Exam Details
Exam Code
:220-1002Exam Name
:CompTIA A+ Certification: Core 2Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:898 Q&AsLast Updated
:Apr 16, 2025
CompTIA CompTIA Certifications 220-1002 Questions & Answers
-
Question 321:
A company has several hard drives that contain old and irrelevant information. The company would like to wipe and repurpose the hard drives for another system.
Which of the following would be the BEST option to meet the requirement and ensure no residual data remains on the repurposed hard drives?
A. Wipe the drives.
B. Format the drives.
C. Degauss the drives.
D. Delete the drive partitions.
-
Question 322:
A technician is running Windows on a company's Mac workstations without incurring an additional expense to the company. The Windows licenses were purchased in the post. Users are required to run both Windows and Mac operating system on their machines, but never at the same time.
Which of the following would be the BEST way to accomplish this?
A. Perform a PXE boot on the workstations.
B. Install virtualization software.
C. Utilize Mission Control on the Mac workstations.
D. Install Boot Camp on the workstations
-
Question 323:
An end user submits a request for the IT specialist to install new software on a workstation The workstation has the following specifications.
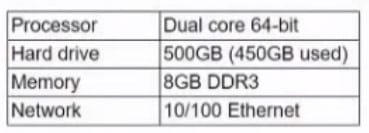
The minimum software requirements for the new application are a dual-core. 64-btt OS with 4GB of RAM and 60GB storage
Which of the following conditions will the technician encounter when attempting to install the software?
A. Insufficient RAM
B. Incompatible processor
C. Insufficient storage
D. Incompatible system architecture
E. Insufficient network bandwidth
-
Question 324:
A user can access the company's internal website properly, but some e-commerce websites have stopped loading and been replaced with an error message. The technician who is troubleshooting the issue tries to update the malware scanner over the network, but the automatic update fails. However, a manual update is successful from a USB drive. No viruses are detected on the device after a full system scan.
Which of the following is the MOST likely cause of the issue?
A. Incorrect time
B. Browser redirection
C. Hijacked email
D. Rogue antivirus
-
Question 325:
A user on a local desktop wants to allow a blocked program through the Windows Firewall.
Which of the following user accounts is necessary to perform this task?
A. Guest
B. Power user
C. Administrator
D. Standard
-
Question 326:
A technician is decommissioning a workstation that contains Pll The HDDs cannot be used in another device, and all data must be destroyed
Which of the following actions would BEST fulfill these requirements? (Select TWO)
A. Physically damage the drives.
B. Leave the drives in the workstation since it will be decommissioned
C. Take a picture of the drives individually and their serial numbers
D. Send the drives to a certified third-party vendor for destruction.
E. Perform a low-level format before removal
F. Set a complex hard drive password.
-
Question 327:
A user is having trouble accessing websites on a computer. A technician troubleshoots and tries to access a site the user typically visits but is instead presented with a completely different site. Which of the following should the technician do NEXT?
A. Clear the DNS cache and check the hosts file.
B. Verify the default gateway settings are correct.
C. Ensure the outbound firewall rules are accurate.
D. Configure the workstation for IPV6.
-
Question 328:
To connect to a secure wireless network, a guest user logs in and is prompted to enter a code that is sent as a text message to the user.
Which of the following types of authentication is this an example?
A. Multifactor
B. RADIUS
C. TACACS
D. Kerberos
-
Question 329:
A customer is missing files from the Desktop and Documents folders after logging on to a PC. A technician looks in the Recycle Bin for the items, but nothing is there. Which of the following steps should the technician take NEXT?
A. Disable application startup.
B. Rebuild the user profile.
C. Reinstall the operating system.
D. Disable Update Services.
-
Question 330:
A user reports unwanted pop-ups are appearing on a computer's screen, and the system is performing slowly. Which of the following should a technician do FIRST to troubleshoot the threat? (Choose two.)
A. Kill all processes that are not related to Windows.
B. Restart the computer in safe mode.
C. Run antivirus and anti-malware scans.
D. Search for software related to the pop-ups.
E. Uninstall the network driver from the Device Manager.
F. Disable all non-Microsoft services.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 220-1002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.