Exam Details
Exam Code
:300-710Exam Name
:Securing Networks with Cisco Firepower (SNCF)Certification
:CCNP SecurityVendor
:CiscoTotal Questions
:398 Q&AsLast Updated
:Apr 15, 2025
Cisco CCNP Security 300-710 Questions & Answers
-
Question 241:
A network engineer is logged into the Cisco AMP for Endpoints console and sees a malicious verdict for an identified SHA-256 hash. Which configuration is needed to mitigate this threat?
A. Add the hash to the simple custom deletion list.
B. Use regular expressions to block the malicious file.
C. Enable a personal firewall in the infected endpoint.
D. Add the hash from the infected endpoint to the network block list.
-
Question 242:
A network engineer implements a new Cisco Firepower device on the network to take advantage of its intrusion detection functionality. There is a requirement to analyze the traffic going across the device, alert on any malicious traffic, and appear as a bump in the wire. How should this be implemented?
A. Specify the BVl IP address as the default gateway for connected devices.
B. Enable routing on the Cisco Firepower
C. Add an IP address to the physical Cisco Firepower interfaces.
D. Configure a bridge group in transparent mode.
-
Question 243:
An engineer is troubleshooting a device that cannot connect to a web server. The connection is initiated from the Cisco FTD inside interface and attempting to reach 10.0.1.100 over the non-standard port of 9443. The host the engineer is attempting the connection from is at the IP address of 10.20.10.20. In order to determine what is happening to the packets on the network, the engineer decides to use the FTD packet capture tool.
Which capture configuration should be used to gather the information needed to troubleshoot the issue?
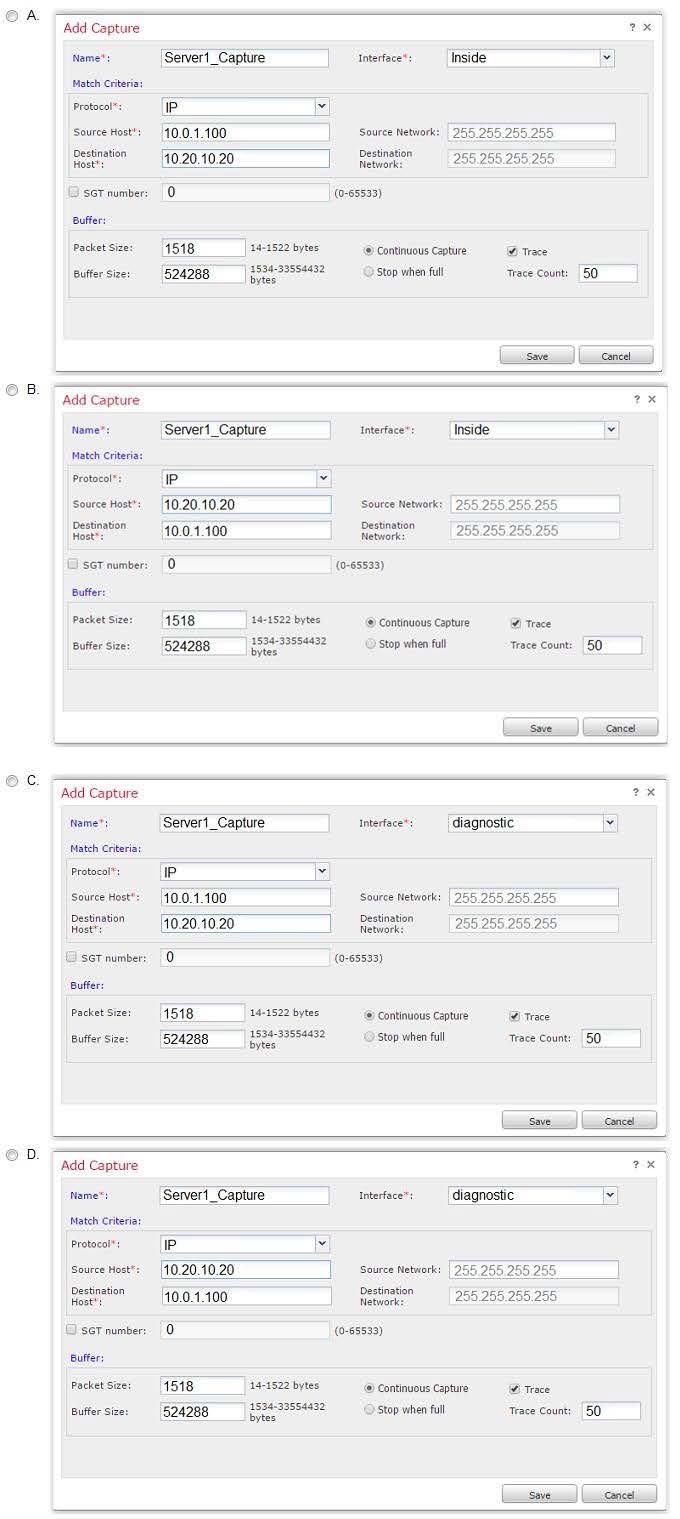
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 244:
A network engineer is receiving reports of users randomly getting disconnected from their corporate applications which traverse the data center FTD appliance. Network monitoring tools show that the FTD appliance utilization is peaking above 90% of total capacity. What must be done in order to further analyze this issue?
A. Use the Packet Export feature to save data onto external drives.
B. Use the Packet Capture feature to collect real-time network traffic.
C. Use the Packet Tracer feature for traffic policy analysis.
D. Use the Packet Analysis feature for capturing network data.
-
Question 245:
An administrator is attempting to remotely log into a switch in the data center using SSH and is unable to connect. How does the administrator confirm that traffic is reaching the firewall?
A. by performing a packet capture on the firewall
B. by attempting to access it from a different workstation
C. by running Wireshark on the administrator's PC
D. by running a packet tracer on the firewall
-
Question 246:
IT management is asking the network engineer to provide high-level summary statistics of the Cisco FTD appliance in the network. The business is approaching a peak season so the need to maintain business uptime is high. Which report type should be used to gather this information?
A. Risk Report
B. SNMP Report
C. Standard Report
D. Malware Report
-
Question 247:
With a recent summer time change, system logs are showing activity that occurred to be an hour behind real time. Which action should be taken to resolve this issue?
A. Manually adjust the time to the correct hour on all managed devices.
B. Configure the system clock settings to use NTP with Daylight Savings checked.
C. Configure the system clock settings to use NTP.
D. Manually adjust the time to the correct hour on the Cisco FMC.
-
Question 248:
An engineer configures a network discovery policy on Cisco FMC. Upon configuration, it is noticed that excessive and misleading events are filling the database and overloading the Cisco FMC. A monitored NAT device is executing multiple updates of its operating system in a short period of time. What configuration change must be made to alleviate this issue?
A. Exclude load balancers and NAT devices.
B. Leave default networks.
C. Increase the number of entries on the NAT device.
D. Change the method to TCP/SYN.
-
Question 249:
A network administrator is configuring SNORT inspection policies and is seeing failed deployment messages in Cisco FMC. What information should the administrator generate for Cisco TAC to help troubleshoot?
A. A "troubleshoot" file for the device in question.
B. A "show tech" file for the device in question.
C. A "troubleshoot" file for the Cisco FMC.
D. A "show tech" for the Cisco FMC.
-
Question 250:
An engineer is attempting to add a new FTD device to their FMC behind a NAT device with a NAT ID of ACME001 and a password of Cisco0391521107.
Which command set must be used in order to accomplish this?
A. configure manager add
ACME001 B. configure manager add ACME001
C. configure manager add
ACME001 D. configure manager add DONTRESOLVE
AMCE001
Related Exams:
300-710
Securing Networks with Cisco Firepower (SNCF)300-715
Implementing and Configuring Cisco Identity Services Engine (SISE)300-720
Securing Email with Cisco Email Security Appliance (SESA)300-725
Securing the Web with Cisco Web Security Appliance (SWSA)300-730
Implementing Secure Solutions with Virtual Private Networks (SVPN)300-735
Automating and Programming Cisco Security Solutions (SAUTO)350-701
Implementing and Operating Cisco Security Core Technologies (SCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 300-710 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.