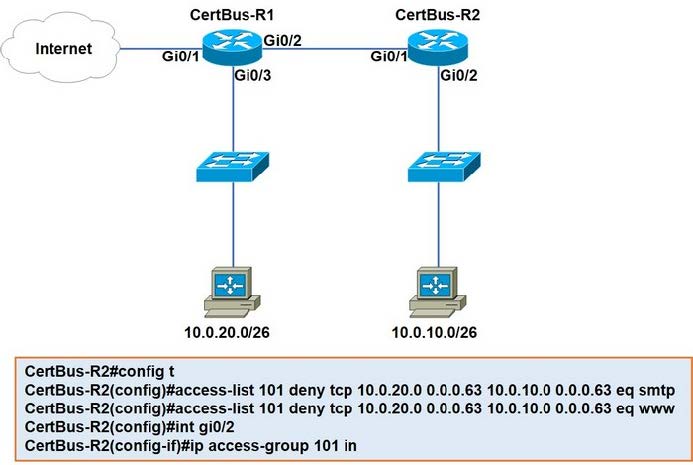
An extended ACL has been configured and applied to router R2. The configuration failed to work as intended.
Which two changes stop outbound traffic on TCP ports 25 and 80 to 10.0.20.0/26 from the 10.0.10.0/26 subnet while still allowing all other traffic? (Choose two.)
A. Add a "permit ip any any" statement at the end of ACL 101 for allowed traffic.
B. Add a "permit ip any any" statement to the beginning of ACL 101 for allowed traffic.
C. The ACL must be moved to the Gi0/1 interface outbound on R2.
D. The source and destination IPs must be swapped in ACL 101.
E. The ACL must be configured the Gi0/2 interface inbound on R1.
-
Question 1234:
An email user has been lured into clicking a link in an email sent by their company's security organization. The webpage that opens reports that it was safe, but the link could have contained malicious code. Which type of security program is in place?
A. user awareness
B. brute force attack
C. physical access control
D. social engineering attack
-
Question 1235:
What is the primary difference between AAA authentication and authorization?
A. Authentication identifies and verifies a user who is attempting to access a system, and authorization controls that tasks the user can perform.
B. Authentication controls the system processes a user can access, and authorization logs the activities the user initiates.
C. Authentication verifies a username and password, and authorization handles the communication between the authentication agent and the user database.
D. Authentication identifies a user who is attempting to access a system, and authorization validates the user's password.
-
Question 1236:
When configuring a WLAN with WPA2 PSK in the Cisco Wireless LAN Controller GUI, which two formats are available to select? (Choose two.)
A. decimal
B. ASCII
C. hexadecimal
D. binary
E. base64
-
Question 1237:
An engineer is asked to protect unused ports that are configured in the default VLAN on a switch. Which two steps will fulfill the request? (Choose two.)
A. Configure the ports as trunk ports.
B. Enable the Cisco Discovery Protocol.
C. Configure the port type as access and place in VLAN 99.
D. Administratively shut down the ports.
E. Configure the ports in an EtherChannel.
-
Question 1238:
Refer to the exhibit.

What is the effect of this configuration?
A. The switch discards all ingress ARP traffic with invalid MAC-to-IP address bindings.
B. All ARP packets are dropped by the switch.
C. Egress traffic is passed only if the destination is a DHCP server.
D. All ingress and egress traffic is dropped because the interface is untrusted.
-
Question 1239:
When a site-to-site VPN is used, which protocol is responsible for the transport of user data?
A. IPsec
B. IKEv1
C. MD5
D. IKEv2
-
Question 1240:
Which type of wireless encryption is used for WPA2 in pre-shared key mode?
A. AES-128
B. TKIP with RC4
C. AES-256
D. RC4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-301 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.