Exam Details
Exam Code
:312-38Exam Name
:EC-Council Certified Network Defender (CND)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:653 Q&AsLast Updated
:Apr 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-38 Questions & Answers
-
Question 221:
Larry is a network administrator working for a manufacturing company in Detroit. Larry is responsible for the entire company's network which consists of 300 workstations and 25 servers. After using a hosted email service for a year, the company wants to cut back on costs and bring the email control internal. Larry likes this idea because it will give him more control over email. Larry wants to purchase a server for email but he does not want the server to be on the internal network because this might cause security risks. He decides to place the email server on the outside of the company's internal firewall. There is another firewall connected directly to the Internet that will protect some traffic from accessing the email server; the server will essentially be place between the two firewalls. What logical area is Larry going to place the new email server into?
A. He is going to place the server in a Demilitarized Zone (DMZ).
B. He will put the email server in an IPSec zone.
C. For security reasons, Larry is going to place the email server in the company's Logical Buffer Zone (LBZ).
D. Larry is going to put the email server in a hot-server zone.
-
Question 222:
Smith is an IT technician that has been appointed to his company's network vulnerability assessment team. He is the only IT employee on the team. The other team members include employees from Accounting, Management, Shipping, and Marketing. Smith and the team members are having their first meeting to discuss how they will proceed. What is the first step they should do to create the network vulnerability assessment plan?
A. Their first step is the acquisition of required documents, reviewing of security policies and compliance.
B. Their first step is to create an initial Executive report to show the management team.
C. Their first step is to make a hypothesis of what their final findings will be.
D. Their first step is to analyze the data they have currently gathered from the company or interviews.
-
Question 223:
A local bank wants to protect their card holder data. The bank should comply with the __________ standard to ensure the security of card holder data.
A. PCI DSS
B. SOX
C. HIPAA
D. ISEC
-
Question 224:
Ross manages 30 employees and only 25 computers in the organization. The network the company uses is a peer-to-peer. Ross configures access control measures allowing the employees to set their own control measures for their files and folders. Which access control did Ross implement?
A. Mandatory access control
B. Non-discretionary access control
C. Discretionary access control
D. Role-based access control
-
Question 225:
Fred is a network technician working for Johnson Services, a temporary employment agency in Boston. Johnson Services has three remote offices in New England and the headquarters in Boston where Fred works. The company relies on a number of customized applications to perform daily tasks and unfortunately these applications require users to be local administrators. Because of this, Fred's supervisor wants to implement tighter security measures in other areas to compensate for the inherent risks in making those users local admins. Fred's boss wants a solution that will be placed on all computers throughout the company and monitored by Fred. This solution will gather information on all network traffic to and from the local computers without actually affecting the traffic. What type of solution does Fred's boss want to implement?
A. Fred's boss wants Fred to monitor a NIPS system.
B. Fred's boss wants to implement a HIDS solution.
C. Fred's boss wants a NIDS implementation.
D. Fred's boss wants to implement a HIPS solution.
-
Question 226:
Which of the following can be used to suppress fire from Class K sources?
A. Water
B. Carbon dioxide
C. Foam
D. Dry Chemical
-
Question 227:
Match the following NIST security life cycle components with their activities:
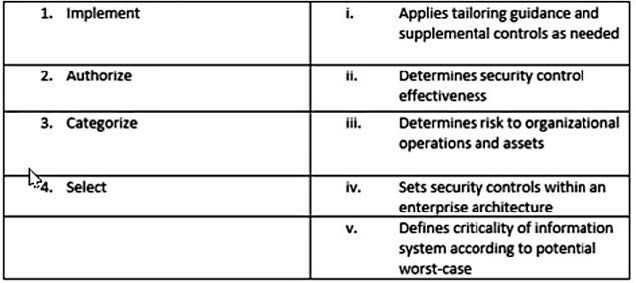
A. 1-iv, 2- iii,3-v,4-i
B. 1-ii,2-i,3-v,4-iv
C. 1-i,2-v,3-iii,4-ii
D. 1-iii,2-iv,3-v,4-i
-
Question 228:
What is the correct order of activities that a IDS is supposed to attempt in order of detect an intrusion?
A. Prevention, Intrusion Monitoring, intrusion Detection, Response
B. Intrusion Detection, Response, Prevention, Intrusion Monitoring
C. Intrusion Monitoring, Intrusion Detection, Response, Prevention
D. Prevention, intrusion Detection, Response, Intrusion Monitoring
-
Question 229:
Daniel is giving training on designing and implementing a security policy in the organization. He is explaining the hierarchy of the security policy which demonstrates how policies are drafted, designed and implemented. What is the correct hierarchy for a security policy implementation?
A. Procedures, Policies, Laws, Standards and Regulations
B. Laws, Regulations, Policies, Standards and Procedures
C. Regulations, Policies, Laws, Standards and Procedures
D. Laws, Policies, Regulations, Procedures and Standards
-
Question 230:
The _______ protocol works in the network layer and is responsible for handling the error codes during the delivery of packets. This protocol is also responsible for providing communication in the TCP/IP stack.
A. RARP
B. ICMP
C. ARP
D. DHCP
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-38 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.