Exam Details
Exam Code
:200-301Exam Name
:Implementing and Administering Cisco Solutions (CCNA) (Include Newest Simulation Labs)Certification
:CCNAVendor
:CiscoTotal Questions
:1606 Q&AsLast Updated
:Apr 14, 2025
Cisco CCNA 200-301 Questions & Answers
-
Question 281:
Refer to the exhibit.
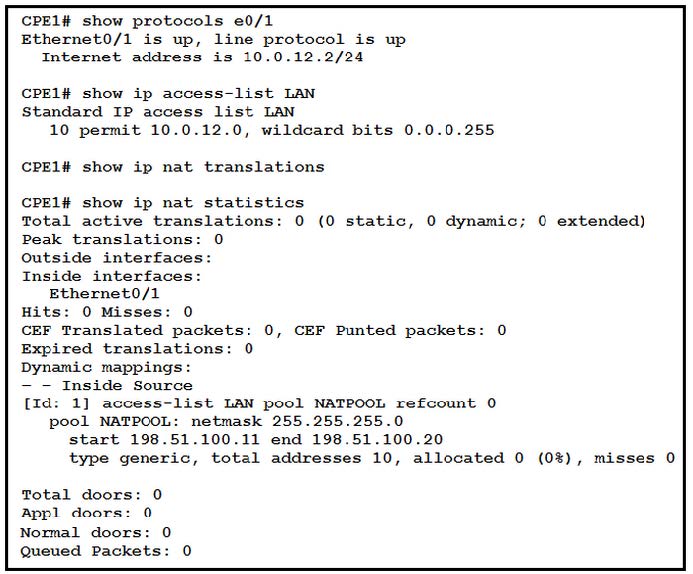
What is the next step to complete the implementation for the partial NAT configuration shown?
A. Reconfigure the static NAT entries that overlap the NAT pool
B. Configure the NAT outside interface
C. Modify the access list for the internal network on e0/1
D. Apply the ACL to the pool configuration
-
Question 282:
Which advantage does the network assurance capability of Cisco DNA Center provide over traditional campus management?
A. Cisco DNA Center correlates information from different management protocols to obtain insights, and traditional campus management requires manual analysis.
B. Cisco DNA Center handles management tasks at the controller to reduce the load on infrastructure devices, and traditional campus management uses the data backbone.
C. Cisco DNA Center leverages YANG and NETCONF to assess the status of fabric and nonfabric devices, and traditional campus management uses CLI exclusively.
D. Cisco DNA Center automatically compares security postures among network devices, and traditional campus management needs manual comparisons.
-
Question 283:
Which security method is used to prevent man-in-the-middle attack?
A. authorization
B. authentication
C. anti-replay
D. accounting
-
Question 284:
Which fact must the engineer consider when implementing syslog on a new network?
A. Syslog defines the software or hardware component that triggered the message.
B. There are 16 different logging levels (0-15).
C. The logging level defines the severity of a particular message.
D. By default, all message levels are sent to the syslog server.
-
Question 285:
Which syslog severity level is considered the most severe and results in the system being considered unusable?
A. Alert
B. Error
C. Emergency
D. Critical
-
Question 286:
Which cable type must be used when connecting a router and switch together using these criteria?
1.
Pins 1 and 2 are receivers and pins 3 and 6 are transmitters.
2.
Auto detection MDI-X is unavailable.
A. crossover
B. rollover
C. console
D. straight-through
-
Question 287:
How does a hub handle a frame traveling to a known destination MAC address differently than a switch?
A. The hub forwards the frame to all ports, and a switch forwards the frame to the known destination.
B. The hub forwards the frame to all ports in the FIB table, and a switch forwards the frame the destination MAC is known.
C. The hub forwards the frame using the information in the MAC table, and a switch uses data in its routing table.
D. The hub forwards the frame only to the port connected to the known MAC address, and a switch forwards the frame to all ports.
-
Question 288:
Which port-security violation mode drops traffic from unknown MAC addresses and forwards an SNMP trap?
A. shutdown VLAN
B. protect
C. restrict
D. shutdown
-
Question 289:
Which cable type must be used when connecting two like devices together using these criteria?
1.
Pins 1 to 3 and 2 to 6 are required.
2.
Auto detection MDI-X is unavailable.
A. straight-through
B. console
C. crossover
D. rollover
-
Question 290:
Which is a fact related to FTP?
A. It uses two separate connections for control and data traffic.
B. It uses block numbers to identify and mitigate data-transfer errors.
C. It always operates without user authentication.
D. It relies on the well-known UDP port 69.
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-301 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.