Exam Details
Exam Code
:312-38Exam Name
:EC-Council Certified Network Defender (CND)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:653 Q&AsLast Updated
:Apr 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-38 Questions & Answers
-
Question 211:
Daniel who works as a network administrator has just deployed an IDS in his organization's network. He wants to calculate the False Positive rate for his implementation. Which of the following formulas will he use, to calculate the False Positive rate?
A. False Negative/True Negative+True Positive
B. False Positive/False Positive+True Negative
C. True Negative/False Negative+True Positive
D. False Negative/False Negative+True Positive
-
Question 212:
The SNMP contains various commands that reduce the burden on the network administrators. Which of the following commands is used by SNMP agents to notify SNMP managers about an event occurring in the network?
A. INFORM
B. RESPONSE
C. TRAPS
D. SET
-
Question 213:
As a network administrator, you have implemented WPA2 encryption in your corporate wireless network. The WPA2's __________ integrity check mechanism provides security against a replay attack.
A. CBC-MAC
B. CRC-MAC
C. CBC-32
D. CRC-32
-
Question 214:
Paul is a network security technician working on a contract for a laptop manufacturing company in Chicago. He has focused primarily on securing network devices, firewalls, and traffic traversing in and out of the network. He just finished setting up a server a gateway between the internal private network and the outside public network. This server will act as a proxy, limited amount of services, and will filter packets. What is this type of server called?
A. Session layer firewall.
B. SOCKS host.
C. Bastion host.
D. Edge transport server.
-
Question 215:
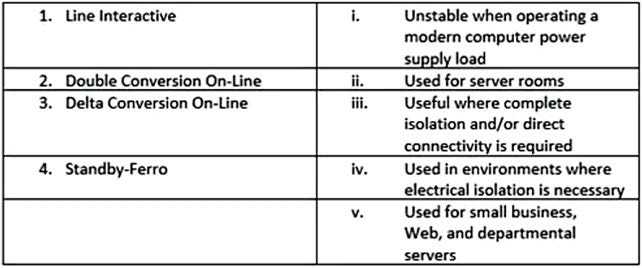
Your company is planning to use an uninterruptible power supply (UPS) to avoid damage from power fluctuations. As a network administrator, you need to suggest an appropriate UPS solution suitable for specific resources or conditions. Match the type of UPS with the use and advantage:
A. 1-i,2-iv,3-ii,4-v
B. 1-v,2-iii,3-i,4-ii
C. 1-ii,2-iv,3-iii,4-i
D. 1-iii,2-iv,3-v,4-iv
-
Question 216:
John has successfully remediated the vulnerability of an internal application that could have caused a threat to the network. He is scanning the application for the existence of a remediated vulnerability, this process is called a __________ and it has to adhere to the __________.
A. Mitigation, Security policies
B. Verification, Security Policies
C. Vulnerability scanning, Risk Analysis
D. Risk analysis, Risk matrix
-
Question 217:
Which filter to locate unusual ICMP request an Analyst can use in order to detect a ICMP probes from the attacker to a target OS looking for the response to perform ICMP based fingerprinting?
A. (icmp.type==9 andand ((!(icmp.code==9))
B. (icmp.type==8 andand ((!(icmp.code==8))
C. (icmp.type==12) | | (icmp.type==15| |(icmp.type==17)
D. (icmp.type==14) | | (icmp.type==15| |(icmp.type==17)
-
Question 218:
You are using Wireshark to monitor your network traffic and you see a lot of packages with the FIN, PUSH and URG flags activated; what can you infer about this behavior?
A. The Layer 3 Controls are activated in the Switches
B. The Spanning Tree Protocol is activated in the Switches
C. One NIC is broadcasting erroneous traffic
D. An attacker is running a XMAS scan against the network
-
Question 219:
The Circuit-level gateway firewall technology functions at which of the following OSI layer?
A. Transport layer
B. Data-link layer
C. Session layer
D. Network layer
-
Question 220:
Individuals in the organization using system resources in a way that violates acceptable usage policies indicates which of the following security incident(s):
A. Unauthorized Access
B. Improper Usage
C. Denial-of-Service (DoS)
D. Malicious Code
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-38 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.