Exam Details
Exam Code
:200-301Exam Name
:Implementing and Administering Cisco Solutions (CCNA) (Include Newest Simulation Labs)Certification
:CCNAVendor
:CiscoTotal Questions
:1606 Q&AsLast Updated
:Apr 14, 2025
Cisco CCNA 200-301 Questions & Answers
-
Question 131:
Which management security process is invoked when a user logs in to a network device using their username and password?
A. authentication
B. auditing
C. accounting
D. authorization
-
Question 132:
Refer to the exhibit.
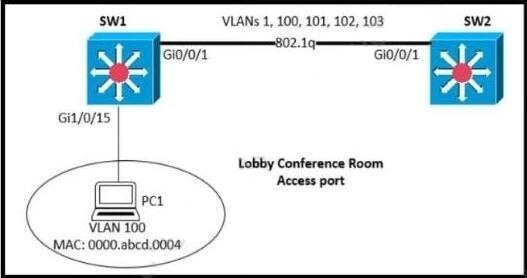
SW1 supports connectivity for a lobby conference room and must be secured. The engineer must limit the connectivity from PC1 to the SW1 and SW2 network. The MAC addresses allowed must be limited to two. Which configuration secures the conference room connectivity?
A. interface gi1/0/15 switchport port-security switchport port-security maximum 2
B. interface gi1/0/15 switchport port-security switchport port-security mac-address 0000.abcd.0004vlan 100
C. interface gi1/0/15 switchport port-security mac-address 0000.abcd.0004 vlan 100
D. interface gi1/0/15 switchport port-security mac-address 0000.abcd.0004 vlan 100 interface switchport secure-mac limit 2
-
Question 133:
Refer to the exhibit.
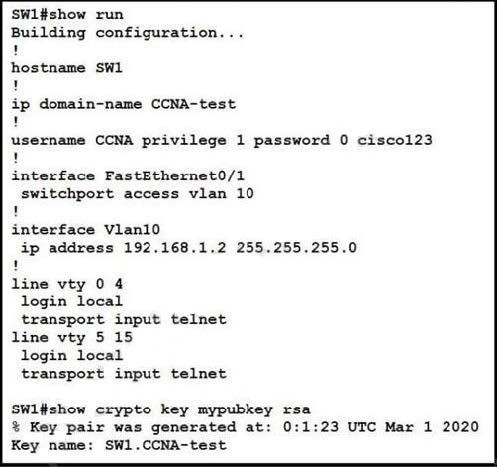
An engineer is updating the management access configuration of switch SW1 to allow secured, encrypted remote configuration. Which two commands or command sequences must the engineer apply to the switch? (Choose two.)
A. SW1(config)#enable secret ccnaTest123
B. SW1(config)#username NEW secret R3mote123
C. SW1(config)#line vty 0 15 SW1(config-line)#transport input ssh
D. SW1(config)# crypto key generate rsa
E. SW1(config)# interface f0/1 SW1(confif-if)# switchport mode trunk
-
Question 134:
Which enhancements were implemented as part of WPA3?
A. Forward secrecy and SAE in personal mode for secure initial key exchange
B. 802.1x authentication and AES-128 encryption
C. AES-64 in personal mode and AES-128 in enterprise mode
D. TKIP encryption improving WEP and per-packet keying
-
Question 135:
In an SDN architecture, which function of a network node is centralized on a controller?
A. Creates the IP routing table
B. Discards a message due filtering
C. Makes a routing decision
D. Provides protocol access for remote access devices
-
Question 136:
Which remote access protocol provides unsecured remote CLI access?
A. console
B. Telnet
C. SSH
D. Bash
-
Question 137:
Which device separates networks by security domains?
A. intrusion protection system
B. firewall
C. wireless controller
D. access point
-
Question 138:
What is a feature of TFTP?
A. offers anonymous user login ability
B. uses two separate connections for control and data traffic
C. relies on the well-known TCP port 20 to transmit data
D. provides secure data transfer
-
Question 139:
Which QoS forwarding per-hop behavior changes a specific value in a packet header to set the class of service for the packet?
A. shaping
B. classification
C. policing
D. marking
-
Question 140:
Which per-hop traffic-control feature does an ISP implement to mitigate the potential negative effects of a customer exceeding its committed bandwidth?
A. policing
B. queuing
C. marking
D. shaping
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-301 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.