Exam Details
Exam Code
:300-710Exam Name
:Securing Networks with Cisco Firepower (SNCF)Certification
:CCNP SecurityVendor
:CiscoTotal Questions
:398 Q&AsLast Updated
:Apr 15, 2025
Cisco CCNP Security 300-710 Questions & Answers
-
Question 211:
An organization has a compliance requirement to protect servers from clients, however, the clients and servers all reside on the same Layer 3 network. Without readdressing IP subnets for clients or servers, how is segmentation achieved?
A. Change the IP addresses of the servers, while remaining on the same subnet.
B. Deploy a firewall in routed mode between the clients and servers.
C. Change the IP addresses of the clients, while remaining on the same subnet.
D. Deploy a firewall in transparent mode between the clients and servers.
-
Question 212:
Within an organization's high availability environment where both firewalls are passing traffic, traffic must be segmented based on which department it is destined for. Each department is situated on a different LAN. What must be configured to meet these requirements?
A. redundant interfaces
B. span EtherChannel clustering
C. high availability active/standby firewalls
D. multi-instance firewalls
-
Question 213:
An engineer is restoring a Cisco FTD configuration from a remote backup using the command restore remote-manager-backup location 1.1.1.1 admin /volume/home/admin BACKUP_Cisc394602314.zip on a Cisco FMG. After connecting to the repository, an error occurred that prevents the FTD device from accepting the backup file. What is the problem?
A. The backup file is not in .cfg format.
B. The backup file is too large for the Cisco FTD device
C. The backup file extension was changed from .tar to .zip
D. The backup file was not enabled prior to being applied
-
Question 214:
Refer to the exhibit.
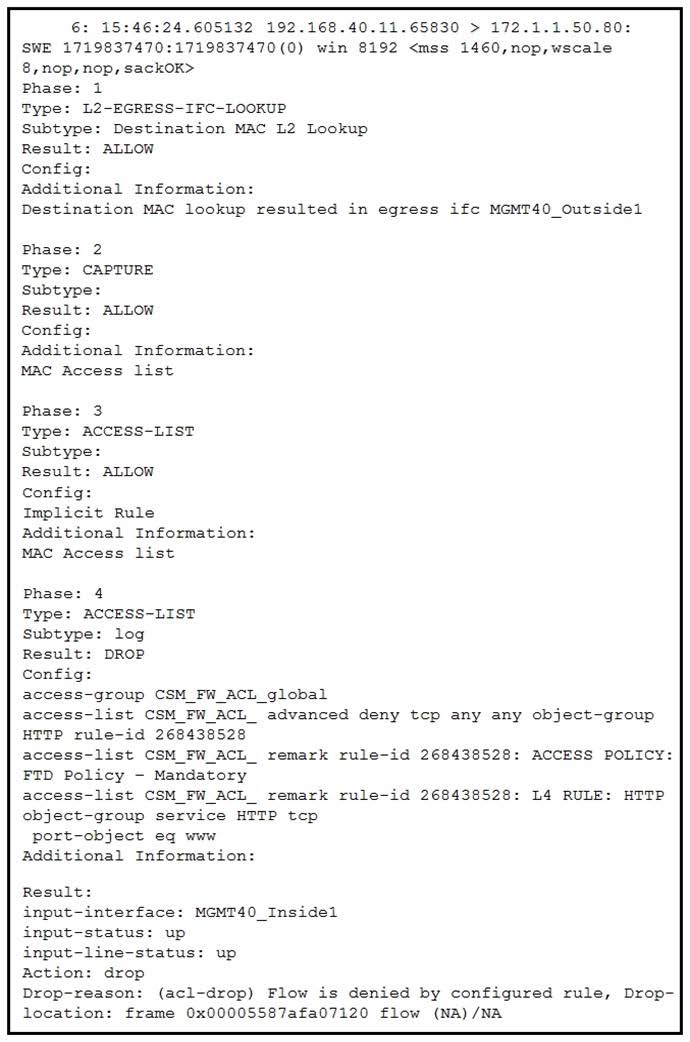
What must be done to fix access to this website while preventing the same communication to all other websites?
A. Create an intrusion policy rule to have Snort allow port 80 to only 172.1.1 50.
B. Create an access control policy rule to allow port 80 to only 172.1.1 50.
C. Create an intrusion policy rule to have Snort allow port 443 to only 172.1.1.50
D. Create an access control policy rule to allow port 443 to only 172.1.1 50
-
Question 215:
An engineer currently has a Cisco FTD device registered to the Cisco FMC and is assigned the address of 10 10.50.12. The organization is upgrading the addressing schemes and there is a requirement to convert the addresses to a format that provides an adequate amount of addresses on the network What should the engineer do to ensure that the new addressing takes effect and can be used for the Cisco FTD to Cisco FMC connection?
A. Delete and reregister the device to Cisco FMC
B. Update the IP addresses from IFV4 to IPv6 without deleting the device from Cisco FMC
C. Format and reregister the device to Cisco FMC.
D. Cisco FMC does not support devices that use IPv4 IP addresses.
-
Question 216:
An organization is using a Cisco FTD and Cisco ISE to perform identity-based access controls. A network administrator is analyzing the Cisco FTD events and notices that unknown user traffic is being allowed through the firewall. How should this be addressed to block the traffic while allowing legitimate user traffic?
A. Modify lhe Cisco ISE authorization policy to deny this access to the user.
B. Modify Cisco ISE to send only legitimate usernames to the Cisco FTD.
C. Add the unknown user in the Access Control Policy in Cisco FTD.
D. Add the unknown user in the Malware and File Policy in Cisco FTD.
-
Question 217:
A network administrator needs to create a policy on Cisco Firepower to fast-path traffic to avoid Layer 7 inspection. The rate at which traffic is inspected must be optimized. What must be done to achieve this goal?
A. Enable lhe FXOS for multi-instance.
B. Configure a prefilter policy.
C. Configure modular policy framework.
D. Disable TCP inspection.
-
Question 218:
An engineer is building a new access control policy using Cisco FMC. The policy must inspect a unique IPS policy as well as log rule matching. Which action must be taken to meet these requirements?
A. Configure an IPS policy and enable per-rule logging.
B. Disable the default IPS policy and enable global logging.
C. Configure an IPS policy and enable global logging.
D. Disable the default IPS policy and enable per-rule logging.
-
Question 219:
Which two conditions must be met to enable high availability between two Cisco FTD devices? (Choose two.)
A. same flash memory size
B. same NTP configuration
C. same DHCP/PPoE configuration
D. same host name
E. same number of interfaces
-
Question 220:
A network administrator notices that inspection has been interrupted on all non-managed interfaces of a device. What is the cause of this?
A. The value of the highest MTU assigned to any non-management interface was changed.
B. The value of the highest MSS assigned to any non-management interface was changed.
C. A passive interface was associated with a security zone.
D. Multiple inline interface pairs were added to the same inline interface.
Related Exams:
300-710
Securing Networks with Cisco Firepower (SNCF)300-715
Implementing and Configuring Cisco Identity Services Engine (SISE)300-720
Securing Email with Cisco Email Security Appliance (SESA)300-725
Securing the Web with Cisco Web Security Appliance (SWSA)300-730
Implementing Secure Solutions with Virtual Private Networks (SVPN)300-735
Automating and Programming Cisco Security Solutions (SAUTO)350-701
Implementing and Operating Cisco Security Core Technologies (SCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 300-710 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.