Exam Details
Exam Code
:312-38Exam Name
:EC-Council Certified Network Defender (CND)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:653 Q&AsLast Updated
:Apr 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-38 Questions & Answers
-
Question 191:
James is working as a Network Administrator in a reputed company situated in California. He is monitoring his network traffic with the help of Wireshark. He wants to check and analyze the traffic against a PING sweep attack. Which of the following Wireshark filters will he use?
A. Icmp.type==8 or icmp.type==16
B. icmp.type==8 or icmp.type==0
C. icmp.type==8 and icmp.type==0
D. Icmp.type==0 and icmp.type==16
-
Question 192:
Management wants to bring their organization into compliance with the ISO standard for information security risk management. Which ISO standard will management decide to implement?
A. ISO/IEC 27005
B. ISO/IEC 27006
C. ISO/IEC 27002
D. ISO/IEC 27004
-
Question 193:
Which of the following systems includes an independent NAS Head and multiple storage arrays?
A. FreeNAS
B. None of these
C. Gateway NAS System
D. Integrated NAS System
-
Question 194:
You are monitoring your network traffic with the Wireshark utility and noticed that your network is experiencing a large amount of traffic from a certain region. You suspect a DoS incident on the network. What will be your first reaction as a first responder?
A. Avoid Fear, Uncertainty and Doubt
B. Communicate the incident
C. Make an initial assessment
D. Disable Virus Protection
-
Question 195:
The GMT enterprise is working on their internet and web usage policies. GMT would like to control internet bandwidth consumption by employees. Which group of policies would this belong to?
A. Enterprise Information Security Policy
B. Network Services Specific Security Policy
C. Issue Specific Security Policy
D. System Specific Security Policy
-
Question 196:
Which of the following intrusion detection techniques observes the network for abnormal usage patterns by determining the performance parameters for regular activities and monitoring for actions beyond the normal parameters?
A. Statistical anomaly detection
B. Signature/Pattern matching
C. None of these
D. Stateful protocol analysis
-
Question 197:
An administrator wants to monitor and inspect large amounts of traffic and detect unauthorized attempts from inside the organization, with the help of an IDS. They are not able to recognize the exact location to deploy the IDS sensor. Can you help him spot the location where the IDS sensor should be placed?
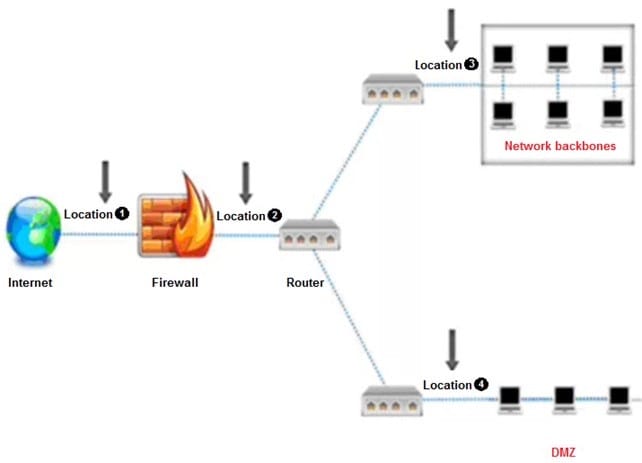
A. Location 1
B. Location 2
C. Location 3
D. Location 4
-
Question 198:
Steven's company has recently grown from 5 employees to over 50. Every workstation has a public IP address and navigated to the Internet with little to no protection. Steven wants to use a firewall. He also wants IP addresses to be private addresses, to prevent public Internet devices direct access to them. What should Steven implement on the firewall to ensure this happens?
A. Steven should use Open Shortest Path First (OSPF).
B. Steven should enable Network Address Translation (NAT).
C. Steven should use a Demilitarized Zone (DMZ).
D. Steven should use IPsec.
-
Question 199:
Stephanie is currently setting up email security so all company data is secured when passed through email. Stephanie first sets up encryption to make sure that a specific user's email is protected. Next, she needs to ensure that the incoming and the outgoing mail has not been modified or altered using digital signatures. What is Stephanie working on?
A. Usability
B. Confidentiality
C. Availability
D. Data Integrity
-
Question 200:
Which of the following interfaces uses hot plugging technique to replace computer components without the need to shut down the system?
A. SATA
B. SCSI
C. IDE
D. SDRAM
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-38 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.