Exam Details
Exam Code
:312-39Exam Name
:EC-Council Certified SOC Analyst (CSA)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:100 Q&AsLast Updated
:Apr 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-39 Questions & Answers
-
Question 1:
Which of the following attack can be eradicated by converting all non-alphanumeric characters to HTML character entities before displaying the user input in search engines and forums?
A. Broken Access Control Attacks
B. Web Services Attacks
C. XSS Attacks
D. Session Management Attacks
-
Question 2:
Which attack works like a dictionary attack, but adds some numbers and symbols to the words from the dictionary and tries to crack the password?
A. Hybrid Attack
B. Bruteforce Attack
C. Rainbow Table Attack
D. Birthday Attack
-
Question 3:
Emmanuel is working as a SOC analyst in a company named Tobey Tech. The manager of Tobey Tech recently recruited an Incident Response Team (IRT) for his company. In the process of collaboration with the IRT, Emmanuel just escalated an incident to the IRT.
What is the first step that the IRT will do to the incident escalated by Emmanuel?
A. Incident Analysis and Validation
B. Incident Recording
C. Incident Classification
D. Incident Prioritization
-
Question 4:
Identify the HTTP status codes that represents the server error.
A. 2XX
B. 4XX
C. 1XX
D. 5XX
-
Question 5:
Jony, a security analyst, while monitoring IIS logs, identified events shown in the figure below.
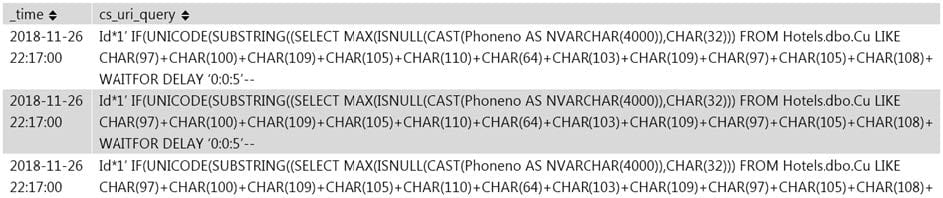
What does this event log indicate?
A. Parameter Tampering Attack
B. XSS Attack
C. Directory Traversal Attack
D. SQL Injection Attack
-
Question 6:
David is a SOC analyst in Karen Tech. One day an attack is initiated by the intruders but David was not able to find any suspicious events. This type of incident is categorized into __________?
A. True Positive Incidents
B. False positive Incidents
C. True Negative Incidents
D. False Negative Incidents
-
Question 7:
Which of the following service provides phishing protection and content filtering to manage the Internet experience on and off your network with the acceptable use or compliance policies?
A. Apility.io
B. Malstrom
C. OpenDNS
D. I-Blocklist
-
Question 8:
InfoSystem LLC, a US-based company, is establishing an in-house SOC. John has been given the responsibility to finalize strategy, policies, and procedures for the SOC. Identify the job role of John.
A. Security Analyst
-
Question 9:
If the SIEM generates the following four alerts at the same time:
I. Firewall blocking traffic from getting into the network alerts
II. SQL injection attempt alerts
III. Data deletion attempt alerts
IV.
Brute-force attempt alerts
Which alert should be given least priority as per effective alert triaging?
A.
III
B.
IV
C.
II
D.
I
-
Question 10:
Which of the following threat intelligence helps cyber security professionals such as security operations managers, network operations center and incident responders to understand how the adversaries are expected to perform the attack on the organization, and the technical capabilities and goals of the attackers along with the attack vectors?
A. Analytical Threat Intelligence
B. Operational Threat Intelligence
C. Strategic Threat Intelligence
D. Tactical Threat Intelligence
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-39 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.