Exam Details
Exam Code
:300-710Exam Name
:Securing Networks with Cisco Firepower (SNCF)Certification
:CCNP SecurityVendor
:CiscoTotal Questions
:398 Q&AsLast Updated
:Mar 30, 2025
Cisco CCNP Security 300-710 Questions & Answers
-
Question 61:
A security engineer must create a malware and file policy on a Cisco Secure Firewall Threat Defense device. The solution must ensure that PDF, DOCX, and XLSX files are not sent to Cisco Secure Malware Analytics. What must be configured to meet the requirements?
A. Spero analysis
B. local malware analysis
C. capacity handling
D. dynamic analysis
-
Question 62:
A security engineer is deploying Cisco Secure Endpoint to detect a zero day malware attack with an SHA-256 hash of 47ea931f3e9dc23ec0b0885a80663e30ea013d493f8e88224b570a0464084628. What must be configured in Cisco Secure Endpoint to enable the application to take action based on this hash?
A. access control rule
B. correlation policy
C. transform set
D. custom detection list
-
Question 63:
A company is deploying AMP private cloud. The AMP private cloud instance has already been deployed by the server administrator. The server administrator provided the hostname of the private cloud instance to the network engineer via email. What additional information does the network engineer require from the server administrator to be able to make the connection to the AMP private cloud in Cisco FMC?
A. SSL certificate for the AMP private cloud instance
B. Username and password to the AMP private cloud instance
C. IP address and port number for the connection proxy
D. Internet access for the AMP private cloud to reach the AMP public cloud
-
Question 64:
A network engineer is planning on replacing an Active/Standby pair of physical Cisco Secure Firewall ASAs with a pair of Cisco Secure Firewall Threat Defense Virtual appliances. Which two virtual environments support the current High Availability configuration? (Choose two.)
A. ESXi
B. Azure
C. Openstack
D. KVM
E. AWS
-
Question 65:
Network users are experiencing Intermittent issues with internet access. An engineer ident med mat the issue Is being caused by NAT exhaustion. How must the engineer change the dynamic NAT configuration to provide internet access for more users without running out of resources?
A. Define an additional static NAT for the network object in use.
B. Configure fallthrough to interface PAT on 'he Advanced tab.
C. Convert the dynamic auto NAT rule to dynamic manual NAT.
D. Add an identity NAT rule to handle the overflow of users.
-
Question 66:
Refer to the exhibit.
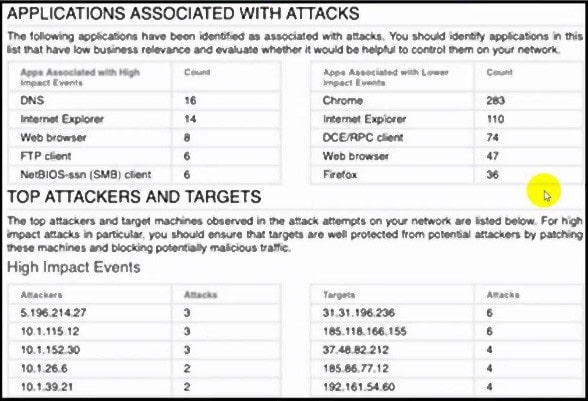
A security engineer must improve security in an organization and is producing a risk mitigation strategy to present to management for approval. Which action must the security engineer take based on this Attacks Risk Report?
A. Block NetBIOS.
B. Inspect TCP port 80 traffic.
C. Block Internet Explorer.
D. Inspect DNS traffic.
-
Question 67:
A network administrator reviews the attack risk report and notices several low-impact attacks. What does this type of attack indicate?
A. All attacks are listed as low until manually recategorized.
B. The host is not vulnerable to those attacks.
C. The host is not within the administrator's environment.
D. The attacks are not dangerous to the network.
-
Question 68:
An engineer has been tasked with performing an audit of network objects to determine which objects are duplicated across the various firewall models (Cisco Secure Firewall Threat Defense, Cisco Secure Firewall ASA, and Meraki MX Series) deployed throughout the company. Which tool will assist the engineer in performing that audit?
A. Cisco Firepower Device Manager
B. Cisco Defense Orchestrator
C. Cisco Secure Firewall Management Center
D. Cisco SecureX
-
Question 69:
The security engineer reviews the syslog server events of an organization and sees many outbound connections to malicious sites initiated from hosts running Cisco Secure Endpoint. The hosts are on a separate network from the Cisco FTD device. Which action blocks the connections?
A. Modify the policy on Cisco Secure Endpoint to enable DFC.
B. Modify the access control policy on the Cisco FMC to block malicious outbound connections
C. Add the IP addresses of the malicious sites to the access control policy on the Cisco FMC
D. Add a Cisco Secure Endpoint policy with the Tetra and Spero engines enabled
-
Question 70:
A network administrator must create an EtherChannel Interface on a new Cisco Firepower 9300 appliance registered with an FMC tor high availability. Where must the administrator create the EtherChannel interface?
A. FMC CLI
B. FTD CLI
C. FXOS CLI
D. FMC GUI
Related Exams:
300-710
Securing Networks with Cisco Firepower (SNCF)300-715
Implementing and Configuring Cisco Identity Services Engine (SISE)300-720
Securing Email with Cisco Email Security Appliance (SESA)300-725
Securing the Web with Cisco Web Security Appliance (SWSA)300-730
Implementing Secure Solutions with Virtual Private Networks (SVPN)300-735
Automating and Programming Cisco Security Solutions (SAUTO)350-701
Implementing and Operating Cisco Security Core Technologies (SCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 300-710 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.