Exam Details
Exam Code
:250-513Exam Name
:Administration of Symantec Data Loss Prevention 12Certification
:Symantec CertificationsVendor
:SymantecTotal Questions
:305 Q&AsLast Updated
:Apr 12, 2025
Symantec Symantec Certifications 250-513 Questions & Answers
-
Question 231:
While you are working on Storage Foundation for DB2, you want to convert the DB2 containers by executing the qio_convertdbfiles
-
Question 232:
You are working on a Storage Foundation 5.0 server named Srv1 that has a disk group named vol1. You install another Storage Foundation 5.0 server named Srv2. You want to successfully move the disk group from Srv1 to Srv2. To initiate the movement, you stop all volumes in the disk group, and deport and move all disks to Srv2.
What should you do next?
A. Start the volumes in the disk group.
B. Format the disk group.
C. Recognize the disks using VxVM.
D. Create a new disk group.
-
Question 233:
A file system encounters an error during VxVM operations. The error "VxVM vxio WARMINIG V-5-0-144 Double failure condition detected on RAID-5 volume" is displayed in the file system. How should you resolve this error?
A. By correcting the hardware failure and recovering the volume using the vxrecover command.
B. By checking the underlying hardware to recover the desired path.
C. By creating a new log plex and attaching it with the volume to restore RAID-5 logging to a RAID-5 volume.
D. By rebooting the computer.
-
Question 234:
You need to provide storage space for database application, including permanent data, temporary space, and activity log data. You need to ensure that the storage space that you provide offers data protection against disk failures. Which storage techniques will you use? (Each correct answer presents part of the solution. Select two.)
A. Concatenated
B. RAID-0
C. RAID-1
D. RAID-5
E. RAID-1+0
-
Question 235:
An administrator implements a policy to block confidential data from being posted to Facebook. The policy generates incidents but allows the content to be posted.
Which action should the administrator take to resolve this issue?
A. turn off Trial mode
B. turn on default settings
C. enable Get Processing
D. enable ICAP.Allowhosts
-
Question 236:
Which server encrypts the message when using a Modify SMTP Message response rule?
A. Encryption Gateway
B. SMTP Prevent server
C. Network Monitor server
D. Enforce server
-
Question 237:
You are responsible for administering the Storage Foundation for Sybase server. You want to remove a mounted volume. What should you do first to ensure you are able to remove the mounted volume?
A. Remove the snapshot from the associated volume.
B. Recursively remove all plexes and subdisks.
C. Disassociate the snapshot from the associated volume.
D. Unmount the file system.
-
Question 238:
Which incidents appear in the Network Incident List report when the Network Prevent Action filter is set to Modified?
A. incidents in which confidential content was removed from the body of an SMTP email
B. incidents in which an SMTP email was changed to include one or more SMTP headers
C. incidents in which digital rights were applied to SMTP email attachments containing confidential information
D. incidents in which confidential attachments were removed from an SMTP email
-
Question 239:
An administrator needs to deploy a Symantec Data Loss Prevention solution that will monitor network traffic. Which traffic type is excluded from inspection when using the default configuration?
A. HTTP-get
B. NNTP
C. FTP-put
D. HTTP-post
-
Question 240:
Refer to the exhibit.
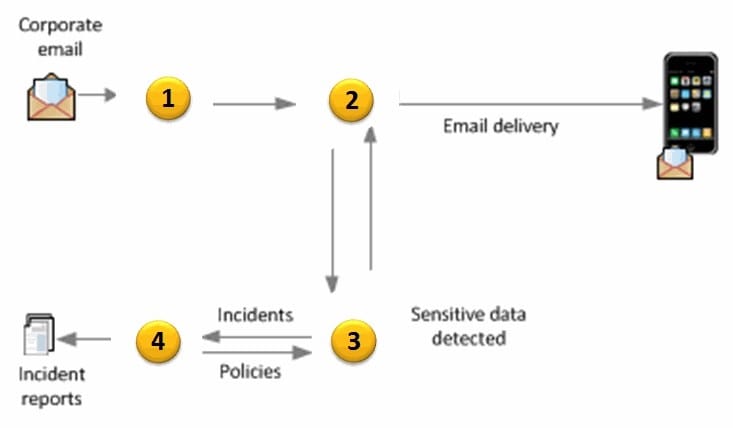
An administrator needs to implement a Mobile Email Monitor solution to inspect corporate emails on mobile devices. Where should the administrator place the web proxy?
A. 1
B. 2
C. 3
D. 4
Related Exams:
250-428
Administration of Symantec Endpoint Protection 14250-438
Administration of Symantec Data Loss Prevention 15250-440
Administration of Symantec PacketShaper 11.9.1250-441
Administration of Symantec Advanced Threat Protection 3.0250-445
Administration of Symantec Email Security.cloud (v1)250-447
Administration of Symantec Client Management Suite 8.5250-513
Administration of Symantec Data Loss Prevention 12250-556
Administration of Symantec ProxySG 6.7250-561
Endpoint Security Complete - Administration R1250-580
Endpoint Security Complete - R2 Technical Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Symantec exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 250-513 exam preparations and Symantec certification application, do not hesitate to visit our Vcedump.com to find your solutions here.