Exam Details
Exam Code
:250-513Exam Name
:Administration of Symantec Data Loss Prevention 12Certification
:Symantec CertificationsVendor
:SymantecTotal Questions
:305 Q&AsLast Updated
:Apr 12, 2025
Symantec Symantec Certifications 250-513 Questions & Answers
-
Question 221:
How should an administrator apply a policy to Network Discover scans?
A. assign the policy group to the scan target
B. choose the correct policy in the scan target
C. assign the policy to the Network Discover Server
D. choose the correct scan target in the policy destination
-
Question 222:
A DLP administrator needs to modify a Network Discover scan that has started.
How should the administrator ignore files larger than 20 MB for the remaining shares?
A. pause the scan, edit the scan target filters to ignore files greater than 20 MB, resume the scan
B. modify the server settings for the Discover server running the scan, adjust the maxfilesize.level setting to greater than 20 MB, restart the Discover server
C. stop the Vontu Monitor Controller Service, go to Manage > Discover Scanning > Discover Targets, set a new filter, restart the service
D. create a new scan with updated file size filters and start the scan
-
Question 223:
Refer to the exhibit.
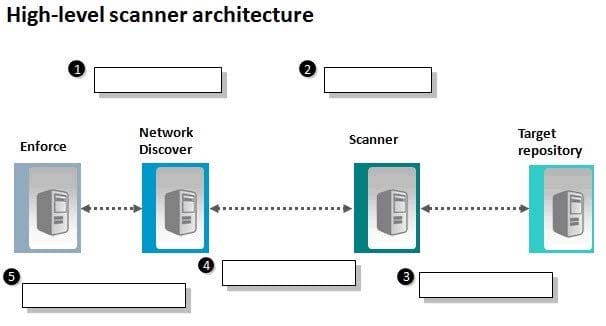
An administrator needs to implement the use of a scanner, but is unfamiliar with the general, high-level process associated with scanners. Which action occurs in step 3?
A. the scanner reviews and confirms configuration parameters
B. the scanner connects to target and reads the content and metadata
C. the scanner process is started by a user or scheduled event
D. the scanner packages filtered content and posts the data to Discover server
-
Question 224:
When working on Storage Foundation 5.0 on HP-UX, you are unable to log in to Veritas Enterprise Administrator. You have converted shadow passwords with long passwords. After converting to shadow password with long password, the users are unable to log into Veritas Enterprise Administrator. You check and ensure that the users are part of the vrtsadm group. Error" V-39-53247-3 Error while connecting to Server. The user name or password is incorrect. Please retype your user name and password, and try connecting to the server again." You want to ensure all users who are part of the vrtsadm group are able to log on to the Veritas Enterprise Administrator.
What should you do?
A. Change the Shadow password.
B. Apply appropriate patch to Veritas Enterprise Administrator.
C. Retype the username and password.
D. Restart the Volume Manager.
-
Question 225:
Which valid automated response option should an administrator choose for Email Prevent?
A. modify the message subject or add specific RFC-2822 headers
B. add metadata to email headers of confidential email
C. modify the body of email messages containing confidential data
D. process confidential email re-routed to a specified email list
-
Question 226:
The VxVM operation fails while importing a disk group and you get an error message "VxVM vxdg ERROR V-5-1-2907 diskgroup: Disk group does not exist"
How will you solve this problem?
A. Export a disk group from another host.
B. Export a disk group from the current host and import the disk group to another host.
C. If the disk group already exists on the exported host, import it to the current host.
D. Restore the configuration for the disk group from the backup.
-
Question 227:
You need to increase the size of an existing volume to 10 gigabytes. You also want to exclude storages on the controller c1 from being allocated. To meet the required goal, you execute the following command, but when executed, the command fails.
vxassist -g mydg1 growto vol1 10g \use_storage='noneof("Controller"="c1")'
What could be the possible cause for the failure?
A. You cannot exclude the c1 controller.
B. The size specified is smaller than the current size of the volume.
C. The growto parameter needs to be replaced by growby parameter.
D. The growto parameter needs to be replaced by maxby parameter.
-
Question 228:
You are writing the change documents for a procedure to relay a volume.
In which two cases is it necessary to specify a target plex for the "vxassist relayout" operation? (Each correct answer presents part of the solution. Select two.)
A. When a concatenated layout is being relaid to a mirror-stripe layout.
B. When the volume affected has plexes of differing layouts.
C. When a mirrored volume is being converted to RAID-5.
D. When a RAID-5 volume is being relaid as a mirrored volume.
E. When a volume with multiple mirrors is being relaid with only two plexes.
-
Question 229:
A DLP administrator needs to have the Email Prevent Server return inspected emails to the same MTA from which it receives the message. In which mode should the Email Prevent server be configured?
A. forward
B. reflect
C. mirror
D. trial
-
Question 230:
You have collected performance data from an e-commerce Oracle database using the vxstat command. You are creating a similar e-commerce Oracle database to serve as a backend for an e-commerce website. You also want to ensure optimal Online Transaction Processing (OLTP) throughput by balancing the I/O across as many disks as possible.
What should you do?
A. Create the database on a file system on a mirrored volume using all available disks.
B. Create the database on 2 separate file systems on a striped volume using all available disks.
C. Create the database on a file system on a striped volume using all available disks.
D. Create the database on a file system on a RAID-5 volume using all available disks.
Related Exams:
250-428
Administration of Symantec Endpoint Protection 14250-438
Administration of Symantec Data Loss Prevention 15250-440
Administration of Symantec PacketShaper 11.9.1250-441
Administration of Symantec Advanced Threat Protection 3.0250-445
Administration of Symantec Email Security.cloud (v1)250-447
Administration of Symantec Client Management Suite 8.5250-513
Administration of Symantec Data Loss Prevention 12250-556
Administration of Symantec ProxySG 6.7250-561
Endpoint Security Complete - Administration R1250-580
Endpoint Security Complete - R2 Technical Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Symantec exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 250-513 exam preparations and Symantec certification application, do not hesitate to visit our Vcedump.com to find your solutions here.