Exam Details
Exam Code
:300-710Exam Name
:Securing Networks with Cisco Firepower (SNCF)Certification
:CCNP SecurityVendor
:CiscoTotal Questions
:398 Q&AsLast Updated
:Apr 07, 2025
Cisco CCNP Security 300-710 Questions & Answers
-
Question 291:
An engineer is configuring a Cisco FTD appliance in IPS-only mode and needs to utilize fail-to-wire interfaces. Which interface mode should be used to meet these requirements?
A. passive
B. routed
C. transparent
D. inline set
-
Question 292:
An engineer is configuring a second Cisco FMC as a standby device but is unable to register with the active unit. What is causing this issue?
A. The primary FMC currently has devices connected to it.
B. The code versions running on the Cisco FMC devices are different.
C. The licensing purchased does not include high availability
D. There is only 10Mbps of bandwidth between the two devices.
-
Question 293:
Administrator is attempting to remotely log into a switch in the data center using SSH and is unable to connect. How does the administrator confirm that traffic is reaching the firewall?
A. by running Wireshark on the administrator's PC.
B. by performing a packet capture on the firewall.
C. by running a packet tracer on the firewall.
D. by attempting to access it from a different workstation.
-
Question 294:
A security engineer is configuring an Access Control Policy for multiple branch locations. These locations share a common rule set and utilize a network object called INSIDE_NET which contains the locally significant internal network subnets
at each location.
What technique will retain the policy consistency at each location but allow only the locally significant network subnet within the applicable rules?
A. utilizing policy inheritance
B. utilizing a dynamic ACP that updates from Cisco Talos Eba
C. creating a unique ACP per device.
D. creating an ACP with an INSIDE_NET network object and object overrides.
-
Question 295:
An engineer is troubleshooting application failures through a FTD deployment. While using the FMC CLI, it has been determined that the traffic in question is not matching the desired policy. What should be done to correct this?
A. Use the system support firewall-engine-debug command to determine which rules the traffic matching and modify the rule accordingly.
B. Use the system support application-identification-debug command to determine which rules the traffic matching and modify the rule accordingly.
C. Use the system support firewall-engine-dump-user-f density-data command to change the policy and allow the application through the firewall.
D. Use the system support network-options command to fine tune the policy.
-
Question 296:
An engineer currently has a Cisco FTD device registered to the Cisco FMC and is assigned the address of 10.10.50.12. The organization is upgrading the addressing schemes and there is a requirement to convert the addresses to a format
that provides an adequate amount of addresses on the network.
What should the engineer do to ensure that the new addressing takes effect and can be used for the Cisco FTD to Cisco FMC connection?
A. Delete and register the device to Cisco FMC.
B. Update the IP addresses from IPV4 to IPV6 without deleting the device from cisco FMC.
C. Format and register the device to Cisco FMC.
D. Cisco FMC does not support devices that use IPv4 IP addresses.
-
Question 297:
An engineer is implementing Cisco FTD in the network and is determining which Firepower mode to use. The organization needs to have multiple virtual Firepower devices working separately inside of the FTD appliance to provide traffic
segmentation.
Which deployment mode should be configured in the Cisco Firepower Management Console to support these requirements?
A. Multiple Deployment
B. single-context
C. Single deployment
D. multi-instance
-
Question 298:
An Engineer has been asked to show application usages automatically on a monthly basis and send the information to management. What mechanism should be used to accomplish this task?
A. Event viewer
B. Reports
C. dashboards
D. context explorer
-
Question 299:
Refer to the exhibit.
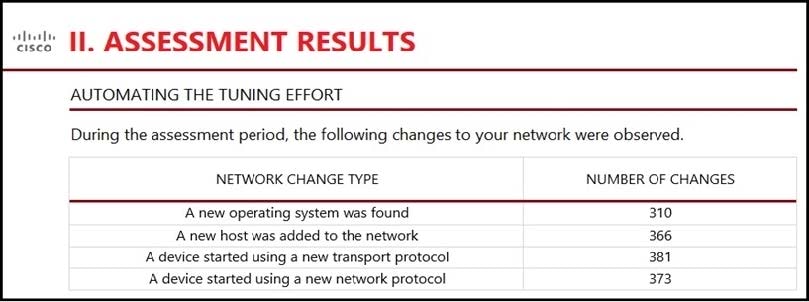
An engineer is analyzing the Attacks Risk Report and finds that there are over 300 instances of new operating systems being seen on the network. How is the Firepower configuration updated to protect these new operating systems?
A. Cisco Firepower Automatically updates the policies.
B. The administrator requests a Remediation Recommendation Report from Cisco Firepower
C. Cisco Firepower gives recommendation to update the policies
D. The administrator manually updates the policies.
-
Question 300:
After using Firepower for some time and learning about how it interacts with the network, an administrator is trying to correlate malicious activity with a user. Which widget should be configured to provide this visibility on the Cisco Firepower Dashboards?
A. Custom analysis.
B. Current Status
C. Current Sessions
D. Correlation Events
Related Exams:
300-710
Securing Networks with Cisco Firepower (SNCF)300-715
Implementing and Configuring Cisco Identity Services Engine (SISE)300-720
Securing Email with Cisco Email Security Appliance (SESA)300-725
Securing the Web with Cisco Web Security Appliance (SWSA)300-730
Implementing Secure Solutions with Virtual Private Networks (SVPN)300-735
Automating and Programming Cisco Security Solutions (SAUTO)350-701
Implementing and Operating Cisco Security Core Technologies (SCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 300-710 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.