Exam Details
Exam Code
:200-301Exam Name
:Implementing and Administering Cisco Solutions (CCNA) (Include Newest Simulation Labs)Certification
:CCNAVendor
:CiscoTotal Questions
:1606 Q&AsLast Updated
:Apr 14, 2025
Cisco CCNA 200-301 Questions & Answers
-
Question 461:
What is the role of disaggregation in controller-based networking?
A. It divides the control-plane and data-plane functions.
B. It summarizes the routes between the core and distribution layers of the network topology.
C. It enables a network topology to quickly adjust from a ring network to a star network
D. It streamlines traffic handling by assigning individual devices to perform either Layer 2 or Layer 3 functions.
-
Question 462:
What is a zero-day exploit?
A. It is when a new network vulnerability is discovered before a fix is available
B. It is when the perpetrator inserts itself in a conversation between two parties and captures or alters data.
C. It is when the network is saturated with malicious traffic that overloads resources and bandwidth
D. It is when an attacker inserts malicious code into a SQL server.
-
Question 463:
Refer to the exhibit.
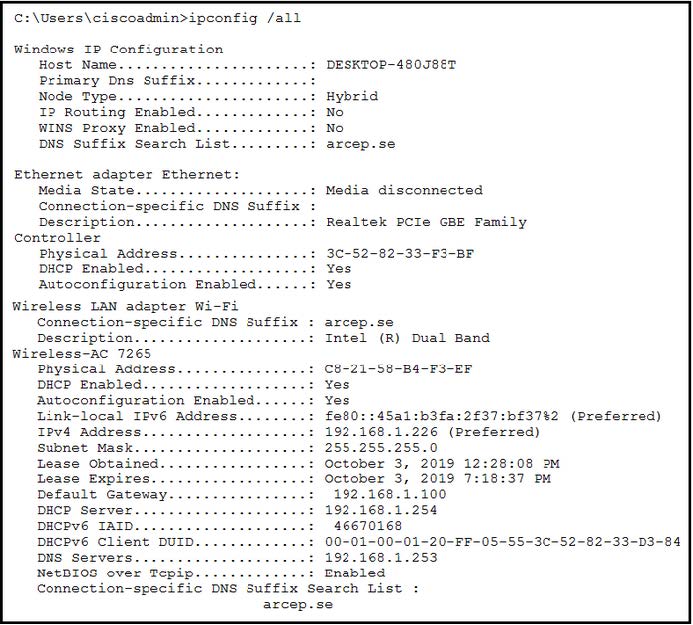
The given Windows PC is requesting the IP address of the host at www.cisco.com. To which IP address is the request sent?
A. 192.168.1.226
B. 192.168.1.100
C. 192.168.1.254
D. 192.168.1.253
-
Question 464:
Refer to the exhibit. All routers in the network are configured. R2 must be the DR. After the engineer connected the devices, R1 was elected as the DR. Which command sequence must be configured on R2 to be elected as the DR in the network?
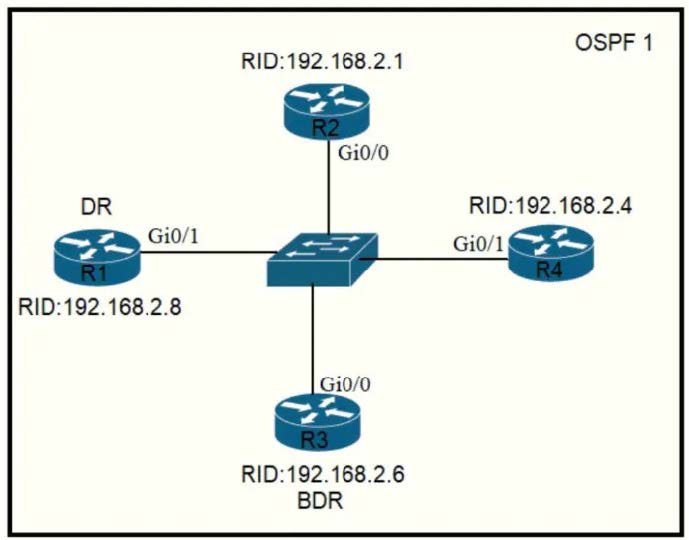
A. R2(config)#router ospf 1 R2(config-router)#router-id 10.100.100.100
B. R2(config)#router ospf 1 R2(config-router)#router-id 192.168.2.7
C. R2(config)#interface gi0/0 R2(config-if)#ip ospf priority 100
D. R2(config)#interface gi0/0 R2(config-if)#ip ospf priority 1
-
Question 465:
A network engineer is replacing the switches that belong to a managed-services client with new Cisco Catalyst switches. The new switches will be configured for updated security standards, including replacing Telnet services with encrypted connections and doubling the modulus size from 1024. Which two commands must the engineer configure on the new switches? (Choose two.)
A. crypto key generate rsa general-keys modulus 1024
B. transport input all
C. crypto key generate rsa usage-keys
D. crypto key generate rsa modulus 2048
E. transport Input ssh
-
Question 466:
Which QoS queuing method discards or marks packets that exceed the desired bit rate of traffic flow?
A. shaping
B. policing
C. CBWFQ
D. LLQ
-
Question 467:
Refer to the exhibit. Router R1 must be configured to reach the 10.0.3.0/24 network from the 10.0.1.0/24 segment. Which command must be used to configure the route?
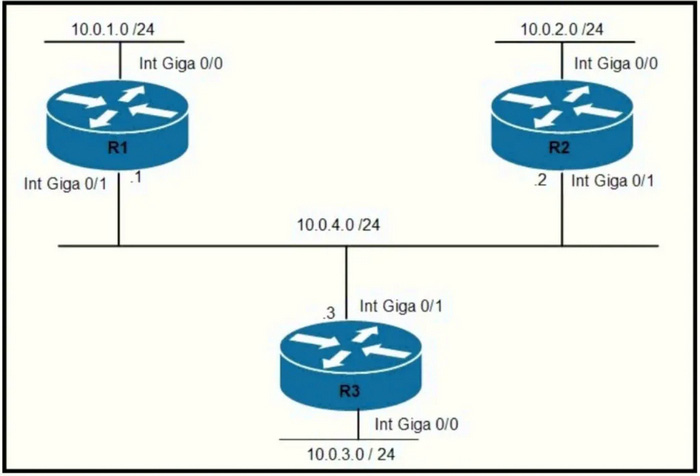
A. route add 10.0.3.0 mask 255.255.255.0 10.0.4.3
B. route add 10.0.3.0 0.255.255.255 10.0.4.2
C. ip route 10.0.3.0 255.255.255.0 10.0.4.3
D. ip route 10.0.3.0 0.255.255.255 10.0.4.2
-
Question 468:
Refer to the exhibit. What is the next hop for traffic entering R1 with a destination of 10.1.2.126?
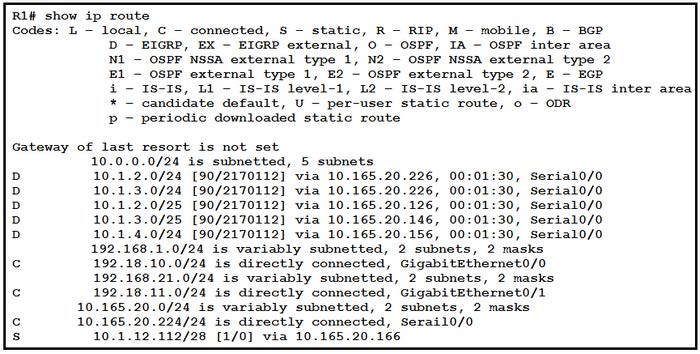
A. 10.165 20.126
B. 10.165.20.146
C. 10.165.20.166
D. 10.165 20.226
-
Question 469:
After a recent security breach and a RADIUS failure, an engineer must secure the console port of each enterprise router with a local username and password. Which configuration must the engineer apply to accomplish this task?
A. aaa new-model line con 0 password plaintextpassword privilege level 15
B. username localuser secret plaintextpassword line con 0 login authentication default privilege level 15
C. username localuser secret plaintextpassword line con 0 no login local privilege level 15
D. aaa new-model aaa authorization exec default local aaa authentication login default radius username localuser privilege 15 secret plaintextpassword
-
Question 470:
An engineer is configuring SSH version 2 exclusively on the R1 router. What is the minimum configuration required to permit remote management using the cryptographic protocol?
A. hostname R1 ip domain name cisco crypto key generate rsa general-keys modulus 1024 username cisco privilege 15 password 0 cisco123 ip ssh version 2 line vty 0 15 transport input ssh login local
B. hostname R1 crypto key generate rsa general-keys modulus 1024 username cisco privilege 15 password 0 cisco123 ip ssh version 2 line vty 0 15 transport input all login local
C. hostname R1 service password-encryption crypto key generate rsa general-keys modulus 1024 username cisco privilege 15 password O cisco123 ip ssh version 2 line vty 0 15 transport input ssh login local
D. hostname R1 ip domain name cisco crypto key generate rsa general-keys modulus 1024 username cisco privilege 15 password 0 cisco123 ip ssh version 2 line vty 0 15 transport input all login local
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-301 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.